TeamTNT Script Employed to Grab AWS Credentials - Cado Security
Por um escritor misterioso
Last updated 16 abril 2025
TeamTNT script has been employed to target a Confluence vulnerability that grabs AWS credentials including those from ECS.

Case Study Continued: Responding to an Attack in AWS - Cado Security
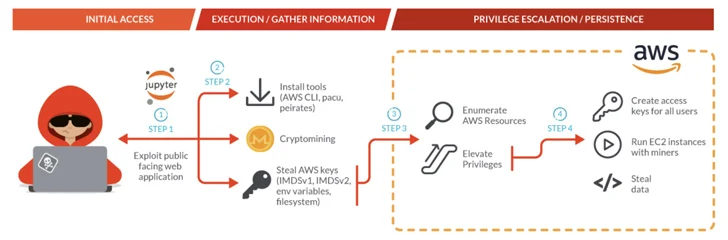
SCARLETEEL Cryptojacking Campaign Exploiting AWS Fargate in Ongoing Campaign

TeamTNT Script Employed to Grab AWS Credentials - Cado Security

Previously Undiscovered TeamTNT Payload Recently Surfaced - Cado Security
TeamTNT Script Employed to Grab AWS Credentials - Cado Security

Cloud Forensics and Incident Response Training.pdf

Resources for Investigating Cloud and Container Penetration Testing Tools - Cado Security
TeamTNT Targets Kubernetes, Nearly 50,000 IPs Compromised in Worm-like Attack
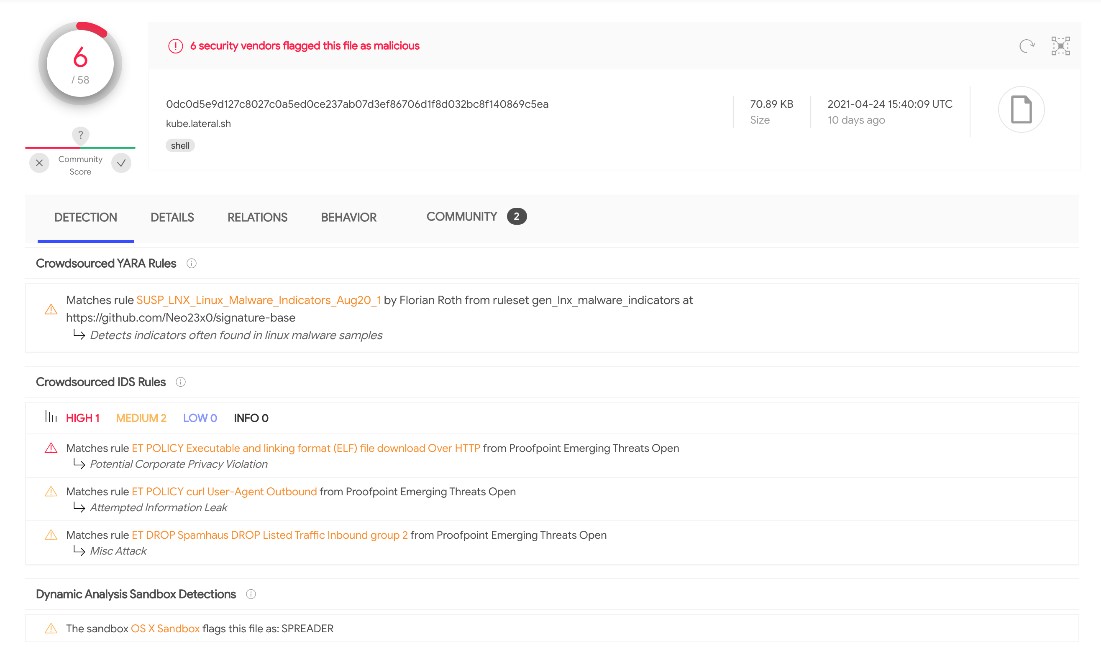
Malicious Shell Script Steals Cloud Credentials
Recomendado para você
-
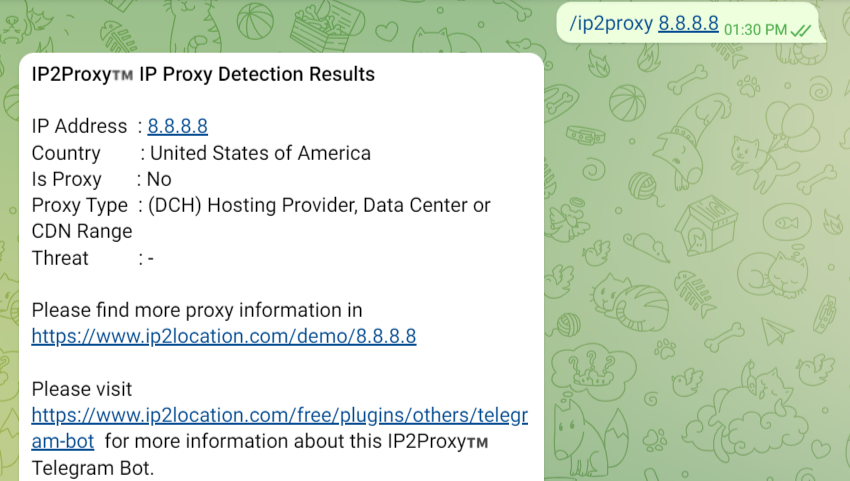 Telegram bot for IP Geolocation16 abril 2025
Telegram bot for IP Geolocation16 abril 2025 -
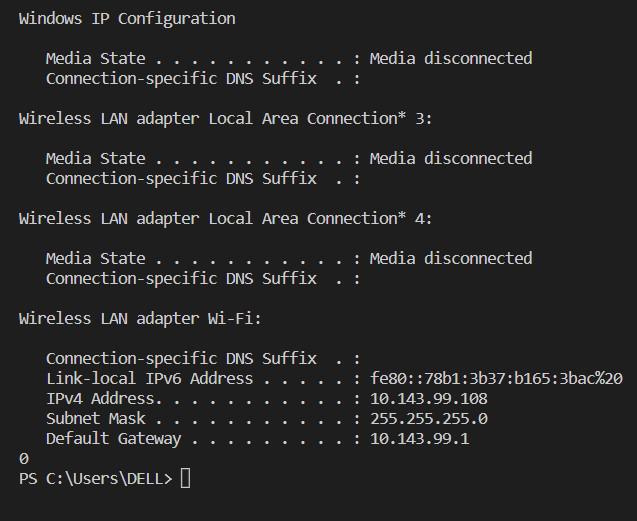 Python program to find IP Address - GeeksforGeeks16 abril 2025
