Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Last updated 16 abril 2025
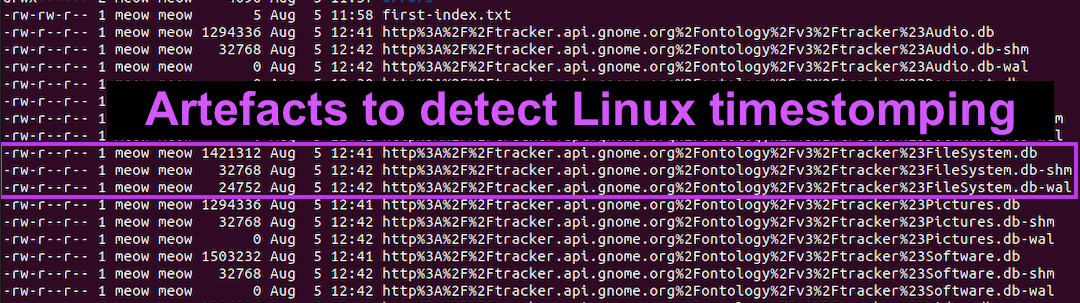
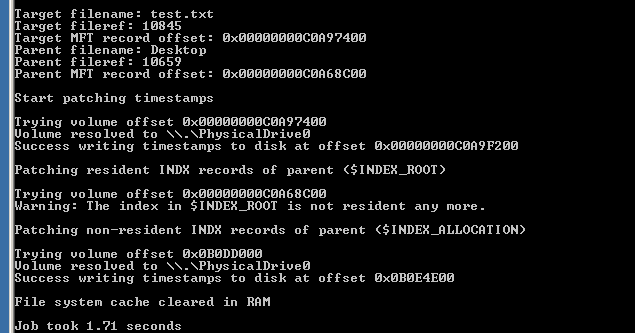
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va

Wiping Techniques and Anti-Forensics Methods
Detecting Linux Anti-Forensics: Timestomping

Detecting Linux Anti-Forensics: Timestomping
5 anti-forensics techniques to trick investigators (+ examples
inversecosᵘʷᵘ's Threads – Thread Reader App
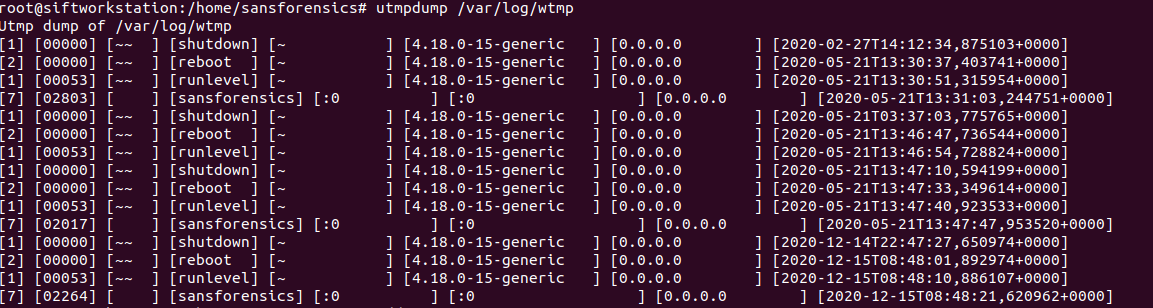
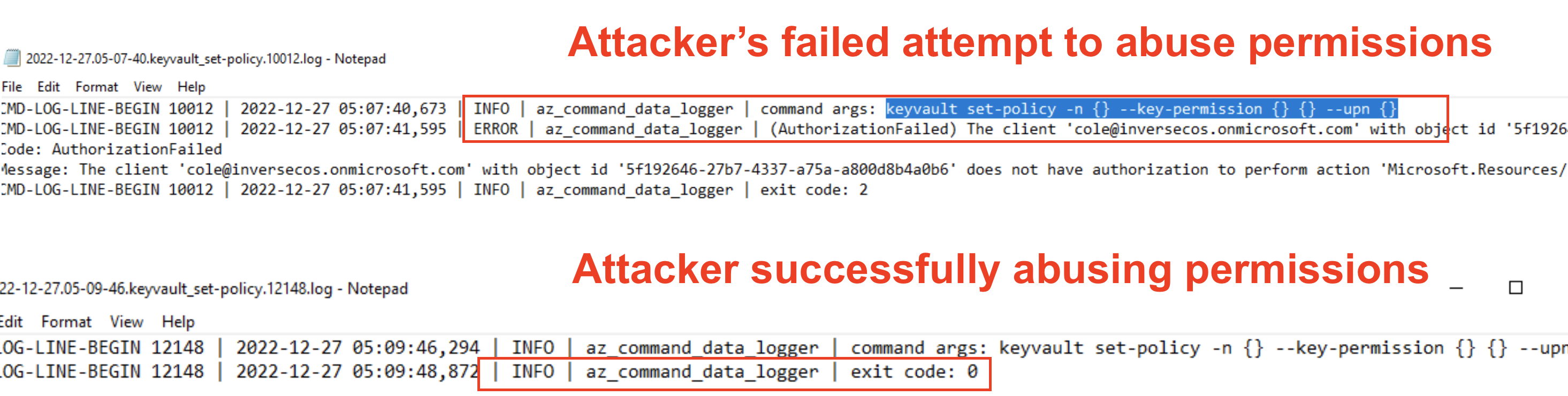
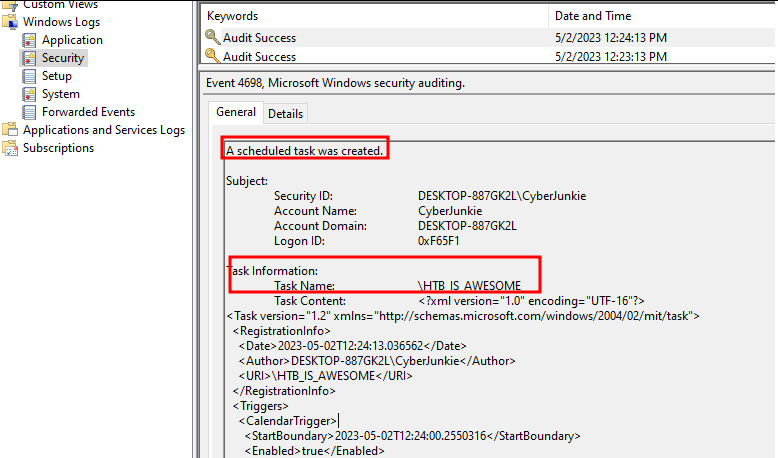
Detecting Linux Anti-Forensics Log Tampering

