Malware analysis
Por um escritor misterioso
Last updated 15 abril 2025

GPT's Journey into Malware Analysis - Check Point Blog

Malware Analysis: SharkBot
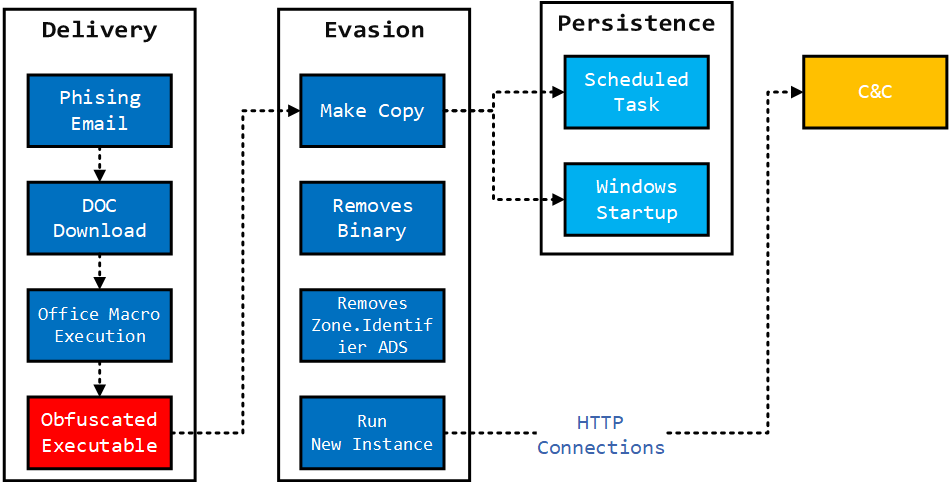
Advanced Windows Malware Analysis - Acquiring Memory Artifacts

Malware Analysis: Steps & Examples - CrowdStrike

How To Set Up Malware Analysis Environment? - The Sec Master
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+
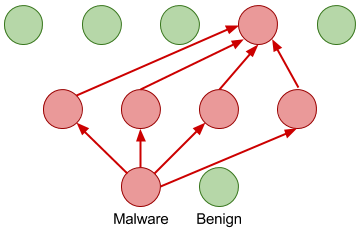
Malware Detection in Executables Using Neural Networks

