Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 16 abril 2025
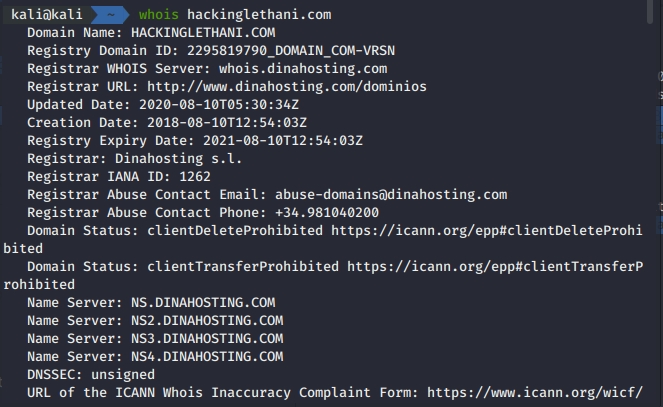
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Iranian hacker claims he acted alone in stealing digital SSL certificates, Hacking

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting
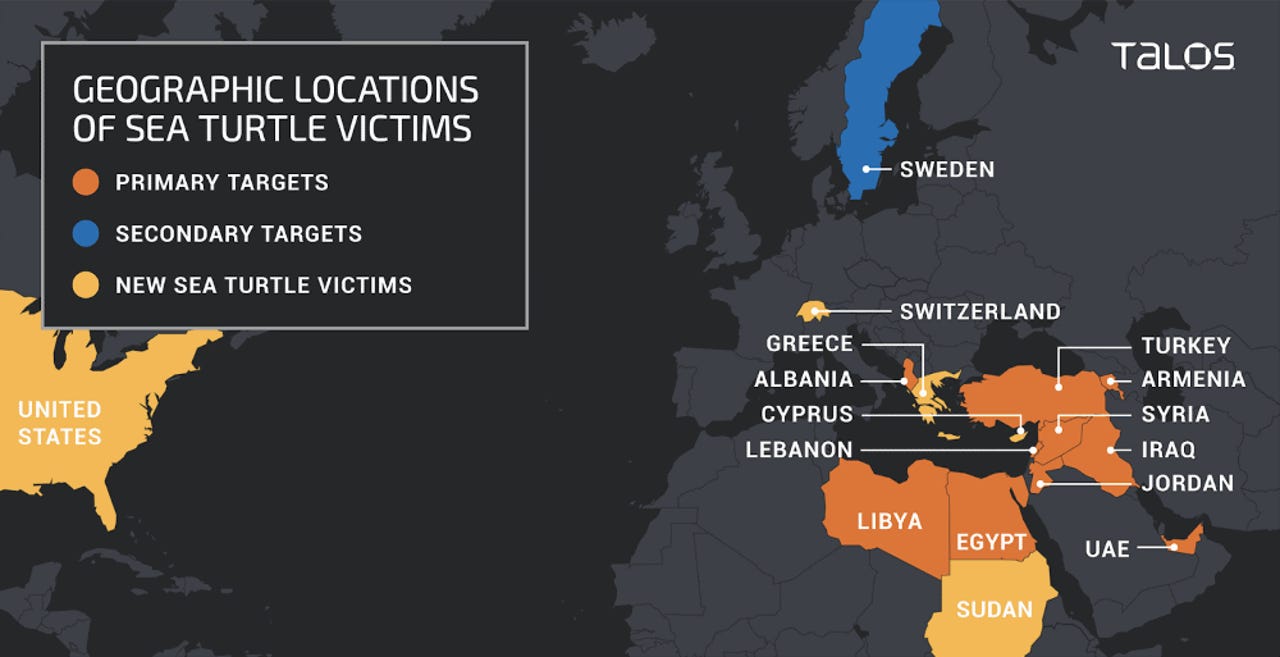
Hackers breached Greece's top-level domain registrar

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Connecting All the World's Users in an Open Way: Decentralized Authentication with Brooklyn Zelenka

Infrastructure Hacking: DNS Protocol II » Hacking Lethani

Killnet Claim They've Stolen Employee Data from Lockheed Martin

Hackbun

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)
Recomendado para você
-
WebRank Whois Lookup16 abril 2025
-
 What Is Whois Lookup And How Can It Help You? - Monsterhost16 abril 2025