Defence Evasion Technique: Timestomping Detection – NTFS Forensics

A survey on anti-forensics techniques

PPT - Anti-forensics and reasons for optimism PowerPoint

5 anti-forensics techniques to trick investigators (+ examples
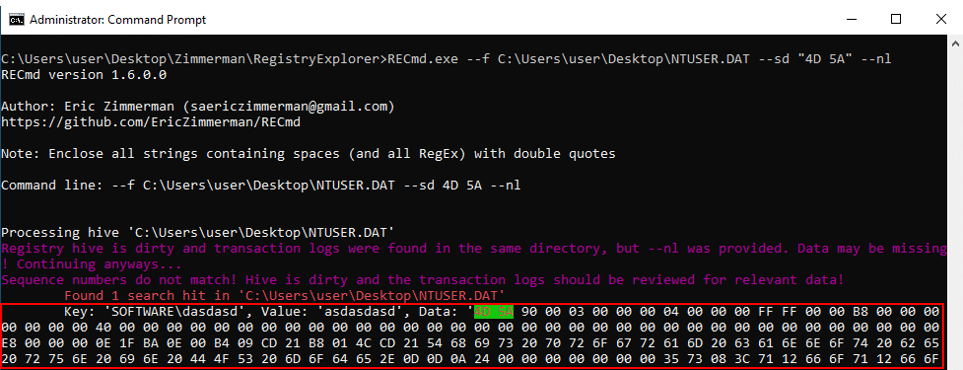
Anti-Forensics Techniques - Cynet