11 Best Malware Analysis Tools and Their Features

Must Have Free Resources for Malware Analysis
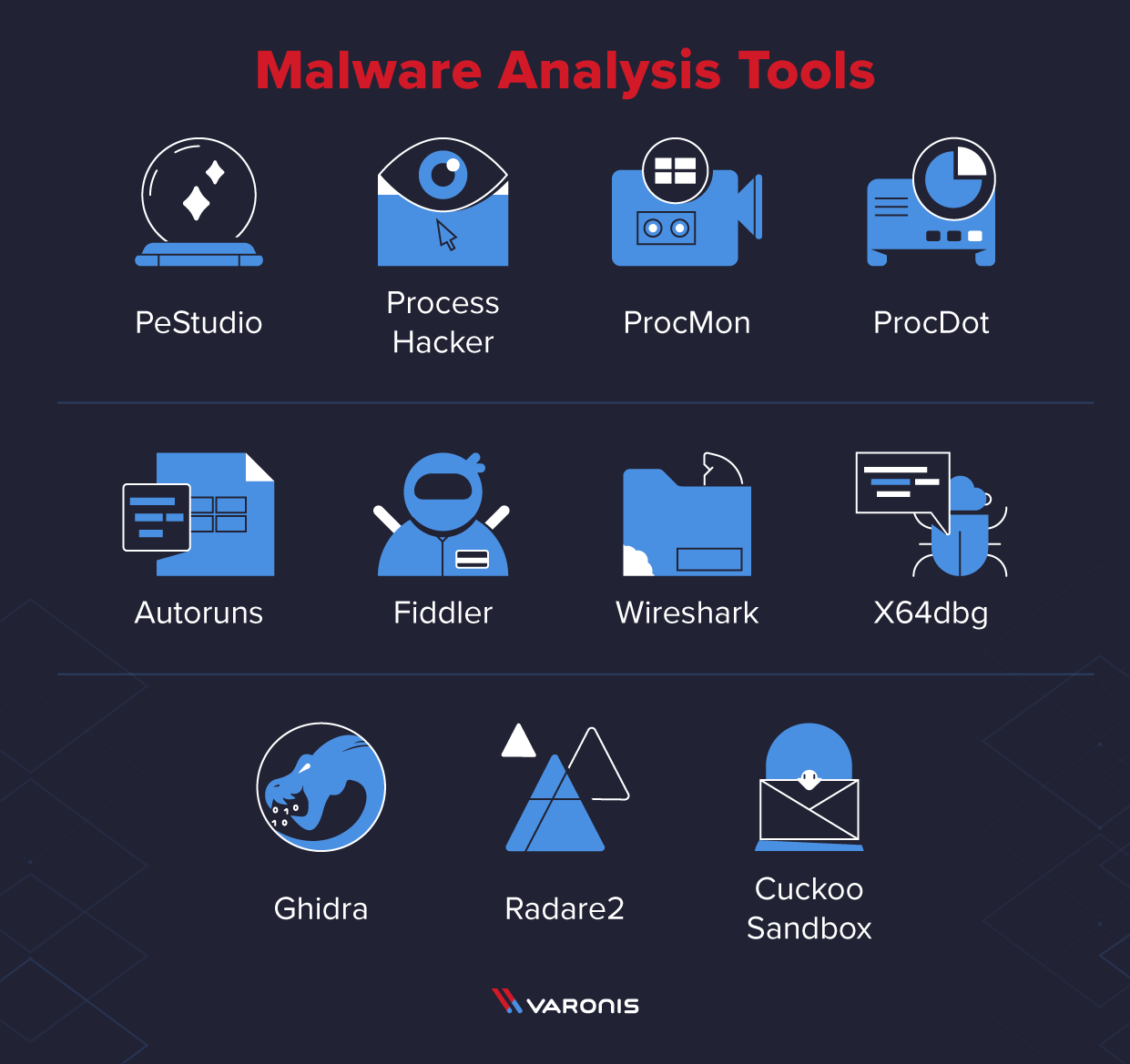
11 Best Malware Analysis Tools and Their Features

Malware Analysis Benefits Incident Response
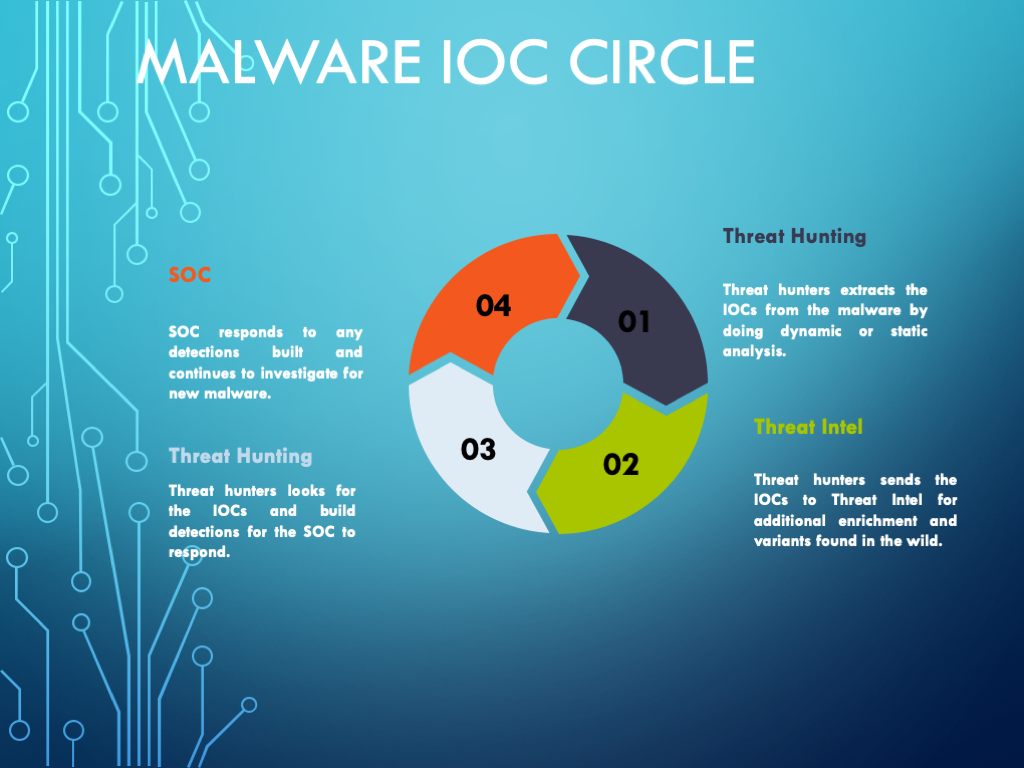
Malware Analysis Framework v1.0