Python program to find IP Address - GeeksforGeeks16 abril 2025 -
 Ip Location Plugins, Code & Scripts16 abril 2025
Ip Location Plugins, Code & Scripts16 abril 2025 -
GitHub - AstroBolo/Ducky-IP-Grabber: USB rubber ducky script to pull IPs16 abril 2025
-
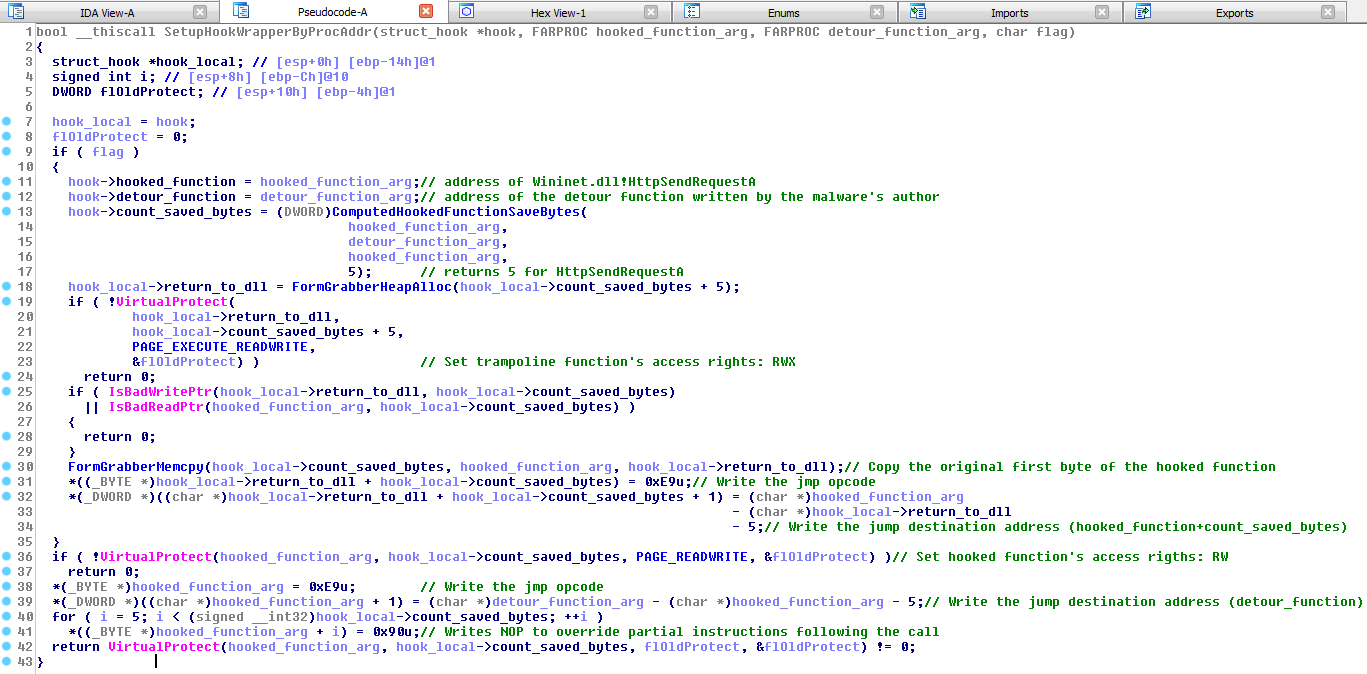 Analyzing a form-grabber malware - Stormshield16 abril 2025
Analyzing a form-grabber malware - Stormshield16 abril 2025 -
 Getting Started with Keyboard Control of Parrot Minidrones - MATLAB & Simulink Example16 abril 2025
Getting Started with Keyboard Control of Parrot Minidrones - MATLAB & Simulink Example16 abril 2025 -
Discord Ip Address Grabber16 abril 2025
-
Roblox-Server-IP-Grabber/script.lua at main · ccxmIcal/Roblox-Server-IP- Grabber · GitHub16 abril 2025
-
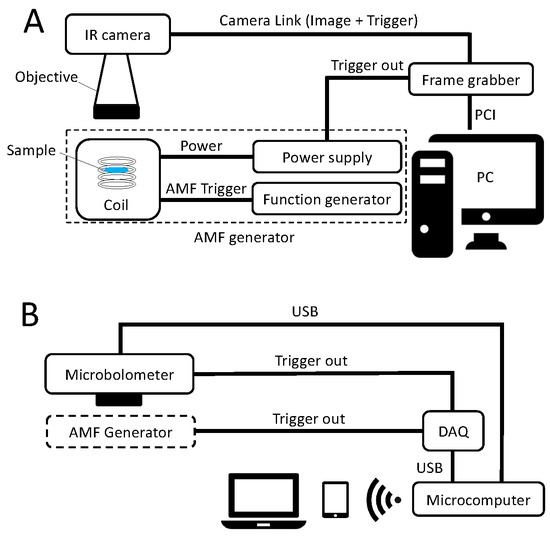 Nanomaterials, Free Full-Text16 abril 2025
Nanomaterials, Free Full-Text16 abril 2025 -
 Technical support scam - Wikipedia16 abril 2025
Technical support scam - Wikipedia16 abril 2025
você pode gostar
-
 Honzuki no Gekokujou - Fanatics Times Two (Doujinshi) - MangaDex16 abril 2025
Honzuki no Gekokujou - Fanatics Times Two (Doujinshi) - MangaDex16 abril 2025 -
