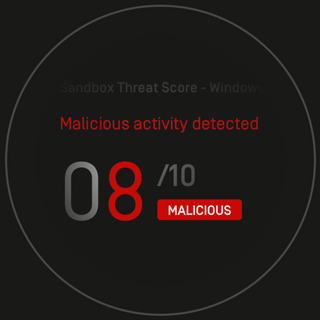
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 14 abril 2025
Interactive Online Malware Sandbox

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware analysis index.html Malicious activity

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

AlienVault - Open Threat Exchange

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Malware analysis metasploit.bat Malicious activity

Malware analysis mykey_.rar Malicious activity

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Dynamic malware analysis [34]
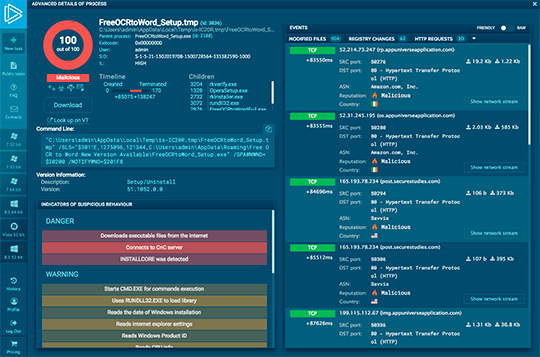
Interactive Online Malware Sandbox
MetaDefender Cloud Advanced threat prevention and detection

