Delay-CJ: A novel cryptojacking covert attack method based on
Por um escritor misterioso
Last updated 17 abril 2025

Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…

Cryptojacking soars as cyberattacks increase, diversify - Help Net Security

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks
Technologies, Free Full-Text
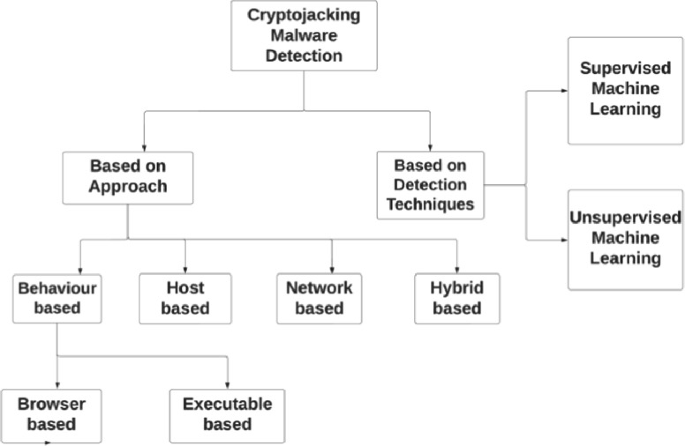
Variants of Crypto-Jacking Attacks and Their Detection Techniques
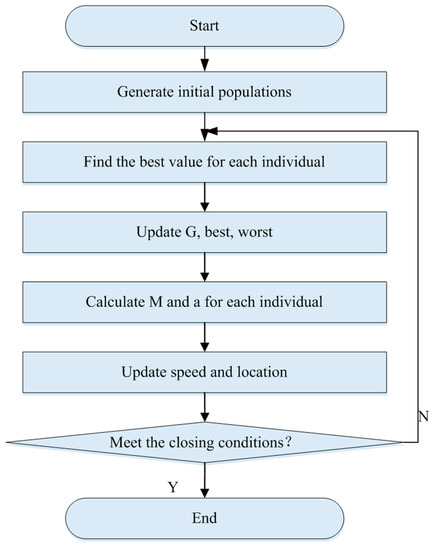
Electronics, Free Full-Text
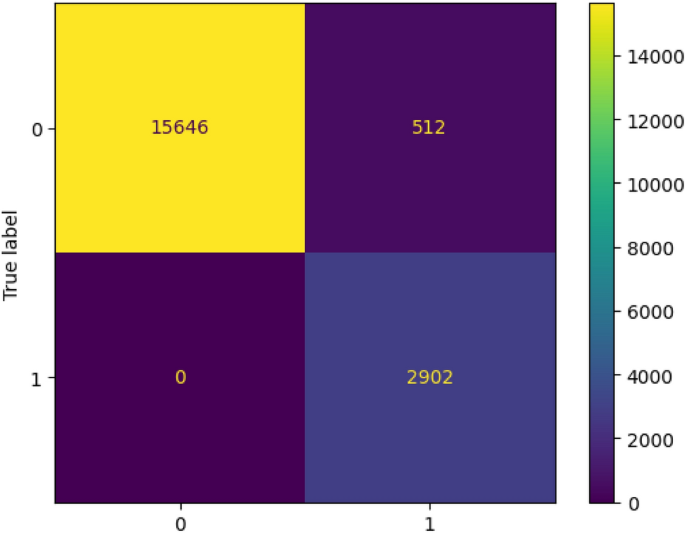
A deep learning approach for host-based cryptojacking malware detection

SHAOYING LIU (Graduate School of Advanced Science and Engineering)

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Handbook of Research On Machine and Deep Learning Applications For Cyber Security, PDF, Machine Learning

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks

PDF) An Approach to Detect Alopecia Areata Hair Disease Using Deep Learning

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect
Recomendado para você
-
minerBlock17 abril 2025
-
GitHub - unkn0wn404/MinerBlocker: Chrome extension Miner Blocker designed to stop coin miners scripts and block cryptojackers from using your CPU for mining17 abril 2025
-
 7 Easy Ways To Block Cryptocurrency Mining In Your Web Browser17 abril 2025
7 Easy Ways To Block Cryptocurrency Mining In Your Web Browser17 abril 2025 -
 Cryptojacking: Digging for your own Treasure17 abril 2025
Cryptojacking: Digging for your own Treasure17 abril 2025 -
 How To Block Cryptomining Scripts In Your Web Browser17 abril 2025
How To Block Cryptomining Scripts In Your Web Browser17 abril 2025 -
 New year, new browser. Opera 50 introduces anti-Bitcoin mining tool - Blog17 abril 2025
New year, new browser. Opera 50 introduces anti-Bitcoin mining tool - Blog17 abril 2025 -
 Salon Offers Visitors In-House Cryptocurrency Mining When Blocking Ads – Mining Bitcoin News17 abril 2025
Salon Offers Visitors In-House Cryptocurrency Mining When Blocking Ads – Mining Bitcoin News17 abril 2025 -
![App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos](https://images.yourstory.com/cs/wordpress/2018/08/Kiwi-Feature.png?w=1152&fm=auto&ar=2:1&mode=crop&crop=faces) App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos17 abril 2025
App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos17 abril 2025 -
 Helium Miner 915mhz, Helium Miner Lora17 abril 2025
Helium Miner 915mhz, Helium Miner Lora17 abril 2025 -
 Unknown, Accents17 abril 2025
Unknown, Accents17 abril 2025
você pode gostar
-
 Roblox Pink Preppy Girl | Essential T-Shirt17 abril 2025
Roblox Pink Preppy Girl | Essential T-Shirt17 abril 2025 -
 Sunset Overdrive is coming to Steam and Windows Store today17 abril 2025
Sunset Overdrive is coming to Steam and Windows Store today17 abril 2025 -
 Hello Kitty vai ganhar coleção de NFTs em 202217 abril 2025
Hello Kitty vai ganhar coleção de NFTs em 202217 abril 2025 -
 Fantasy Football Hub follow up tweet : r/FantasyPL17 abril 2025
Fantasy Football Hub follow up tweet : r/FantasyPL17 abril 2025 -
 Como ver o seu Steam ID17 abril 2025
Como ver o seu Steam ID17 abril 2025 -
 Game of Thrones Prequel Details — House of the Dragon News Cast, Rumors17 abril 2025
Game of Thrones Prequel Details — House of the Dragon News Cast, Rumors17 abril 2025 -
 Desenhos de Ladybug para colorir - Como fazer em casa Desenhos para colorir ladybug, Folhas para colorir, Desenhos para colorir17 abril 2025
Desenhos de Ladybug para colorir - Como fazer em casa Desenhos para colorir ladybug, Folhas para colorir, Desenhos para colorir17 abril 2025 -
 Sonic The Hedgehog (2020) - Big Game Spot - GameSpot17 abril 2025
Sonic The Hedgehog (2020) - Big Game Spot - GameSpot17 abril 2025 -
 The Legend of Zelda: Ocarina of Time Nintendo 64 - Meccha Japan17 abril 2025
The Legend of Zelda: Ocarina of Time Nintendo 64 - Meccha Japan17 abril 2025 -
 Top 10 Anime Character Birthdays for August 16-31! Anime characters birthdays, Anime characters, Anime17 abril 2025
Top 10 Anime Character Birthdays for August 16-31! Anime characters birthdays, Anime characters, Anime17 abril 2025