Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 15 abril 2025

From proof-of-concept to exploitable

Pwnable-Sherpa: An interactive coaching system with a case study
Exploiting Smart Cars Using Software Defined Radio

EclecticIQ Monthly Vulnerability Trend Report - August 2018
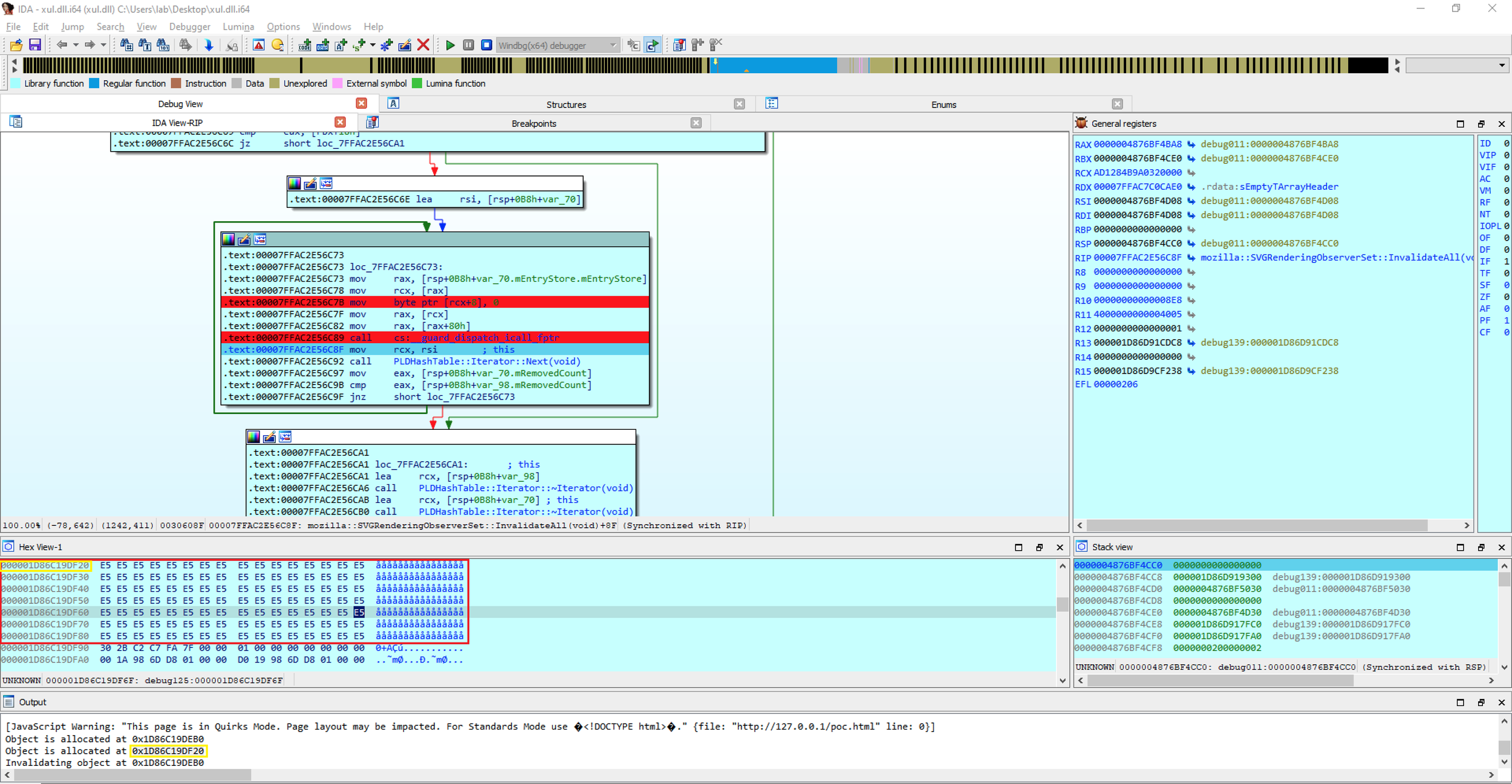
CVE-2022-26381: Gone by others! Triggering a UAF in Firefox