PDF) Detection and Mitigation of Anti-Forensics
Recomendado para você
-
 ⭐League of Legends⭐, SELLY, Scripts/Evade/Tracker16 abril 2025
⭐League of Legends⭐, SELLY, Scripts/Evade/Tracker16 abril 2025 -
💋 KISS the Insertion📍 with Escape & Evade Mobile Keep it simple, stupid. It's fun to talk about at a bar, a few drinks in, imagining skydiving from, By Joel Lambert16 abril 2025
-
 evadescript16 abril 2025
evadescript16 abril 2025 -
 Evade Script Download For Windows PC - Softlay16 abril 2025
Evade Script Download For Windows PC - Softlay16 abril 2025 -
 Compensation #2 for Parry / Evade Bug : r/ContestOfChampions16 abril 2025
Compensation #2 for Parry / Evade Bug : r/ContestOfChampions16 abril 2025 -
 RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA16 abril 2025
RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA16 abril 2025 -
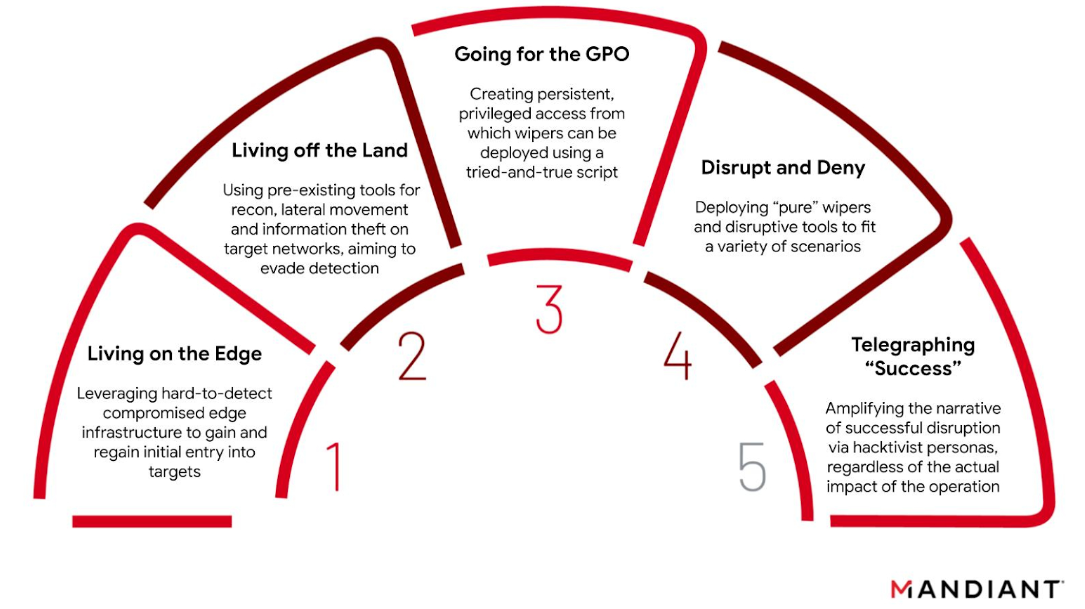 The GRU's Disruptive Playbook16 abril 2025
The GRU's Disruptive Playbook16 abril 2025 -
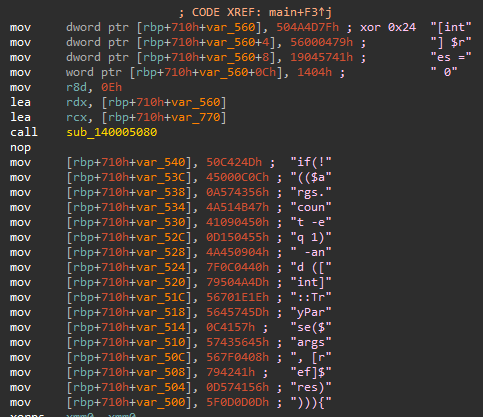 ToddyCat: Keep calm and check logs16 abril 2025
ToddyCat: Keep calm and check logs16 abril 2025 -
 Bogus URL Shorteners Go Mobile-Only in AdSense Fraud Campaign16 abril 2025
Bogus URL Shorteners Go Mobile-Only in AdSense Fraud Campaign16 abril 2025 -
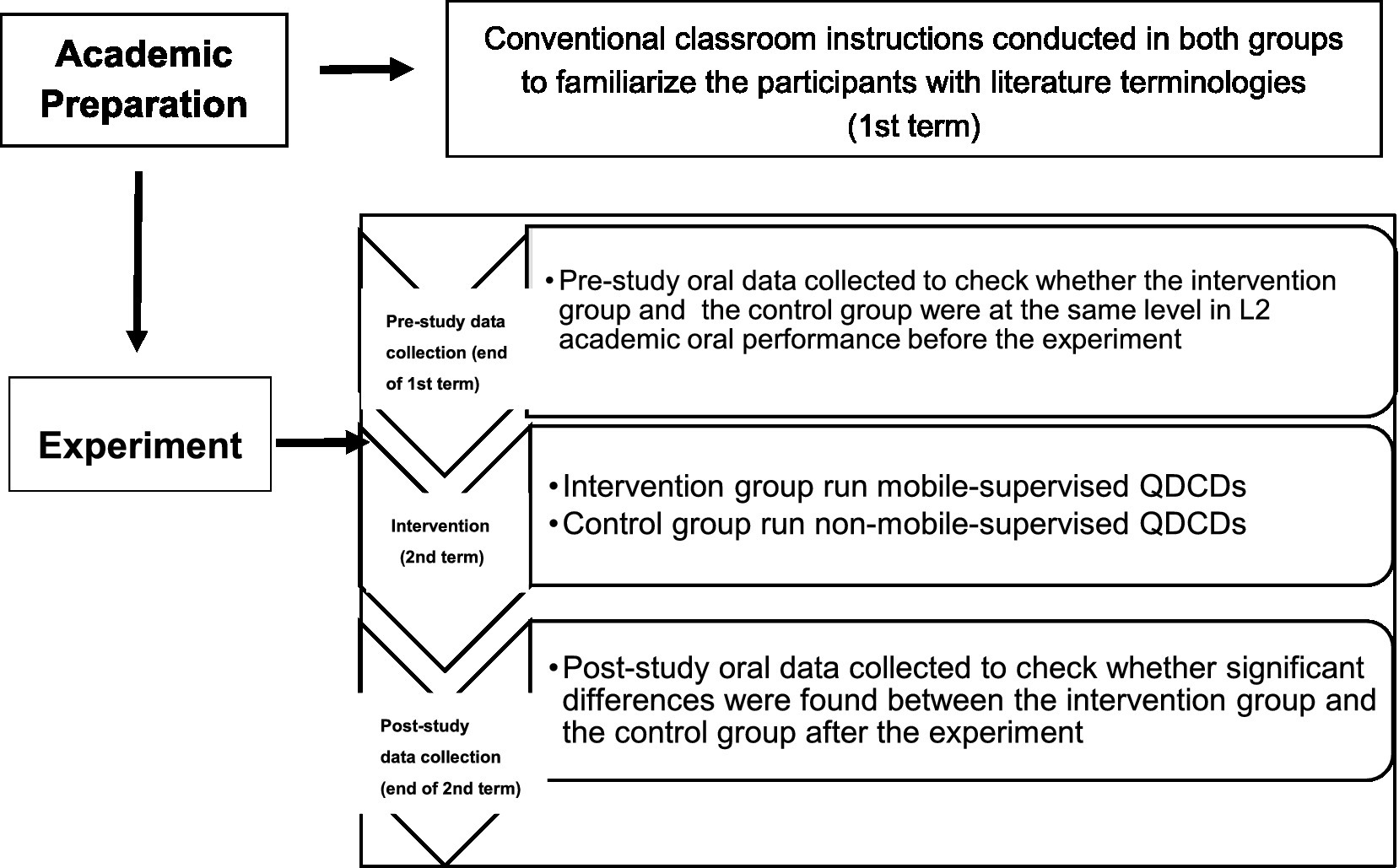 Frontiers Effects of mobile-supervised question-driven collaborative dialogues on EFL learners' communication strategy use and academic oral English performance16 abril 2025
Frontiers Effects of mobile-supervised question-driven collaborative dialogues on EFL learners' communication strategy use and academic oral English performance16 abril 2025
