Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 11 abril 2025


CI/CD Security Best Practices
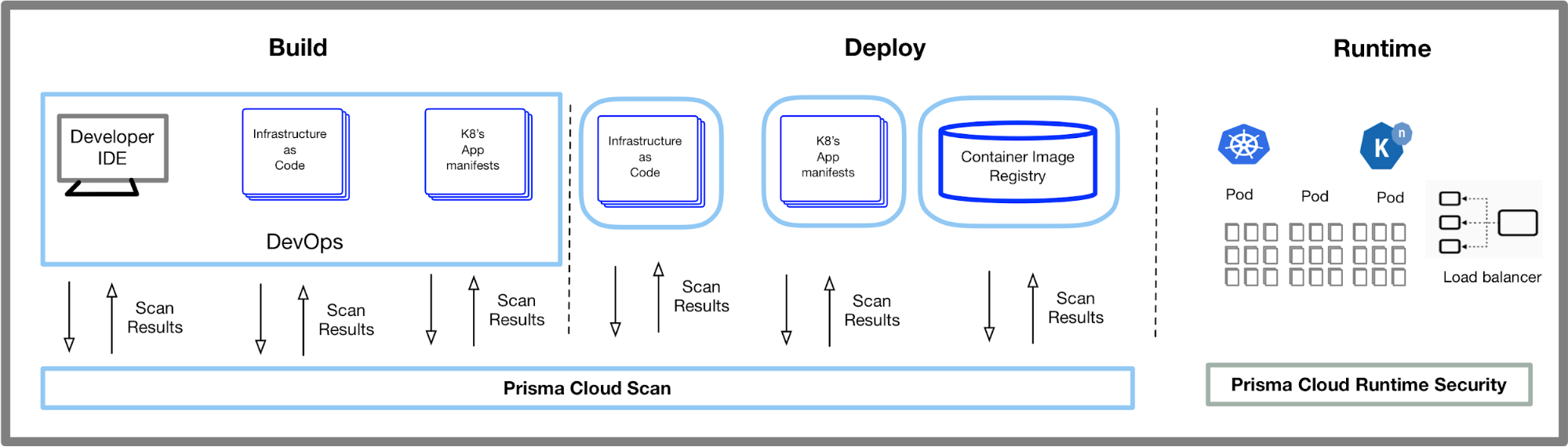
3 Simple Techniques to Add Security Into the CI/CD Pipeline

Cloud Security in CI/CD Part I: Terraform, Github, CircleCI, and Fugue

CI/CD Security: 7 Risks and What You Can Do About Them
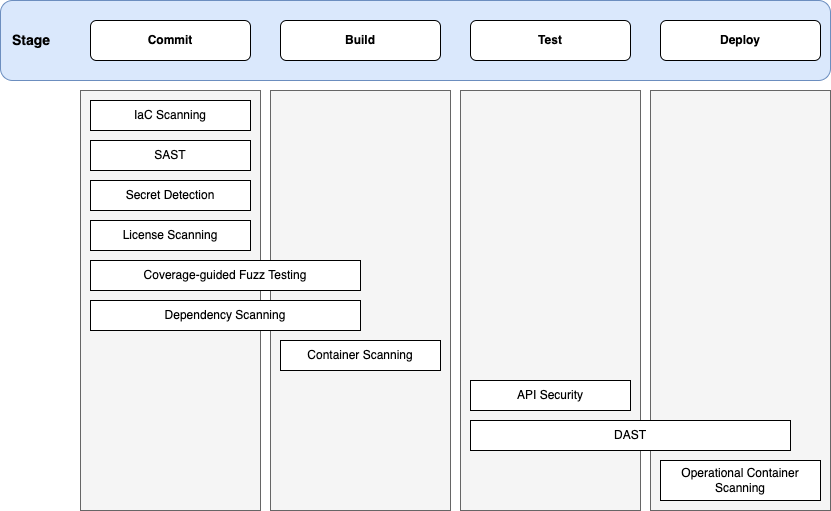
Application security

