Malware analysis Malicious activity
Por um escritor misterioso
Last updated 10 abril 2025

Malware Analysis: Steps & Examples - CrowdStrike

Complex 'NKAbuse' Malware Uses Blockchain to Hide on Linux, IoT Machines

Malware Analysis: Steps & Examples - CrowdStrike
Interactive Online Malware Sandbox
Malware analysis Malicious activity
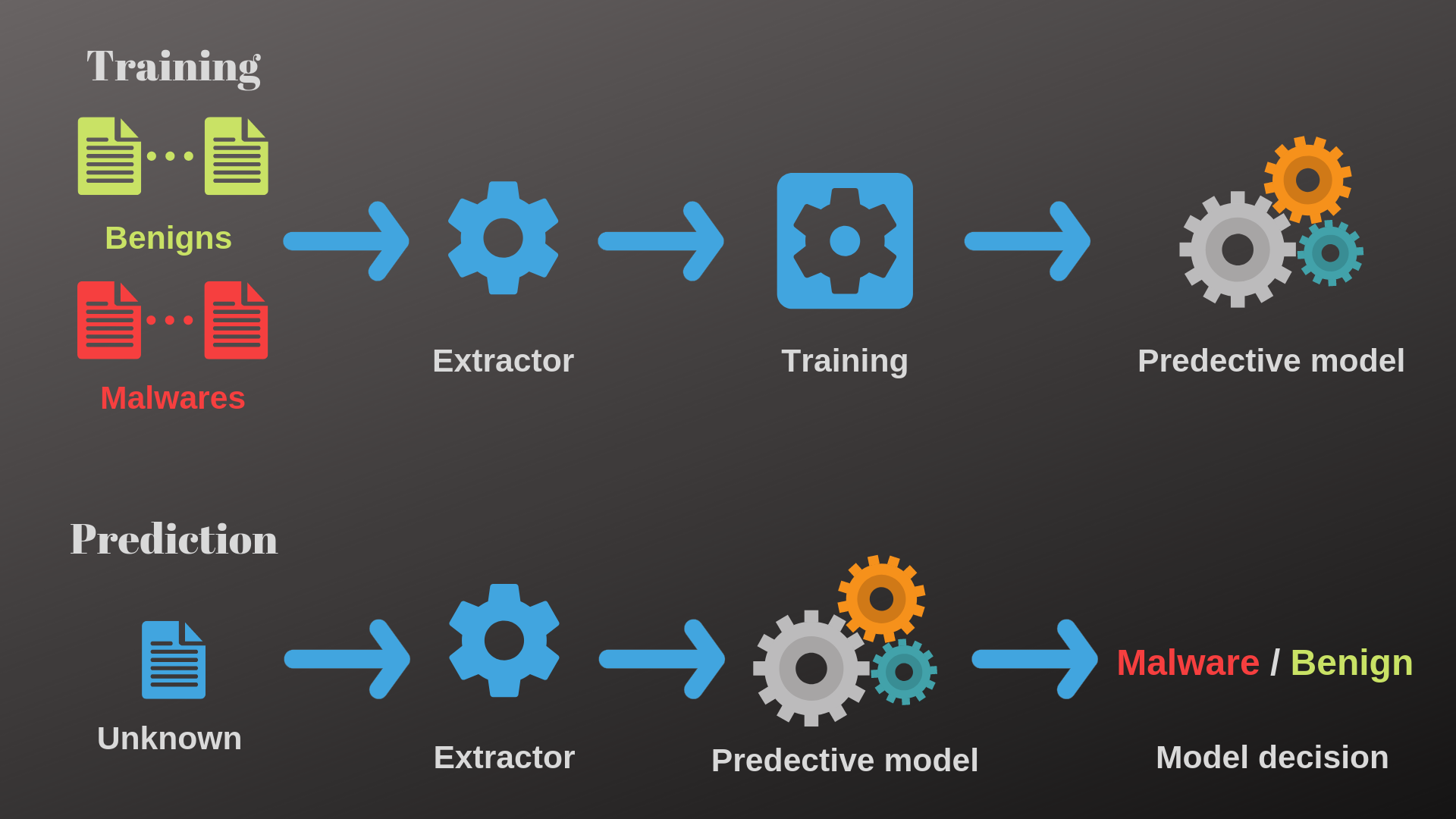
Feature Extraction and Detection of Malwares Using Machine Learning