What Is Whois Lookup And How Can It Help You? - Monsterhost16 abril 2025 -
 Use WHOIS Lookup to Know Who Owns A Domain16 abril 2025
Use WHOIS Lookup to Know Who Owns A Domain16 abril 2025 -
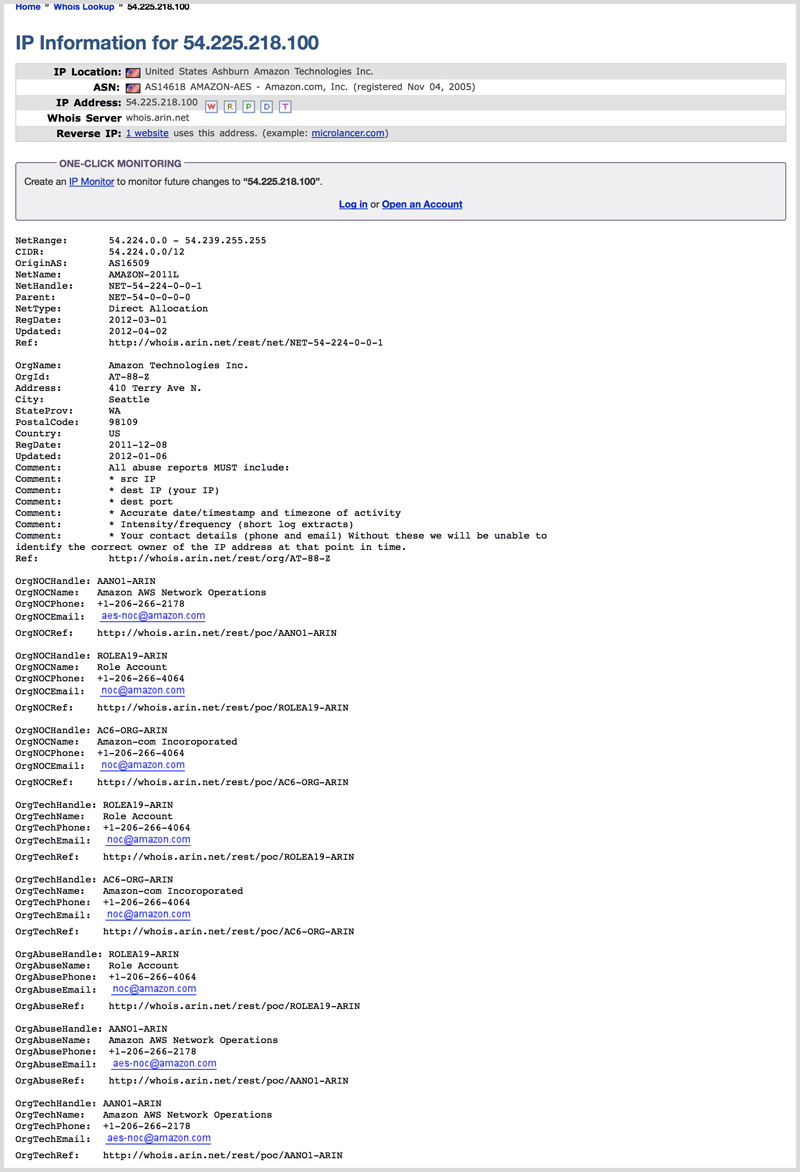 How to use the Whois Lookup Tool – Envato Author Help Center16 abril 2025
How to use the Whois Lookup Tool – Envato Author Help Center16 abril 2025 -
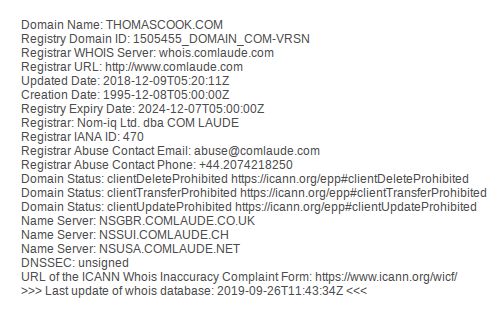 Nixintel Open Source Intelligence & Investigations Search Tip16 abril 2025
Nixintel Open Source Intelligence & Investigations Search Tip16 abril 2025 -
 Whois Lookup - Domain Research and Availablity Tool16 abril 2025
Whois Lookup - Domain Research and Availablity Tool16 abril 2025 -
 File:Whois Mushoku Tensei screenshot.png - Wikipedia16 abril 2025
File:Whois Mushoku Tensei screenshot.png - Wikipedia16 abril 2025 -
 Domain Research Suite, Search & Monitor Tools16 abril 2025
