Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Last updated 26 abril 2025

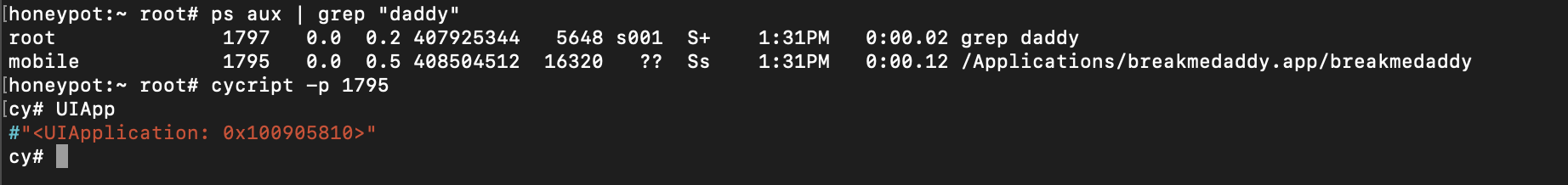
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

Advanced Apple Debugging & Reverse Engineering (3rd Edition) - 2018
Reverse Engineering x64 for Beginners - Windows - Checkmate

Mastering Reverse Engineering
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I

Reverse Engineering Coin Hunt World's Binary Protocol, NCC Group Research Blog

HACKER SUMMER CAMP 2023 GUIDES — Part Nine: DEFCON 31, by DCG 201

Reverse Engineering of a Not-so-Secure IoT Device

2022-2023 College Catalog by Honolulu Community College - Issuu
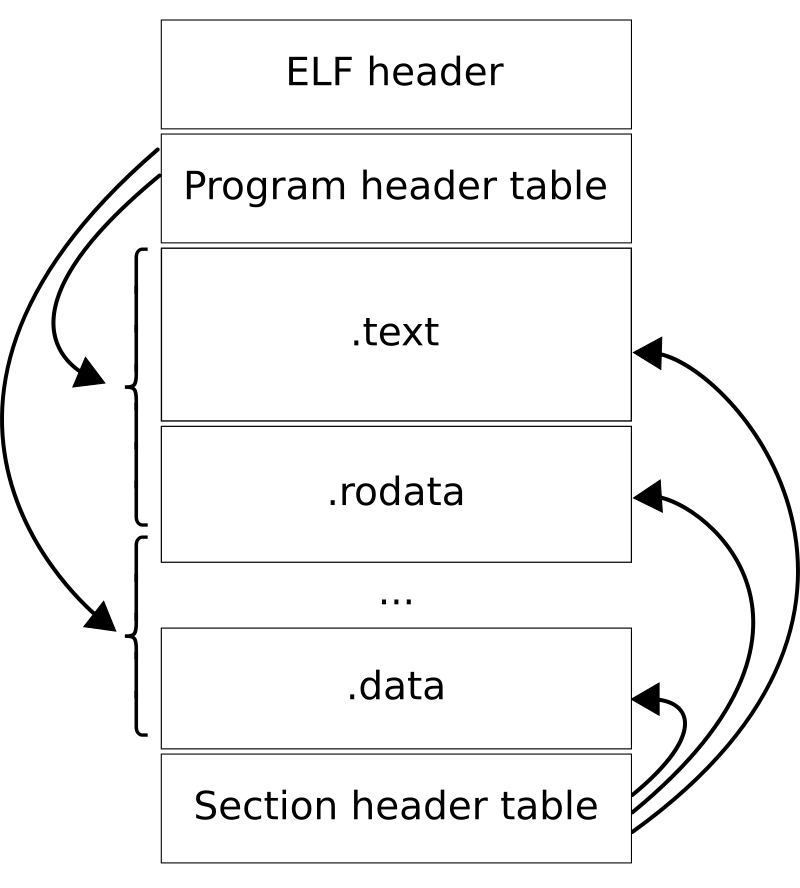
Executable and Linkable Format - Wikipedia
Access Our Reverse Engineering
Recomendado para você
-
rbx gum discord|Búsqueda de TikTok26 abril 2025
-
LilyGia on FreshCut26 abril 2025
-
roblox-api · GitHub Topics · GitHub26 abril 2025
-
 Discuss Everything About Bubble Gum Simulator Wiki26 abril 2025
Discuss Everything About Bubble Gum Simulator Wiki26 abril 2025 -
coinEZ/cryptocurrencies.json at main · Purukitto/coinEZ · GitHub26 abril 2025
-
 Our Apologia - Orchestra Magna Grecia26 abril 2025
Our Apologia - Orchestra Magna Grecia26 abril 2025 -
RBX Games26 abril 2025
-
 trading random roblox acc (no rh or am stuff sry;c) : r/CrossTrading_inRoblox26 abril 2025
trading random roblox acc (no rh or am stuff sry;c) : r/CrossTrading_inRoblox26 abril 2025 -
 RBX offers Promo Codes Not Expired!26 abril 2025
RBX offers Promo Codes Not Expired!26 abril 2025 -
 callmehbob: probably has tons of thousands of robux from her game. callmehbob's face: : r/RoyaleHigh_Roblox26 abril 2025
callmehbob: probably has tons of thousands of robux from her game. callmehbob's face: : r/RoyaleHigh_Roblox26 abril 2025
você pode gostar
-
 Console playstation 5 midia fisica26 abril 2025
Console playstation 5 midia fisica26 abril 2025 -
 Ant-Backed Hello Seeking Funds at Likely Lower Valuation - Bloomberg26 abril 2025
Ant-Backed Hello Seeking Funds at Likely Lower Valuation - Bloomberg26 abril 2025 -
Random - FOR ASLAN - Wattpad26 abril 2025
-
Steam Community :: :: Five Nights at Freddy's Minecraft Nightmare26 abril 2025
-
 BLU-RAY) EXORCISMUS: A POSSESSÃO - Manuel Carballo - DVD26 abril 2025
BLU-RAY) EXORCISMUS: A POSSESSÃO - Manuel Carballo - DVD26 abril 2025 -
 COMO COLOCAR PLACAS/ITENS NO PLS DONATE PARA VENDER E GANHAR ROBUX NO ROBLOX26 abril 2025
COMO COLOCAR PLACAS/ITENS NO PLS DONATE PARA VENDER E GANHAR ROBUX NO ROBLOX26 abril 2025 -
 McFarlane - DC Justice League 7 Figures - Aquaman26 abril 2025
McFarlane - DC Justice League 7 Figures - Aquaman26 abril 2025 -
 🔝 Códigos Heroes Online - diciembre 2023 Códigos gratis26 abril 2025
🔝 Códigos Heroes Online - diciembre 2023 Códigos gratis26 abril 2025 -
 How To Download PS2 Games For PCSX226 abril 2025
How To Download PS2 Games For PCSX226 abril 2025 -
 Boruto's New Hokage Is The Weakest In History26 abril 2025
Boruto's New Hokage Is The Weakest In History26 abril 2025