você pode gostar
-
 PROJETO MOVIMENTAR CATALÃO: Pessoas acima de 60 anos terão aulas gratuitas de ginástica e xadrez em projeto coordenado pela Ação Social da Prefeitura de Catalão - Prefeitura Municipal de Catalão16 abril 2025
PROJETO MOVIMENTAR CATALÃO: Pessoas acima de 60 anos terão aulas gratuitas de ginástica e xadrez em projeto coordenado pela Ação Social da Prefeitura de Catalão - Prefeitura Municipal de Catalão16 abril 2025 -
Confirmed - CK III - CK3 - Gameplay - Holy orders not actually participating in crusades.16 abril 2025
-
 Quadro Decorativo Infantil Urso Panda - 4939g216 abril 2025
Quadro Decorativo Infantil Urso Panda - 4939g216 abril 2025 -
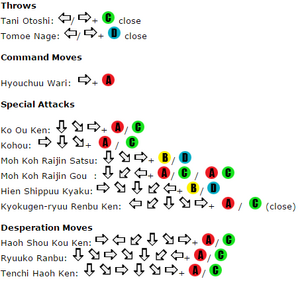 The King of Fighters '98 UMFE/Ryo Sakazaki - Dream Cancel Wiki16 abril 2025
The King of Fighters '98 UMFE/Ryo Sakazaki - Dream Cancel Wiki16 abril 2025 -
 Sylvie Laufeydottir, Marvel Cinematic Universe Wiki16 abril 2025
Sylvie Laufeydottir, Marvel Cinematic Universe Wiki16 abril 2025 -
 Bendy and the Dark Revival16 abril 2025
Bendy and the Dark Revival16 abril 2025 -
 3D file Minecraft Creeper Head Creeper Box Keeper 📦・Model to download and 3D print・Cults16 abril 2025
3D file Minecraft Creeper Head Creeper Box Keeper 📦・Model to download and 3D print・Cults16 abril 2025 -
Weatherford Park Beige Polyester Fabric Dual Power Reclining Sofa - Rooms To Go16 abril 2025
-
sova Pearl Mid Doors, 2 Alt #recondart #sovalineup #valorantlineup #v16 abril 2025
-
 California Rockhounding - 6 Places to Dig for Gemstones in California - Geology In16 abril 2025
California Rockhounding - 6 Places to Dig for Gemstones in California - Geology In16 abril 2025


