What Is Two-Factor Authentication (2FA)? How It Works and Example
Por um escritor misterioso
Last updated 16 abril 2025
:max_bytes(150000):strip_icc()/twofactor-authentication-2fa.asp-final-5dc205d2a08b447abfb2e15eb131e28e.png)
Two-factor authentication (2FA) is a security system that requires two distinct forms of identification in order to access something.
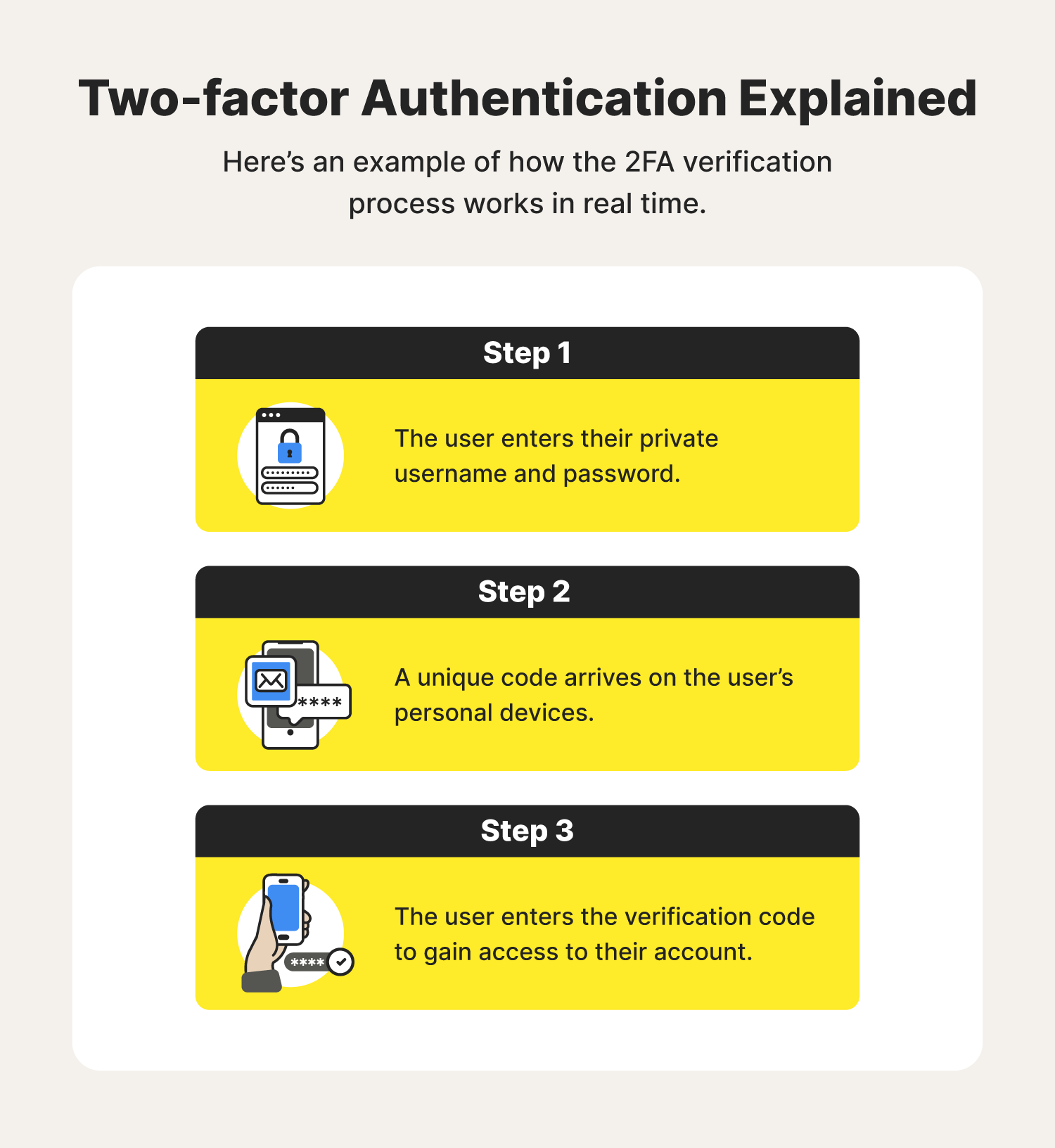
What is 2FA? A simplified guide to two-factor authentication - Norton
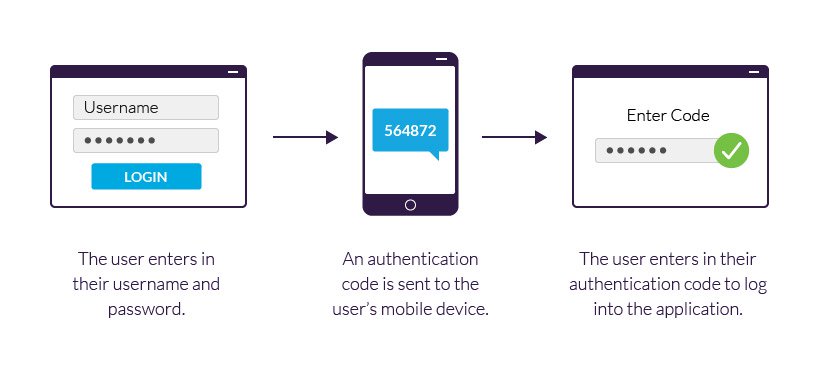
What is Two Factor Authentication, Pros and Cons of 2FA