How to Integrate Security Scanning into Your CI/CD Pipeline
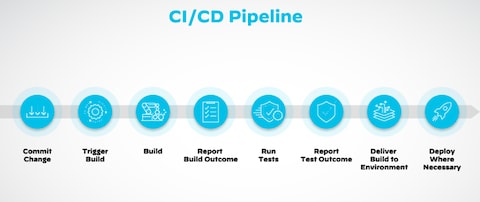
What Is the CI/CD Pipeline? - Palo Alto Networks
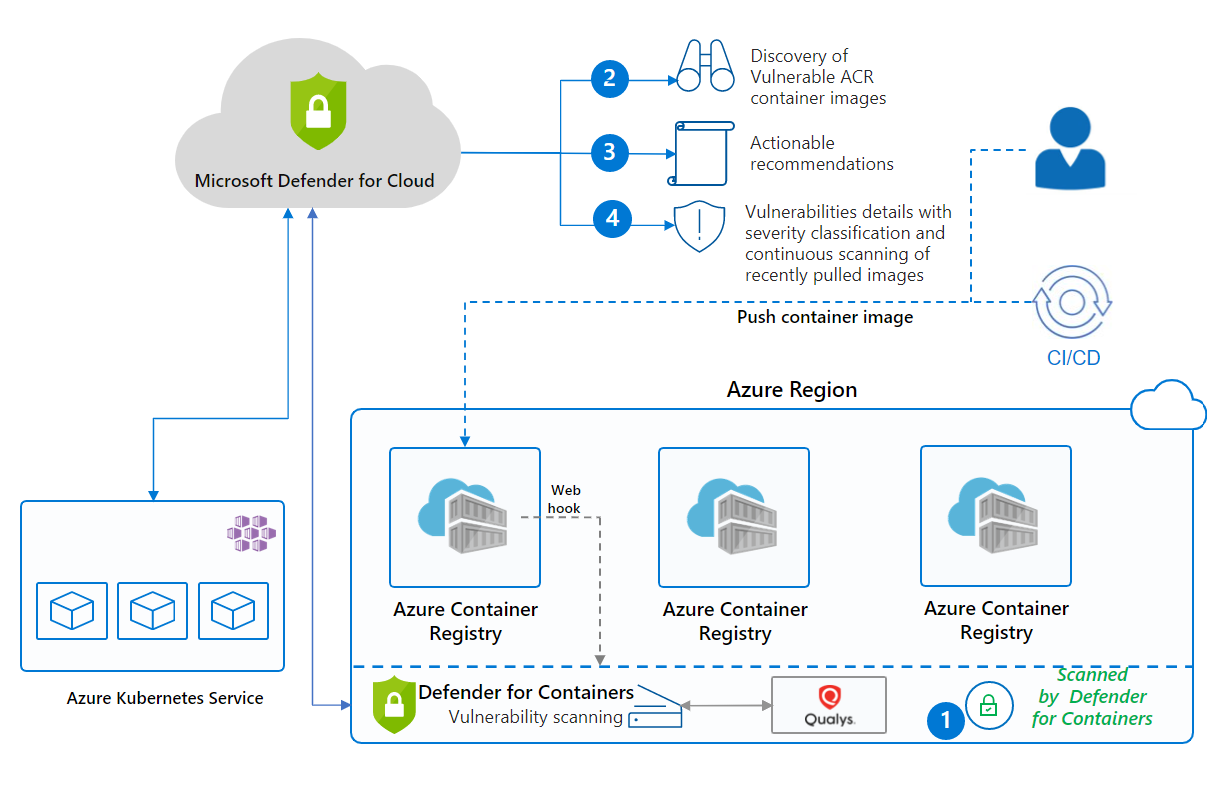
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub
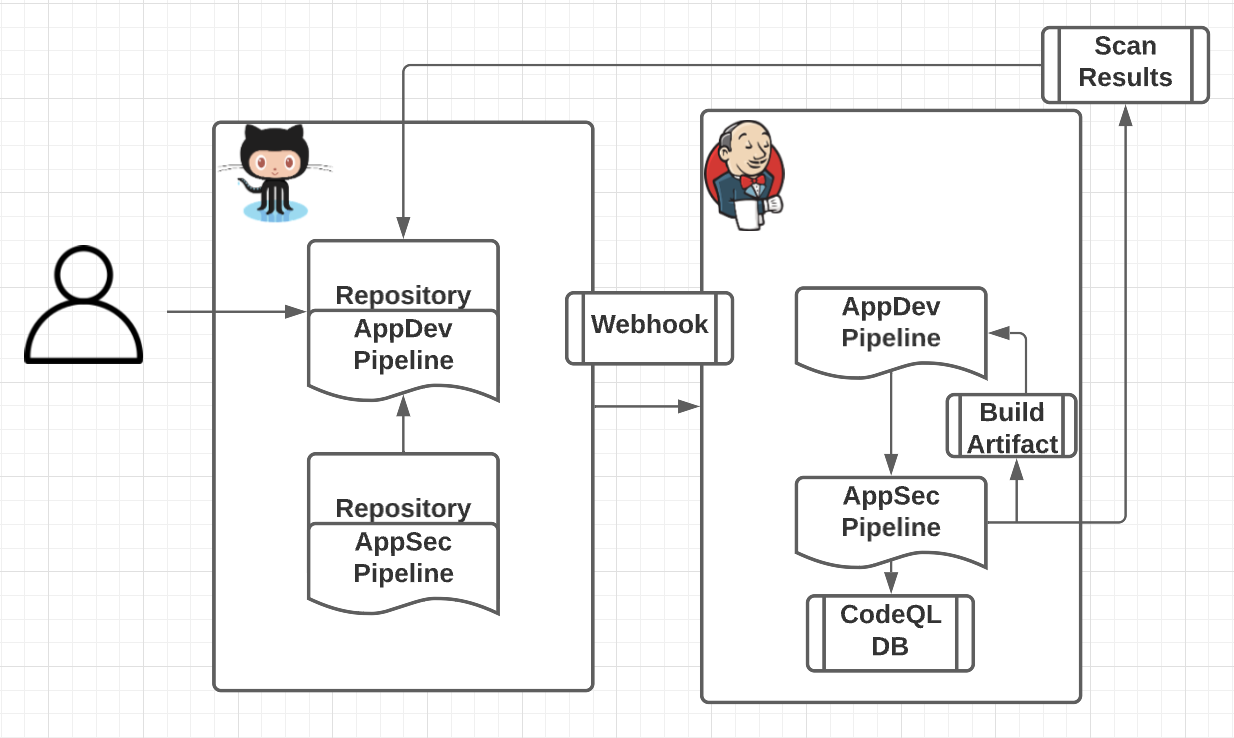
Best practices on rolling out code scanning at enterprise scale - The GitHub Blog

