Algorithms, Free Full-Text
Por um escritor misterioso
Last updated 15 abril 2025
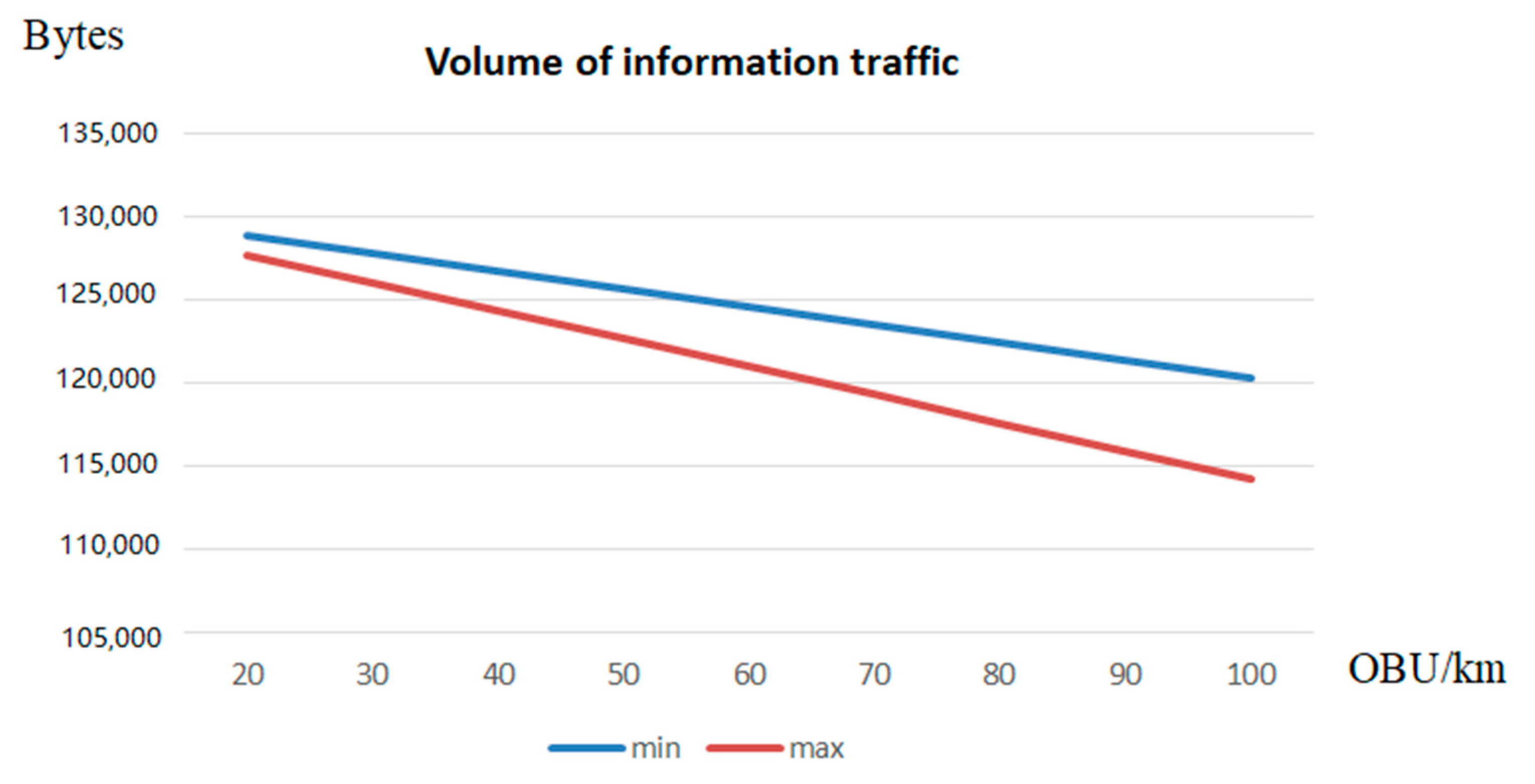
Authentication protocols are expanding their application scope in wireless information systems, among which are low-orbit satellite communication systems (LOSCS) for the OneWeb space Internet, automatic object identification systems using RFID, the Internet of Things, intelligent transportation systems (ITS), Vehicular Ad Hoc Network (VANET). This is due to the fact that authentication protocols effectively resist a number of attacks on wireless data transmission channels in these systems. The main disadvantage of most authentication protocols is the use of symmetric and asymmetric encryption systems to ensure high cryptographic strength. As a result, there is a problem in delivering keys to the sides of the prover and the verifier. At the same time, compromising of keys will lead to a decrease in the level of protection of the transmitted data. Zero-knowledge authentication protocols (ZKAP) are able to eliminate this disadvantage. However, most of these protocols use multiple rounds to authenticate the prover. Therefore, ZKAP, which has minimal time costs, is developed in the article. A scheme for adapting protocol parameters has been developed in this protocol to increase its efficiency. Reductions in the level of confidentiality allow us to reduce the time spent on the execution of the authentication protocol. This increases the volume of information traffic. At