Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 03 abril 2025

Top 10 Malware Analysis Platforms & Tools
Introducing malware analysis: enhance your cybersecurity triage

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey
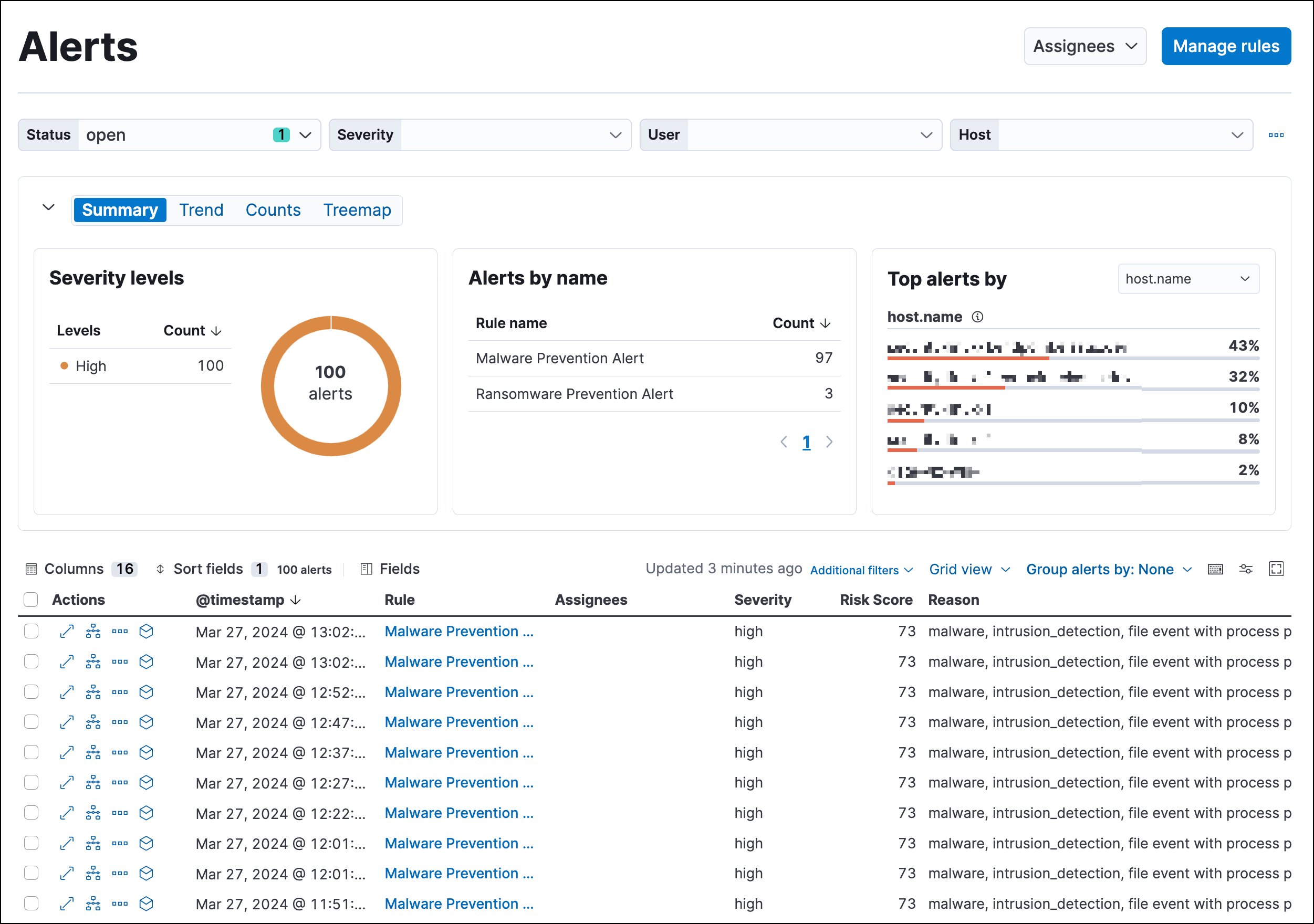
Detections and alerts, Elastic Security Solution [8.11]