Domain Research Suite, Search & Monitor Tools16 abril 2025 -
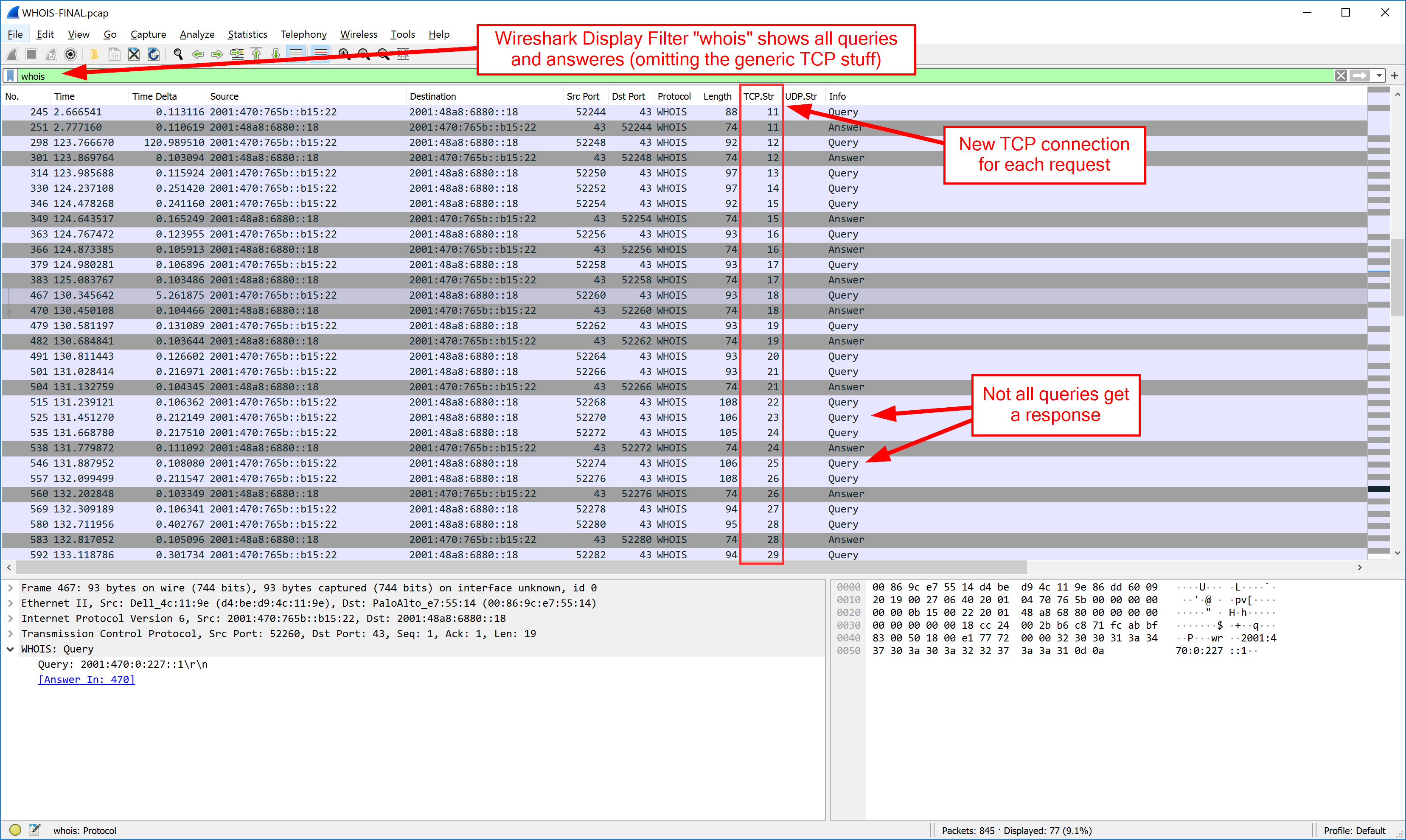 Who is WHOIS Wireshark 02 Display Filter whois16 abril 2025
Who is WHOIS Wireshark 02 Display Filter whois16 abril 2025 -
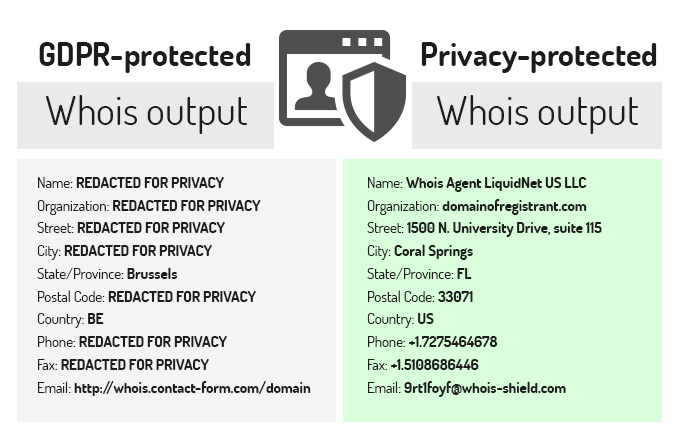 Privacy Protected vs GDPR Protected Whois - the key differences16 abril 2025
Privacy Protected vs GDPR Protected Whois - the key differences16 abril 2025
você pode gostar
-
 Jogos populares portugueses de jovens e adultos16 abril 2025
Jogos populares portugueses de jovens e adultos16 abril 2025 -
 Fantom: Though DeFi-friendly measures show results, FTM remains in limbo - AMBCrypto16 abril 2025
Fantom: Though DeFi-friendly measures show results, FTM remains in limbo - AMBCrypto16 abril 2025 -
 Boruto: Naruto Next Generations revela visual do próximo arco16 abril 2025
Boruto: Naruto Next Generations revela visual do próximo arco16 abril 2025 -
Prueba Una Historia Del Futbol16 abril 2025
-
 Vanderweil Engineers - Company Information, Competitors, News & FAQs16 abril 2025
Vanderweil Engineers - Company Information, Competitors, News & FAQs16 abril 2025 -
 Face decal not appearing on custom Humanoid, + body colour issues - Building Support - Developer Forum16 abril 2025
Face decal not appearing on custom Humanoid, + body colour issues - Building Support - Developer Forum16 abril 2025 -
Jogo Mortal Kombat XL - ps4 (seminovo)16 abril 2025
-
Berserk (1997) #berserk #retro #halloween16 abril 2025
-
 Po/Slendytubbies 3, Slendytubbies Wiki16 abril 2025
Po/Slendytubbies 3, Slendytubbies Wiki16 abril 2025 -
 Episode 8 - Demon Slayer: Kimetsu no Yaiba Swordsmith Village Arc16 abril 2025
Episode 8 - Demon Slayer: Kimetsu no Yaiba Swordsmith Village Arc16 abril 2025