What's the Difference Between 2FA and 2SV? - Rublon
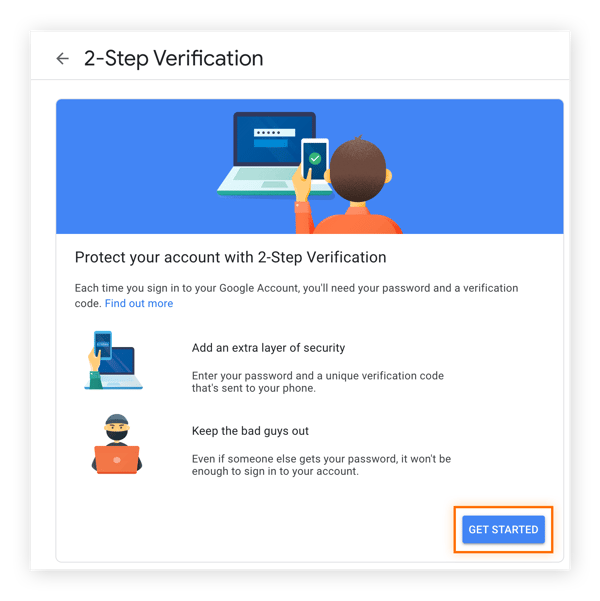
How Does Two-Factor Authentication (2FA) Work?
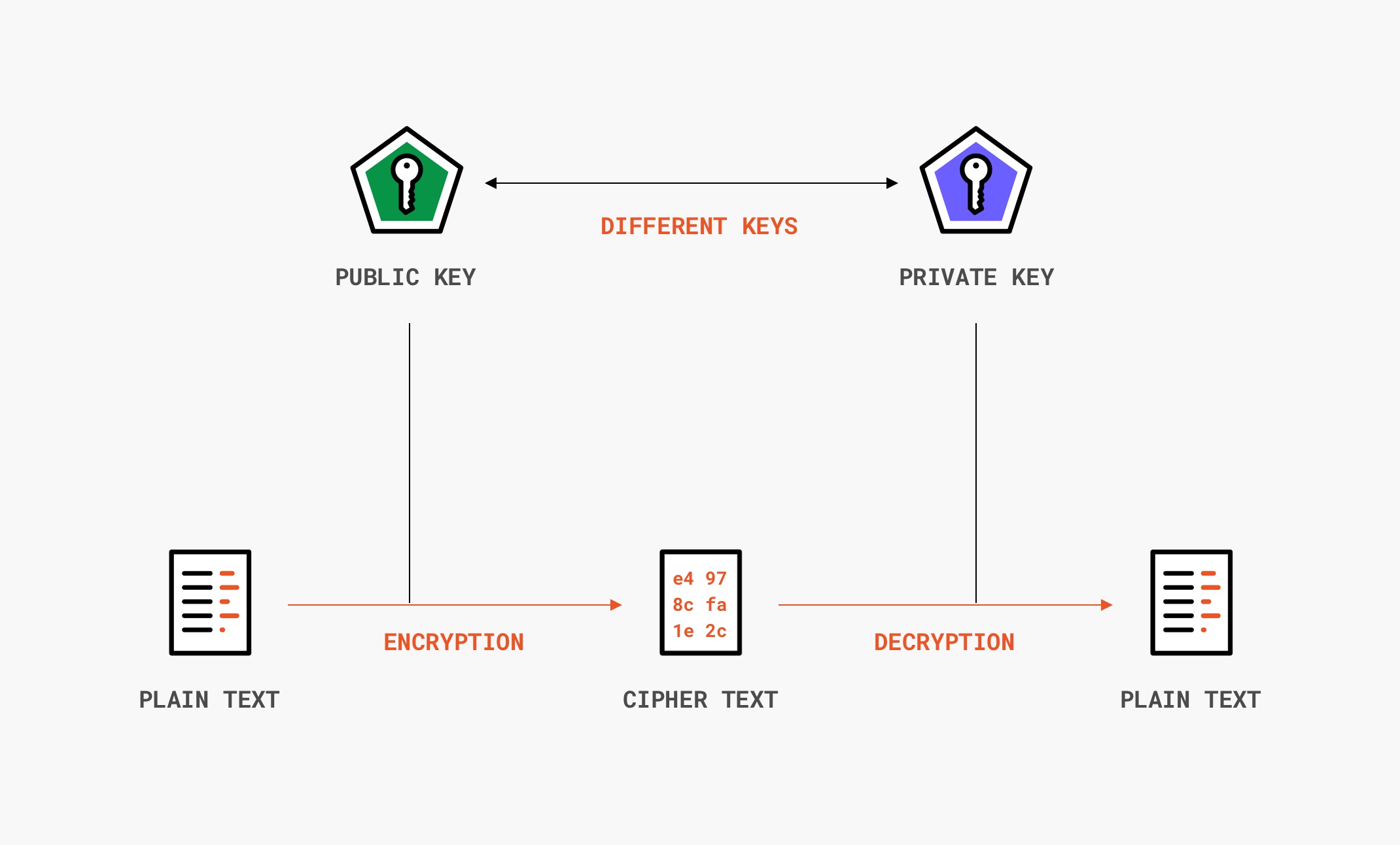
The Working Principles of 2FA (2-Factor Authentication) Hardware