Malware Analysis - What is, Benefits & Types (Easily Explained)

The different types of Malware Analysis, by Dunst Consulting
Recomendado para você
-
![Download Free Roblox FPS Unlocker in 2023 [OFFICIAL]](https://fpsunlocker.net/img/frame.png) Download Free Roblox FPS Unlocker in 2023 [OFFICIAL]15 abril 2025
Download Free Roblox FPS Unlocker in 2023 [OFFICIAL]15 abril 2025 -
 How to Download & Play Roblox for Free on Any Platform15 abril 2025
How to Download & Play Roblox for Free on Any Platform15 abril 2025 -
 How To Play Roblox With a Controller on a PC15 abril 2025
How To Play Roblox With a Controller on a PC15 abril 2025 -
 How To Download Roblox To Your PC (2022)15 abril 2025
How To Download Roblox To Your PC (2022)15 abril 2025 -
 Roblox Apk Download latest version 2.605.660- com.roblox.client15 abril 2025
Roblox Apk Download latest version 2.605.660- com.roblox.client15 abril 2025 -
 Download Roblox 2023.911 - Baixar para PC Grátis15 abril 2025
Download Roblox 2023.911 - Baixar para PC Grátis15 abril 2025 -
Hydrogen Executor [Latest Version]15 abril 2025
-
 The Roblox phenomenon: The sandbox with 90 million active users15 abril 2025
The Roblox phenomenon: The sandbox with 90 million active users15 abril 2025 -
 How to install Roblox Player and Studio on a Chromebook15 abril 2025
How to install Roblox Player and Studio on a Chromebook15 abril 2025 -
 Roblox - Apps on Google Play15 abril 2025
Roblox - Apps on Google Play15 abril 2025
você pode gostar
-
big-ibex269: floresta encantada, criança, flores15 abril 2025
-
 Jogo De Baralho PVC Caixa Metálica Moment EM OFERTA15 abril 2025
Jogo De Baralho PVC Caixa Metálica Moment EM OFERTA15 abril 2025 -
 DRAGON BALL Z KAKAROT - DLC BARDOCK │ O FILME - JOGO COMPLETO15 abril 2025
DRAGON BALL Z KAKAROT - DLC BARDOCK │ O FILME - JOGO COMPLETO15 abril 2025 -
violao #guitar #music #musica #hino #gospel #cifra #cifras15 abril 2025
-
 Street Fighter 30th Anniversary Collection - Wikipedia15 abril 2025
Street Fighter 30th Anniversary Collection - Wikipedia15 abril 2025 -
ISEKAI one turn kill neesan ✓ EP 7 - video Dailymotion15 abril 2025
-
Steam Workshop::Shogi15 abril 2025
-
 32 Desenho Cavalos para Colorir e Imprimir - Colorir Tudo15 abril 2025
32 Desenho Cavalos para Colorir e Imprimir - Colorir Tudo15 abril 2025 -
 Moletom Piet x Oakley Icons Crewneck Preto Desbotado - NewSkull15 abril 2025
Moletom Piet x Oakley Icons Crewneck Preto Desbotado - NewSkull15 abril 2025 -
 Slime Rancher Game Free Download15 abril 2025
Slime Rancher Game Free Download15 abril 2025