A detailed analysis of the Menorah malware used by APT34
Recomendado para você
-
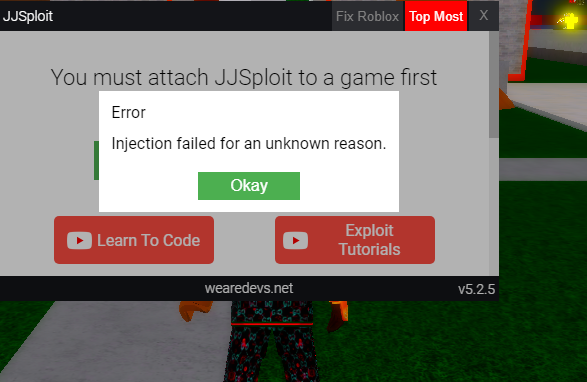
 HOW TO FIX JJSPLOIT IN 2023 UPDATED METHOD! PATCHED OR NOT WORKING AFTER ROBLOX UPDATE!14 abril 2025
HOW TO FIX JJSPLOIT IN 2023 UPDATED METHOD! PATCHED OR NOT WORKING AFTER ROBLOX UPDATE!14 abril 2025 -
 Jjsploit install billpoproterdenz1986's Ownd14 abril 2025
Jjsploit install billpoproterdenz1986's Ownd14 abril 2025 -
 Krnl Wearedevs GIF - Krnl Wearedevs Virus - Discover & Share GIFs14 abril 2025
Krnl Wearedevs GIF - Krnl Wearedevs Virus - Discover & Share GIFs14 abril 2025 -
 Jjsploit Krnl GIF - Jjsploit Krnl Computer - Discover & Share GIFs14 abril 2025
Jjsploit Krnl GIF - Jjsploit Krnl Computer - Discover & Share GIFs14 abril 2025 -
 How To Attach JJSploit To Roblox?, by Jjsploit14 abril 2025
How To Attach JJSploit To Roblox?, by Jjsploit14 abril 2025 -
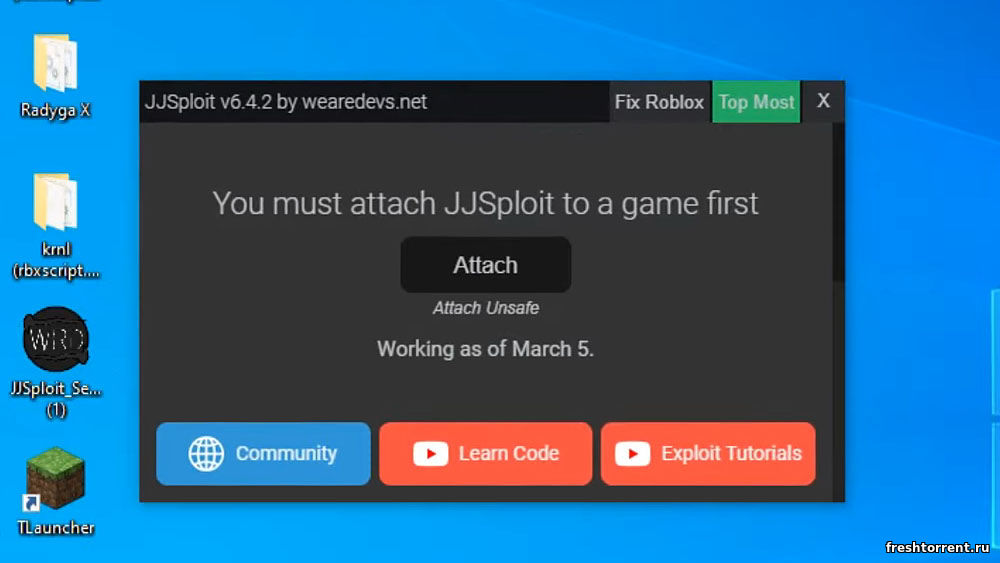 JJSploit Information WeAreDevs, 49% OFF14 abril 2025
JJSploit Information WeAreDevs, 49% OFF14 abril 2025 -
![NOT WORKING] How to fix JJSploit not executing. 07/08/2023](https://i.ytimg.com/vi/3pd8Z6YTJnM/maxresdefault.jpg) NOT WORKING] How to fix JJSploit not executing. 07/08/202314 abril 2025
NOT WORKING] How to fix JJSploit not executing. 07/08/202314 abril 2025 -
 Wearedevs Reviews Read Customer Service Reviews of wearedevs.net14 abril 2025
Wearedevs Reviews Read Customer Service Reviews of wearedevs.net14 abril 2025 -
 Wearedevs Reviews Read Customer Service Reviews of wearedevs.net14 abril 2025
Wearedevs Reviews Read Customer Service Reviews of wearedevs.net14 abril 2025 -
 Roblox Exploits & Hacks & Cheats - WeAreDevs14 abril 2025
Roblox Exploits & Hacks & Cheats - WeAreDevs14 abril 2025
você pode gostar
-
Igloo Flip And Tow 90qt Roller Cooler - White : Target14 abril 2025
-
 Tokyo Revengers Season 2 Release Date, Cast, Story, Episode 114 abril 2025
Tokyo Revengers Season 2 Release Date, Cast, Story, Episode 114 abril 2025 -
 Unown Earrings Pokemon Mini Dangle and Drop Unknown Alphabet14 abril 2025
Unown Earrings Pokemon Mini Dangle and Drop Unknown Alphabet14 abril 2025 -
 Chilam Balam (Boca del Jaguar) : Luis Pinto (El Pinto): Collectibles & Fine Art14 abril 2025
Chilam Balam (Boca del Jaguar) : Luis Pinto (El Pinto): Collectibles & Fine Art14 abril 2025 -
 Bandeira Da Federação Russa No Fundo Do Céu Azul Bandeira De14 abril 2025
Bandeira Da Federação Russa No Fundo Do Céu Azul Bandeira De14 abril 2025 -
 torneio mundial de futebol iraniano 2022 vector bandeira ondulada fixada em um campo de futebol com elementos de design. fase final do torneio mundial de futebol 2022. cores e estilo não oficiais14 abril 2025
torneio mundial de futebol iraniano 2022 vector bandeira ondulada fixada em um campo de futebol com elementos de design. fase final do torneio mundial de futebol 2022. cores e estilo não oficiais14 abril 2025 -
 Size, or How You Rule It? Determining History's Greatest Empire14 abril 2025
Size, or How You Rule It? Determining History's Greatest Empire14 abril 2025 -
 BIONIK Pro Kit for Playstation 5: Powerful 50mm Gaming14 abril 2025
BIONIK Pro Kit for Playstation 5: Powerful 50mm Gaming14 abril 2025 -
 Fortnite Battle Royale Review14 abril 2025
Fortnite Battle Royale Review14 abril 2025 -
 Playstation Plus Essential 12 Meses Assinatura USA - Código Digital - PentaKill Store - Gift Card e Games14 abril 2025
Playstation Plus Essential 12 Meses Assinatura USA - Código Digital - PentaKill Store - Gift Card e Games14 abril 2025