Automated Use-After-Free Detection and Exploit Mitigation: How Far

Top Russian General Possibly Captured in UAF Kharkiv Offensive
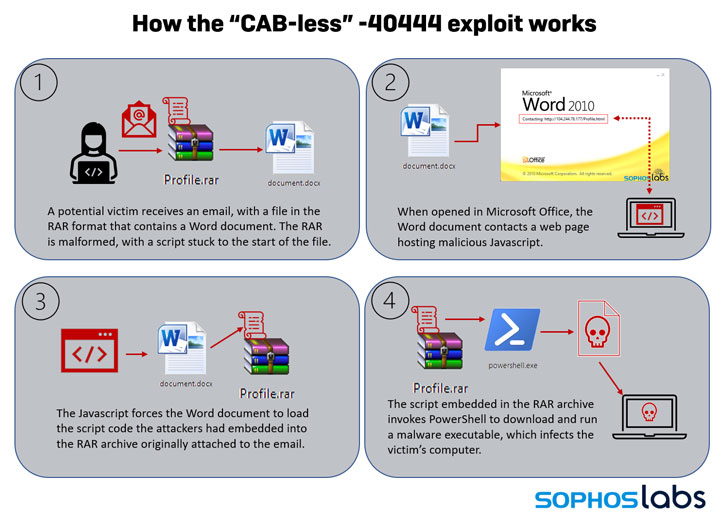
New Exploit Lets Malware Attackers Bypass Patch for Critical

UAF-GUARD: Defending the use-after-free exploits via fine-grained
First Binder Exploit Linked to SideWinder APT Group