the same time, an increase in the confidentiality of the protocol entails an increase in the time needed for authentication of the prover, which reduces the volume of information traffic. The FPGA Artix-7 xc7a12ticsg325-1L was used to estimate the time spent implementing the adaptive ZKAP protocol. Testing was performed for 32- and 64-bit adaptive authentication protocols.
Learn About Algorithms and Data Structures in this Free 6-hour Course
Algorithm for optimized mRNA design improves stability and
Genetic Algorithms And Investment Strategies Download - Colaboratory

Search algorithm - Wikipedia
Word cloud algorithm Royalty Free Vector Image

Text Algorithms - Free Computer, Programming, Mathematics

The Algorithms Illuminated Book Series
Algorithms : Free Download, Borrow, and Streaming : Internet Archive

Free Course: Data Structure and Algorithms in JAVA from Great
Top text generation algorithms how they work - FasterCapital
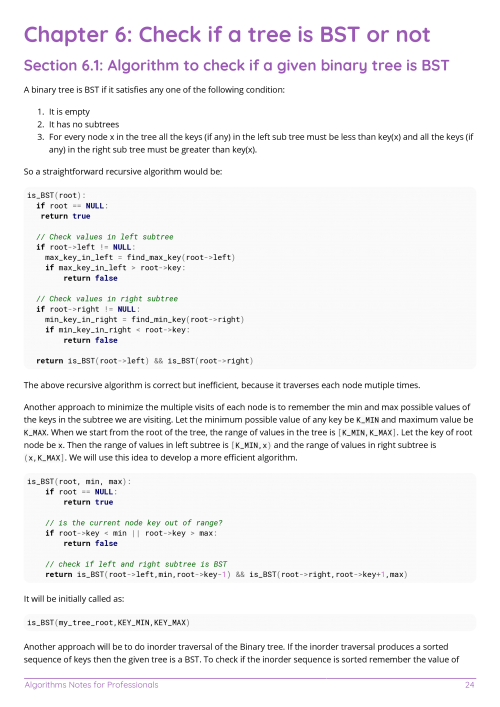
Free Algorithms Book
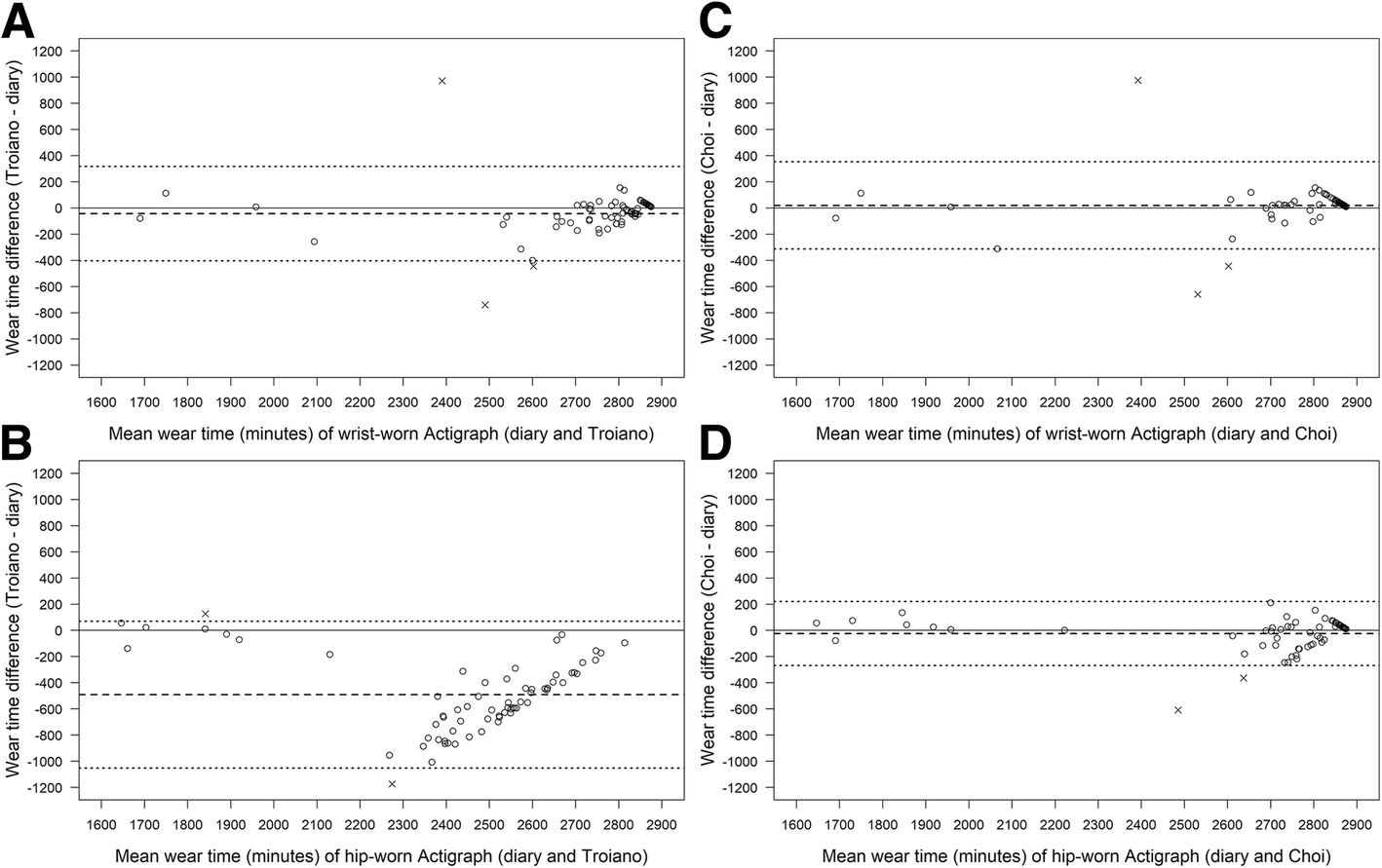
Validation of automatic wear-time detection algorithms in a free
Common pitfalls and recommendations for using machine learning to

Algo-rythmics

What is A* Search Algorithm? A* (star) Algorithm in AI 2024
Recomendado para você
-
![All Roblox Project New World Codes (December 2023) [Haze Piece]](https://twinfinite.net/wp-content/uploads/2022/12/Fruit-Battlegrounds-codes.jpg) All Roblox Project New World Codes (December 2023) [Haze Piece]15 abril 2025