Malware analysis Program_Install_and_Uninstall Malicious activity
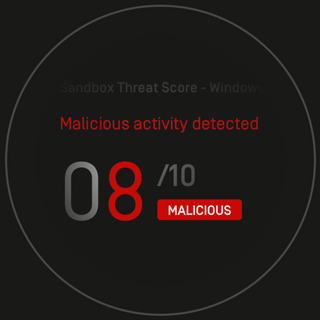
MetaDefender Cloud Advanced threat prevention and detection
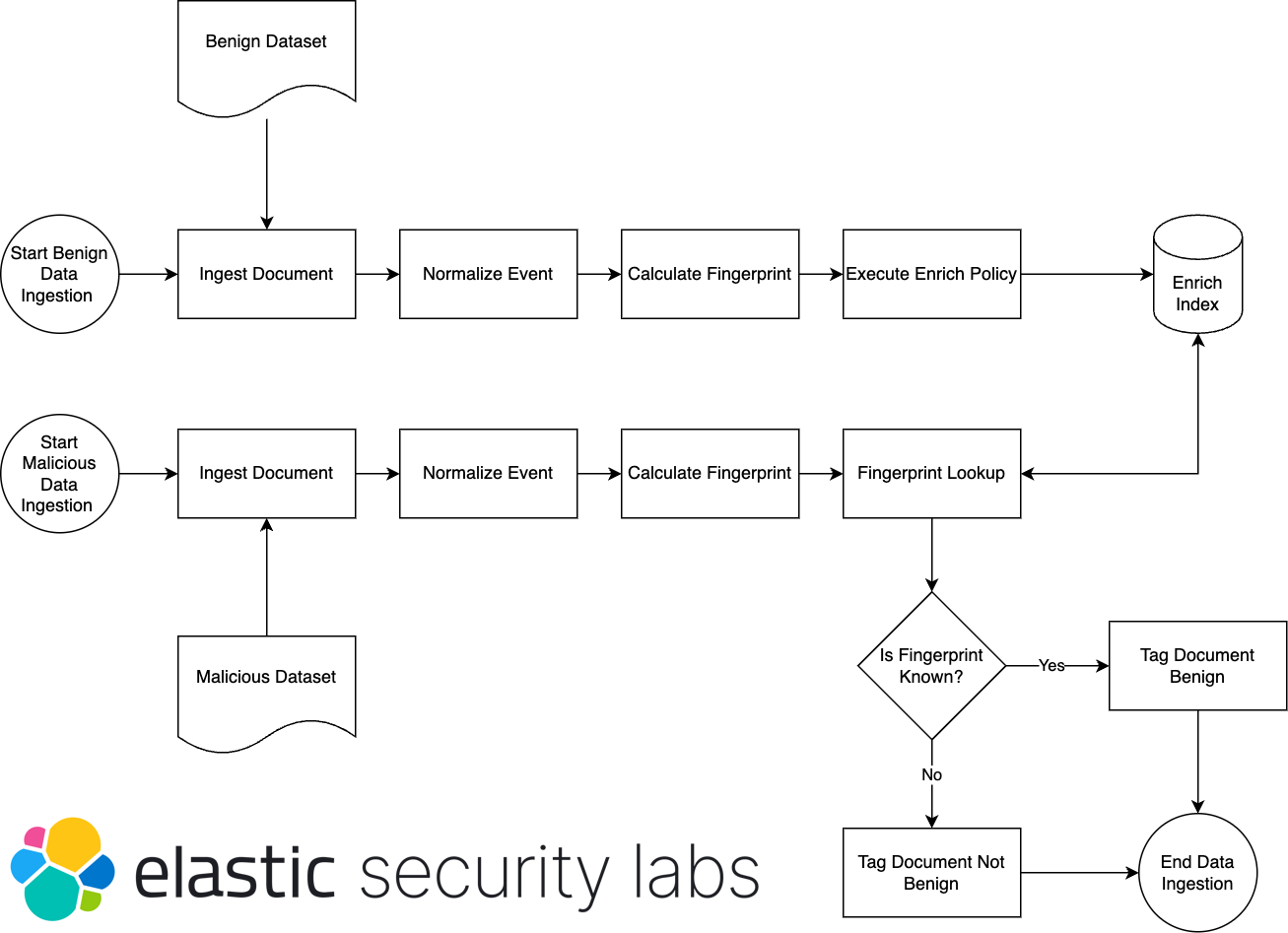
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