How to Detect New Threats via Suspicious Activities

Malware Analysis 101 - Basic Static Analysis

Microsoft 365 Alerting - Detect and React to Threats Instantly

What is Malware? Definition, Types, Prevention - TechTarget

malware analysis

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine
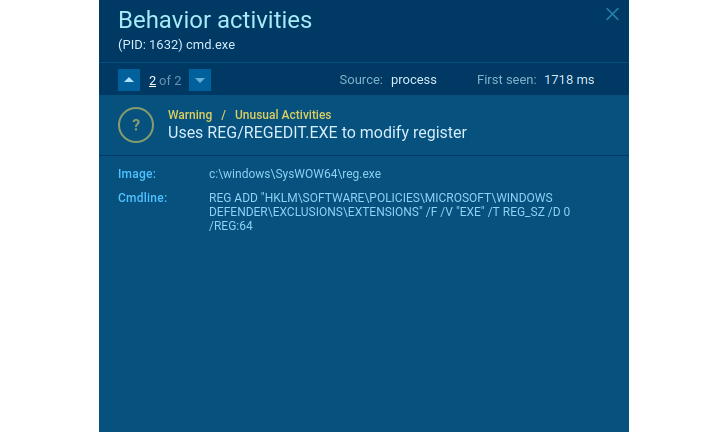
How to Detect New Threats via Suspicious Activities