What is two-factor authentication?

The 12 Days of 2FA: How to Enable Two-Factor Authentication For

Two-Factor Authentication: How It Works and Why You Should Use It

What is Two-Factor Authentication (2FA) and Why Should You Use It?
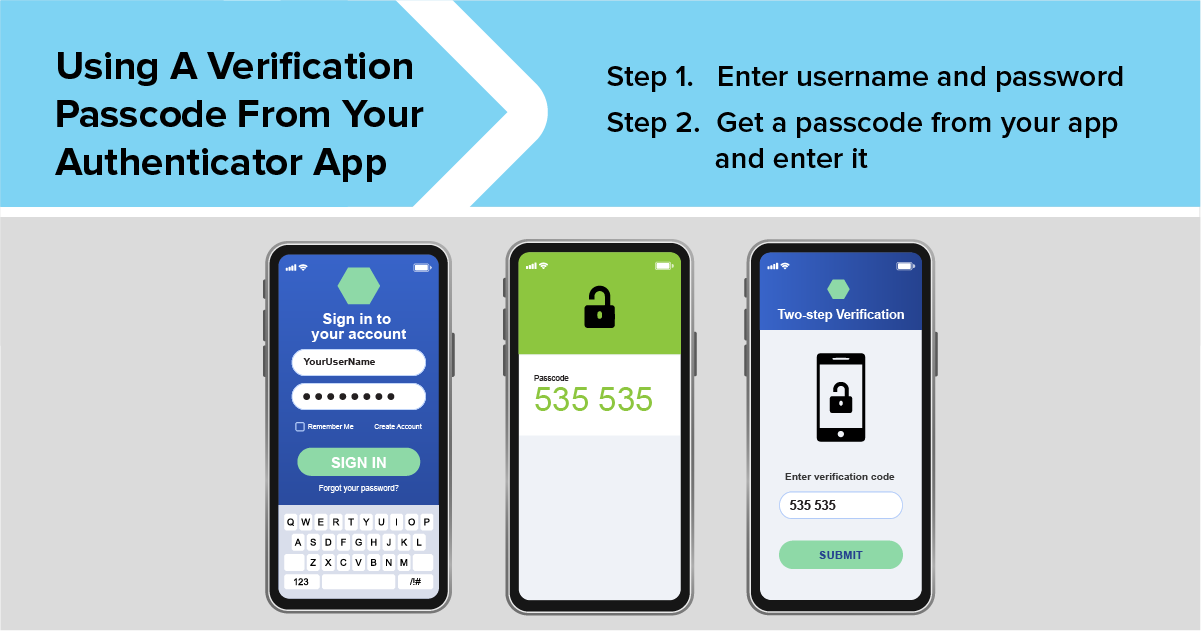
Use Two-factor Authentication to Protect Your Accounts
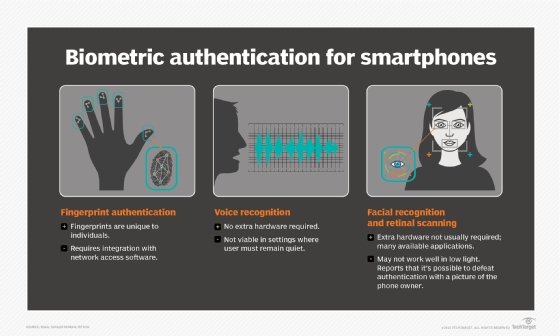
What is Two-Factor Authentication (2FA) and How Does It Work?