How to Do Malware Analysis?
Recomendado para você
-
 Steam Unlocked: A New Game Downloading Website10 abril 2025
Steam Unlocked: A New Game Downloading Website10 abril 2025 -
 Unlock the World of Free PC Gaming! by Steam Unlocked - Issuu10 abril 2025
Unlock the World of Free PC Gaming! by Steam Unlocked - Issuu10 abril 2025 -
 Is SteamUnlocked Safe? 5 Secure Ways to Use It Without Risks10 abril 2025
Is SteamUnlocked Safe? 5 Secure Ways to Use It Without Risks10 abril 2025 -
 Steamunlocked gets greater download speeds : r/PiratedGames10 abril 2025
Steamunlocked gets greater download speeds : r/PiratedGames10 abril 2025 -
 Is Steam unlocked legit and safe? • TechBriefly10 abril 2025
Is Steam unlocked legit and safe? • TechBriefly10 abril 2025 -
 Pin on SteamUnlocked10 abril 2025
Pin on SteamUnlocked10 abril 2025 -
 SteamUnlocked — Grand Theft Auto IV: The Complete Edition - Steam Unlocked - Medium10 abril 2025
SteamUnlocked — Grand Theft Auto IV: The Complete Edition - Steam Unlocked - Medium10 abril 2025 -
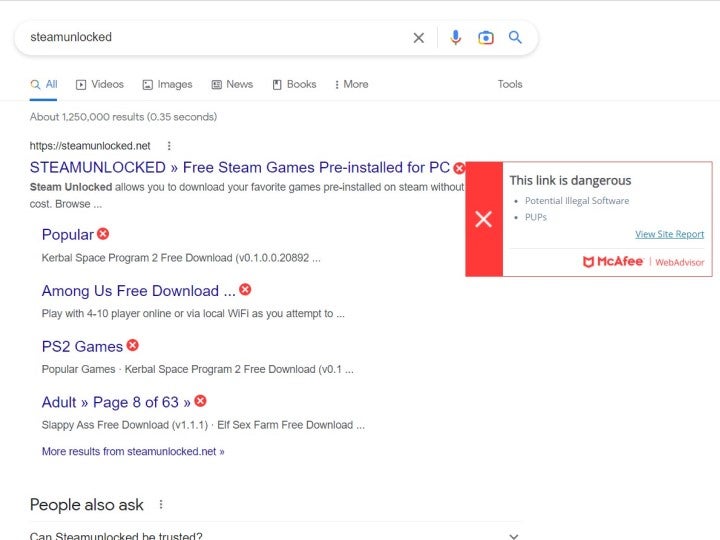 Is SteamUnlocked Safe and Legit? (It's Not) - VGKAMI10 abril 2025
Is SteamUnlocked Safe and Legit? (It's Not) - VGKAMI10 abril 2025 -
 Rogerio 'W. Download (Incl. Multiplayer) STEAMUNLOCKED steamunlocked.net -strike-1-6-free-pe-download/ y Se10 abril 2025
Rogerio 'W. Download (Incl. Multiplayer) STEAMUNLOCKED steamunlocked.net -strike-1-6-free-pe-download/ y Se10 abril 2025 -
steam unlocked download|TikTok Search10 abril 2025
você pode gostar
-
 Plotagem Projektit Valokuvia, videoita, logoja, kuvituskuvia ja10 abril 2025
Plotagem Projektit Valokuvia, videoita, logoja, kuvituskuvia ja10 abril 2025 -
 Star Wars: A Ascensão Skywalker homenageia trilogia clássica em10 abril 2025
Star Wars: A Ascensão Skywalker homenageia trilogia clássica em10 abril 2025 -
 Anime Summer Time Render Shinpei Ajiro Cosplay Wig Black Hair Shoulder-length Shin-chan Summertime Render Free Wig Cap Props - AliExpress10 abril 2025
Anime Summer Time Render Shinpei Ajiro Cosplay Wig Black Hair Shoulder-length Shin-chan Summertime Render Free Wig Cap Props - AliExpress10 abril 2025 -
 Pelúcia Choo-choo Charles Roblox Jogo Trem Vermelho Boneco10 abril 2025
Pelúcia Choo-choo Charles Roblox Jogo Trem Vermelho Boneco10 abril 2025 -
![PS Plus Essential de agosto pode ter Tony Hawk's 1+2 e mais [rumor]](https://meups.com.br/wp-content/uploads/2022/07/PS-Plus-Essential-de-Agosto-1.jpg) PS Plus Essential de agosto pode ter Tony Hawk's 1+2 e mais [rumor]10 abril 2025
PS Plus Essential de agosto pode ter Tony Hawk's 1+2 e mais [rumor]10 abril 2025 -
 7692 - Fazendinha - 40 peças Memória em Madeira10 abril 2025
7692 - Fazendinha - 40 peças Memória em Madeira10 abril 2025 -
 Dinosaucers, o Planeta dos Dinossauros (Abertura dublada)10 abril 2025
Dinosaucers, o Planeta dos Dinossauros (Abertura dublada)10 abril 2025 -
 Mahoutsukai Reimeiki DVD (魔法使い黎明期) (Ep 1-12 end) (English Dub)10 abril 2025
Mahoutsukai Reimeiki DVD (魔法使い黎明期) (Ep 1-12 end) (English Dub)10 abril 2025 -
 Cristiano Ronaldo's FIFA 23 rating slashed after move to Saudi10 abril 2025
Cristiano Ronaldo's FIFA 23 rating slashed after move to Saudi10 abril 2025 -
 Garten Of Banban Plush Toys, 6 Pieces Of Cute Banned Garden Plush Monsters For Kids, Jumbo Josh Opila Bird Plush Toys, Suitable For Children Fan Gifts10 abril 2025
Garten Of Banban Plush Toys, 6 Pieces Of Cute Banned Garden Plush Monsters For Kids, Jumbo Josh Opila Bird Plush Toys, Suitable For Children Fan Gifts10 abril 2025