All Roblox Project New World Codes (December 2023) [Haze Piece]15 abril 2025 -
CODE] HAZE PIECE - Roblox15 abril 2025
-
![135K CODE] Project New World, Roblox GAME, ALL SECRET CODES, ALL WORKING CODES](https://i.ytimg.com/vi/uA5Ij2VwemU/sddefault.jpg) 135K CODE] Project New World, Roblox GAME, ALL SECRET CODES, ALL WORKING CODES15 abril 2025
135K CODE] Project New World, Roblox GAME, ALL SECRET CODES, ALL WORKING CODES15 abril 2025 -
 Roblox Iceberg Chart (Made with a lot of help from my friends!) : r/IcebergCharts15 abril 2025
Roblox Iceberg Chart (Made with a lot of help from my friends!) : r/IcebergCharts15 abril 2025 -
 News/Media Archive - Skender15 abril 2025
News/Media Archive - Skender15 abril 2025 -
 MiPCT Webinar 04/18/201215 abril 2025
MiPCT Webinar 04/18/201215 abril 2025 -
 Knowledge Center15 abril 2025
Knowledge Center15 abril 2025 -
 Saticoy & Wells Community Plan & Development - City Of Ventura15 abril 2025
Saticoy & Wells Community Plan & Development - City Of Ventura15 abril 2025 -
 ALL NEW *SECRET* CODES in PROJECT NEW WORLD CODES! (Roblox Project New World Codes)15 abril 2025
ALL NEW *SECRET* CODES in PROJECT NEW WORLD CODES! (Roblox Project New World Codes)15 abril 2025 -
 Project New World codes (December 2022) - Free EXP boosts and more15 abril 2025
Project New World codes (December 2022) - Free EXP boosts and more15 abril 2025
você pode gostar
-
 Ranking of Kings Episode 17: Bojji's Growth and Ouken's15 abril 2025
Ranking of Kings Episode 17: Bojji's Growth and Ouken's15 abril 2025 -