What Is Multi-Factor Authentication (MFA)? How Does it Work?

How Does Two Factor Authentication Work?

What is two-factor authentication (2FA)?
Recomendado para você
-
Forgot password, Can't log in16 abril 2025
-
 Introducing Home and Feeds on Facebook16 abril 2025
Introducing Home and Feeds on Facebook16 abril 2025 -
Lawn Mowers, Golf Equipment, Landscape Equipment, Irrigation16 abril 2025
-
 Orcas (Killer whales)16 abril 2025
Orcas (Killer whales)16 abril 2025 -
 Accrington Stanley16 abril 2025
Accrington Stanley16 abril 2025 -
 Technical University of Denmark - DTU16 abril 2025
Technical University of Denmark - DTU16 abril 2025 -
 Home - Trans Lifeline16 abril 2025
Home - Trans Lifeline16 abril 2025 -
 Getting more sleep reduces caloric intake, a game changer for16 abril 2025
Getting more sleep reduces caloric intake, a game changer for16 abril 2025 -
 Timbuktu - UNESCO World Heritage Centre16 abril 2025
Timbuktu - UNESCO World Heritage Centre16 abril 2025 -
 Launch Comms: Prepare for Call of Duty: Modern Warfare III16 abril 2025
Launch Comms: Prepare for Call of Duty: Modern Warfare III16 abril 2025
você pode gostar
-
 Bebê Reborn Menina Realista Bebê Reborn Negra com Enxoval16 abril 2025
Bebê Reborn Menina Realista Bebê Reborn Negra com Enxoval16 abril 2025 -
 FC 24 King of the Hill – FIFPlay16 abril 2025
FC 24 King of the Hill – FIFPlay16 abril 2025 -
 Garry Kasparov's Greatest Chess Games Volume 1 (Chess World Champions) See more16 abril 2025
Garry Kasparov's Greatest Chess Games Volume 1 (Chess World Champions) See more16 abril 2025 -
PC Best and Newest games16 abril 2025
-
 Adolescente menina roupas de verão crianças moda camisa tops +16 abril 2025
Adolescente menina roupas de verão crianças moda camisa tops +16 abril 2025 -
 Making an Epic Charcuterie Board with Cheese - Skinnytaste16 abril 2025
Making an Epic Charcuterie Board with Cheese - Skinnytaste16 abril 2025 -
 PlayStation 5 Edição Digital 825GB 2 Controles - Sony com God of War Ragnarok - Outros Games - Magazine Luiza16 abril 2025
PlayStation 5 Edição Digital 825GB 2 Controles - Sony com God of War Ragnarok - Outros Games - Magazine Luiza16 abril 2025 -
 SCP-049, The Plague Doctor, Wiki16 abril 2025
SCP-049, The Plague Doctor, Wiki16 abril 2025 -
 Topper's New Trend Leaving IIT Bombay in 6 months, Joined MIT16 abril 2025
Topper's New Trend Leaving IIT Bombay in 6 months, Joined MIT16 abril 2025 -
 Otome wa Boku ni Koishiteru - Wikipedia16 abril 2025
Otome wa Boku ni Koishiteru - Wikipedia16 abril 2025