 Aesthetic Instagram GIF Recommendations, Gallery posted by syifa.16 abril 2025
Aesthetic Instagram GIF Recommendations, Gallery posted by syifa.16 abril 2025 -
 Pokemon Let's Go Shiny Moltres 6IV-AV Trained – Pokemon4Ever16 abril 2025
Pokemon Let's Go Shiny Moltres 6IV-AV Trained – Pokemon4Ever16 abril 2025 -
 All Star Tower Defence Tier List16 abril 2025
All Star Tower Defence Tier List16 abril 2025 -
 Korean-style french fries corn dog (Gamja-hotdog: 감자핫도그) recipe by Maangchi16 abril 2025
Korean-style french fries corn dog (Gamja-hotdog: 감자핫도그) recipe by Maangchi16 abril 2025 -
 Bom Dia MT Delegação do Palmeiras chegou ontem a noite para o16 abril 2025
Bom Dia MT Delegação do Palmeiras chegou ontem a noite para o16 abril 2025 -
Você não é um fracassado por não ter realizado o primeiro sonho da sua vida16 abril 2025
-
 Conheça o Dublador do OKUYASU - JOJO DUBLADO - Assim Falava Rohan16 abril 2025
Conheça o Dublador do OKUYASU - JOJO DUBLADO - Assim Falava Rohan16 abril 2025 -
How to get a mod menu in GTA 5 #gta #gta5 #bmw #car #gtaonline16 abril 2025
-
 BEST CHARACTERS TIER LIST !! EVERY ATTRIBUTE16 abril 2025
BEST CHARACTERS TIER LIST !! EVERY ATTRIBUTE16 abril 2025