 4 Smothered Mate Images, Stock Photos, 3D objects, & Vectors15 abril 2025
4 Smothered Mate Images, Stock Photos, 3D objects, & Vectors15 abril 2025 -
 Redeeming your pre-order code for Avatar: Frontiers of Pandora15 abril 2025
Redeeming your pre-order code for Avatar: Frontiers of Pandora15 abril 2025 -
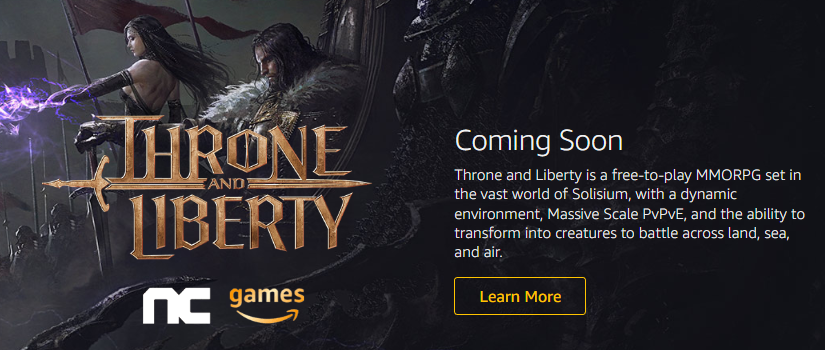 Will Throne and Liberty be Free to Play? -- TL15 abril 2025
Will Throne and Liberty be Free to Play? -- TL15 abril 2025 -
 What Is Y2K Aesthetic And How To Achieve It15 abril 2025
What Is Y2K Aesthetic And How To Achieve It15 abril 2025 -
 Skyward Flight: The Collection: Sunreach, ReDawn, Evershore by Brandon Sanderson, Janci Patterson - Books - Hachette Australia15 abril 2025
Skyward Flight: The Collection: Sunreach, ReDawn, Evershore by Brandon Sanderson, Janci Patterson - Books - Hachette Australia15 abril 2025 -
 59 Coisas para Fazer em Savannah - Hellotickets15 abril 2025
59 Coisas para Fazer em Savannah - Hellotickets15 abril 2025 -
 Las Vegas Pinball Repair In-Home15 abril 2025
Las Vegas Pinball Repair In-Home15 abril 2025 -
 Premium Vector Calligraphy krishna mantra chants hindu mantra hare krishna mantra15 abril 2025
Premium Vector Calligraphy krishna mantra chants hindu mantra hare krishna mantra15 abril 2025 -
 Mini Jogo Labirinto Animais da Quinta Sortido15 abril 2025
Mini Jogo Labirinto Animais da Quinta Sortido15 abril 2025
![CODE] HAZE PIECE - Roblox](https://tr.rbxcdn.com/9827b6a4b2ab7c0e795724a6e3c260bd/768/432/Image/Png)