A fine-grained classification and security analysis of web-based

PDF) Authenticator Rebinding Attack of the UAF Protocol on Mobile
Recomendado para você
-
 KING LEGACY – ScriptPastebin15 abril 2025
KING LEGACY – ScriptPastebin15 abril 2025 -
 King Legacy Mobile Script15 abril 2025
King Legacy Mobile Script15 abril 2025 -
 Macbeth - Wikipedia15 abril 2025
Macbeth - Wikipedia15 abril 2025 -
![MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS](https://i.ytimg.com/vi/a_T9vU5k14s/maxresdefault.jpg) MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS15 abril 2025
MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS15 abril 2025 -
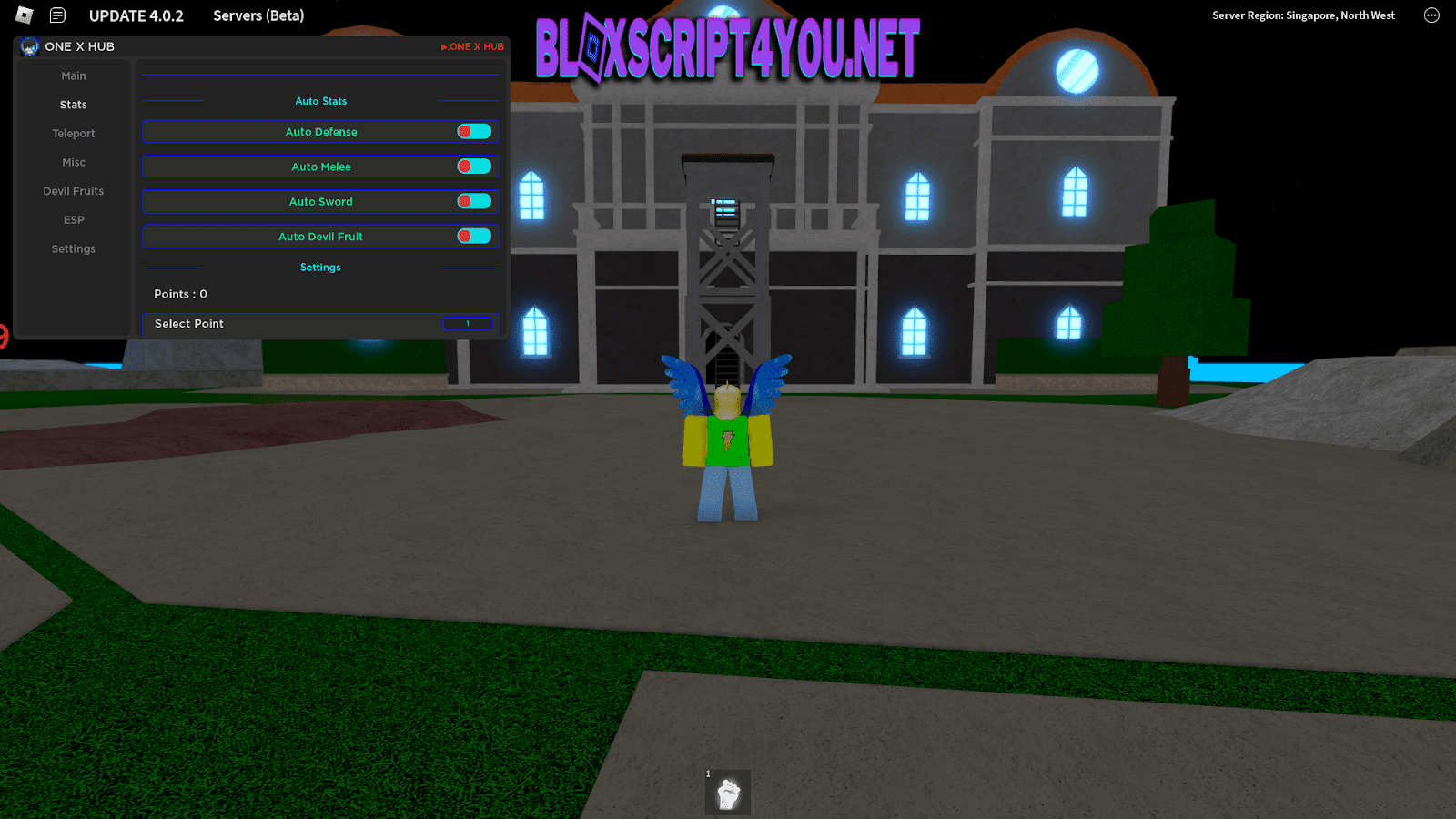 One X Hub King Legacy Script15 abril 2025
One X Hub King Legacy Script15 abril 2025 -
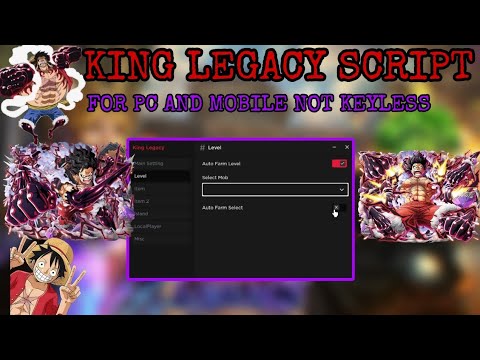 BEST KING LEGACY SCRIPT LATEST FOR PC & MOBILE NOT15 abril 2025
BEST KING LEGACY SCRIPT LATEST FOR PC & MOBILE NOT15 abril 2025 -
 Cystatin C is glucocorticoid responsive, directs recruitment of15 abril 2025
Cystatin C is glucocorticoid responsive, directs recruitment of15 abril 2025 -
 Indie Comics Review: King Spawn #6 - DC Comics News15 abril 2025
Indie Comics Review: King Spawn #6 - DC Comics News15 abril 2025 -
 Sustainability, Free Full-Text15 abril 2025
Sustainability, Free Full-Text15 abril 2025 -
 Arts & Culture - Valpo Stories15 abril 2025
Arts & Culture - Valpo Stories15 abril 2025
você pode gostar
-
 Category:Male, Fairy Tail Wiki15 abril 2025
Category:Male, Fairy Tail Wiki15 abril 2025 -
 Attack on Titan Season 3 World Premiere Event Showtimes15 abril 2025
Attack on Titan Season 3 World Premiere Event Showtimes15 abril 2025 -
 My Pokédex is different from others. Mine has only 149 in kanto region but other has 151 .. why!? : r/pokemongo15 abril 2025
My Pokédex is different from others. Mine has only 149 in kanto region but other has 151 .. why!? : r/pokemongo15 abril 2025 -
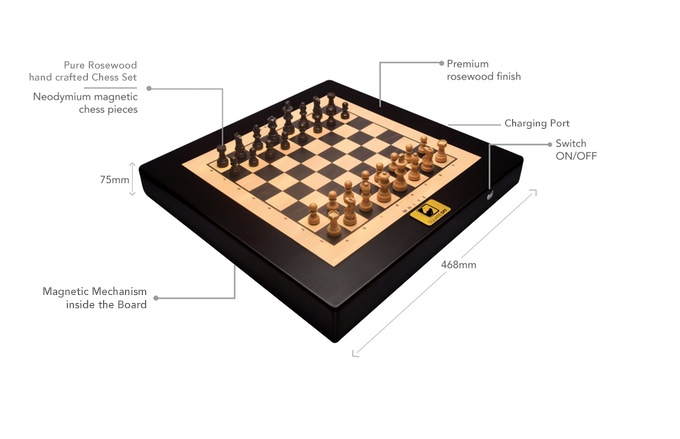 The Square Off Chessboard Moves Its Pieces Totally Hands-Free15 abril 2025
The Square Off Chessboard Moves Its Pieces Totally Hands-Free15 abril 2025 -
 Dead Island 215 abril 2025
Dead Island 215 abril 2025 -
LEGO® Star Wars™: The Skywalker Saga Galactic Edition15 abril 2025
-
Pedalada e chute no ângulo: Payet marca golaço na Liga Europa15 abril 2025
-
 Dragon Ball Z Budokai Tenkaichi 3 MOD Version Latino PS2 ISO For Android And PC15 abril 2025
Dragon Ball Z Budokai Tenkaichi 3 MOD Version Latino PS2 ISO For Android And PC15 abril 2025 -
 The Devil is a Part-Timer Season 3 Gets New Visual, Trailer, and July 13 Release Date : r/qooapp15 abril 2025
The Devil is a Part-Timer Season 3 Gets New Visual, Trailer, and July 13 Release Date : r/qooapp15 abril 2025 -
 Majin boo gordo! by SuperAgua on DeviantArt15 abril 2025
Majin boo gordo! by SuperAgua on DeviantArt15 abril 2025