What DevSecOps Means for Your CI/CD Pipeline
Recomendado para você
-
Open Source Scanning Software - Security Analysis Tool (OSS)11 abril 2025
-
 DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server11 abril 2025
DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server11 abril 2025 -
 Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I11 abril 2025
Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I11 abril 2025 -
 Appointment Scanner - Global Entry Interview Alerts11 abril 2025
Appointment Scanner - Global Entry Interview Alerts11 abril 2025 -
 NeXus file structure showing the NXtomo subentry expanded to show11 abril 2025
NeXus file structure showing the NXtomo subentry expanded to show11 abril 2025 -
 Nexus Vulnerability Scanner: Getting Started with Vulnerability Analysis - DEV Community11 abril 2025
Nexus Vulnerability Scanner: Getting Started with Vulnerability Analysis - DEV Community11 abril 2025 -
 Nexus SDK11 abril 2025
Nexus SDK11 abril 2025 -
 Custom Scan Requirements - Instant Scan - CCR at Starfield Nexus - Mods and Community11 abril 2025
Custom Scan Requirements - Instant Scan - CCR at Starfield Nexus - Mods and Community11 abril 2025 -
Keystone Dental Announces Market Launch of Nexus Connect, the First A.I. Enabled Intraoral Implant-Scan Analyzer for the Nexus iOS Full-Arch Solution11 abril 2025
-
 Sound Devices A20-Nexus Receiver - Trew Audio11 abril 2025
Sound Devices A20-Nexus Receiver - Trew Audio11 abril 2025
você pode gostar
-
![A JORNADA da BIGGORON SWORD de ZELDA OCARINA of TIME #44 - [Gameplay PT-BR] Thamás Morelli](https://i.ytimg.com/vi/SyXa3wChRdc/maxresdefault.jpg) A JORNADA da BIGGORON SWORD de ZELDA OCARINA of TIME #44 - [Gameplay PT-BR] Thamás Morelli11 abril 2025
A JORNADA da BIGGORON SWORD de ZELDA OCARINA of TIME #44 - [Gameplay PT-BR] Thamás Morelli11 abril 2025 -
 POLÔNIA E ARGENTINA AO VIVO - COPA DO MUNDO 2022 AO VIVO - 3ª11 abril 2025
POLÔNIA E ARGENTINA AO VIVO - COPA DO MUNDO 2022 AO VIVO - 3ª11 abril 2025 -
 Buy wholesale Fantasy Forts Wood Large Set11 abril 2025
Buy wholesale Fantasy Forts Wood Large Set11 abril 2025 -
 Shin ficou com ciúmes da Cecily(Kenja no Mago dublado)11 abril 2025
Shin ficou com ciúmes da Cecily(Kenja no Mago dublado)11 abril 2025 -
 Pocket Wiki for Slime Rancher on the App Store11 abril 2025
Pocket Wiki for Slime Rancher on the App Store11 abril 2025 -
 Doja Cat - Woman (Lyrics)11 abril 2025
Doja Cat - Woman (Lyrics)11 abril 2025 -
 Compass, direction, making, navigation, online icon - Download on Iconfinder11 abril 2025
Compass, direction, making, navigation, online icon - Download on Iconfinder11 abril 2025 -
 San Miguel vs Comunicaciones H2H stats - SoccerPunter11 abril 2025
San Miguel vs Comunicaciones H2H stats - SoccerPunter11 abril 2025 -
trolls poppy by 3D Models to Print - yeggi11 abril 2025
-
 Shadowverse Granblue Fantasy Character Art Drawing, Anime, game, cg Artwork, video Game png11 abril 2025
Shadowverse Granblue Fantasy Character Art Drawing, Anime, game, cg Artwork, video Game png11 abril 2025