REMnux toolkit for malware analysis version 7 released - Help Net
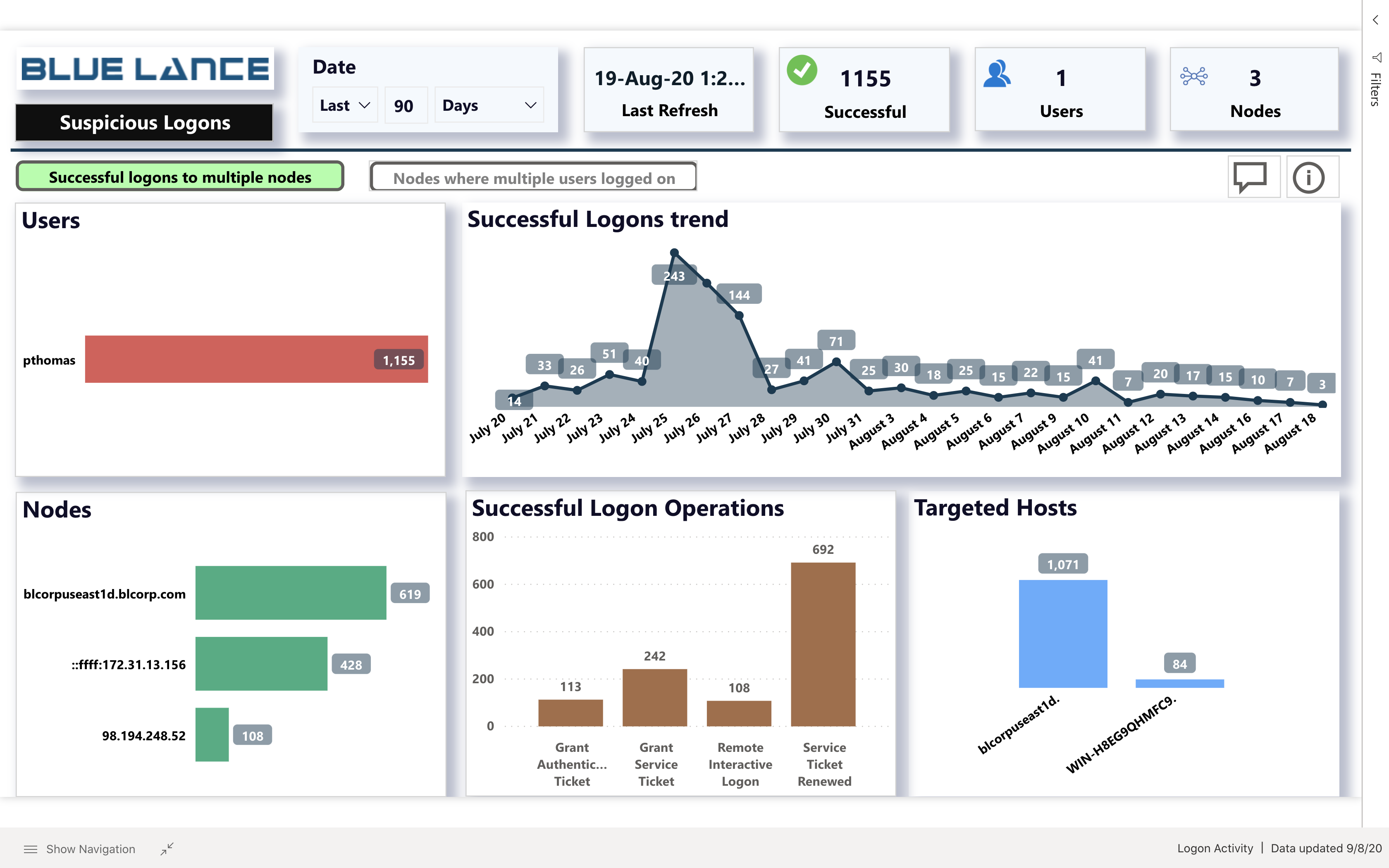
Suspicious Successful Logon Analysis
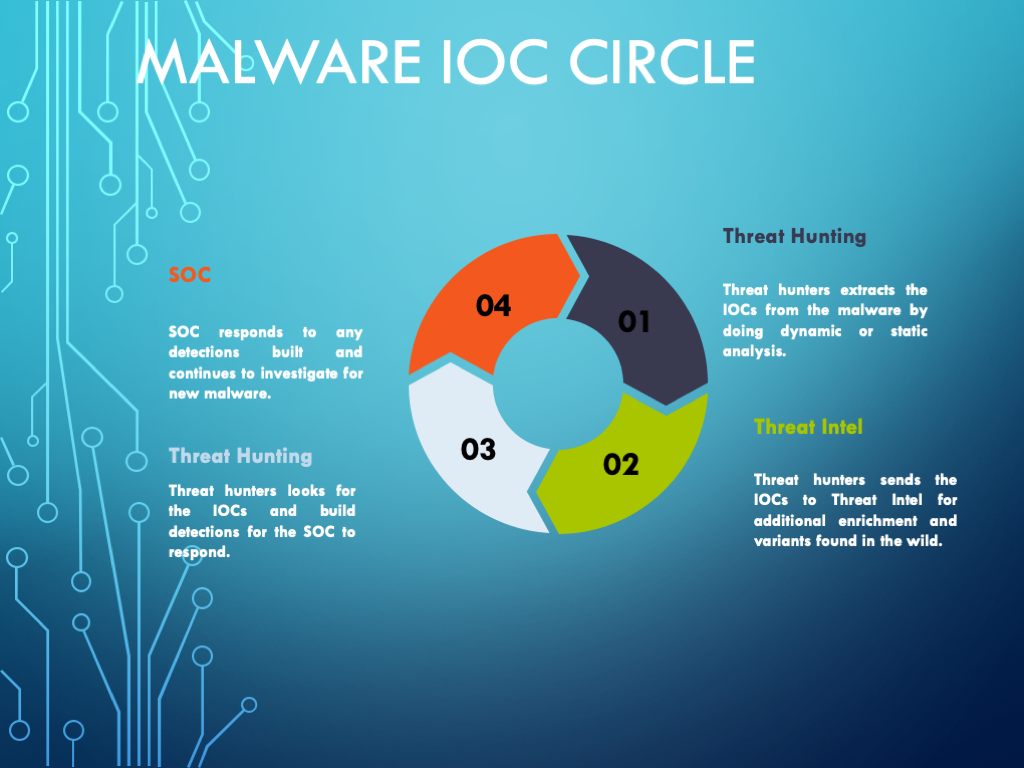
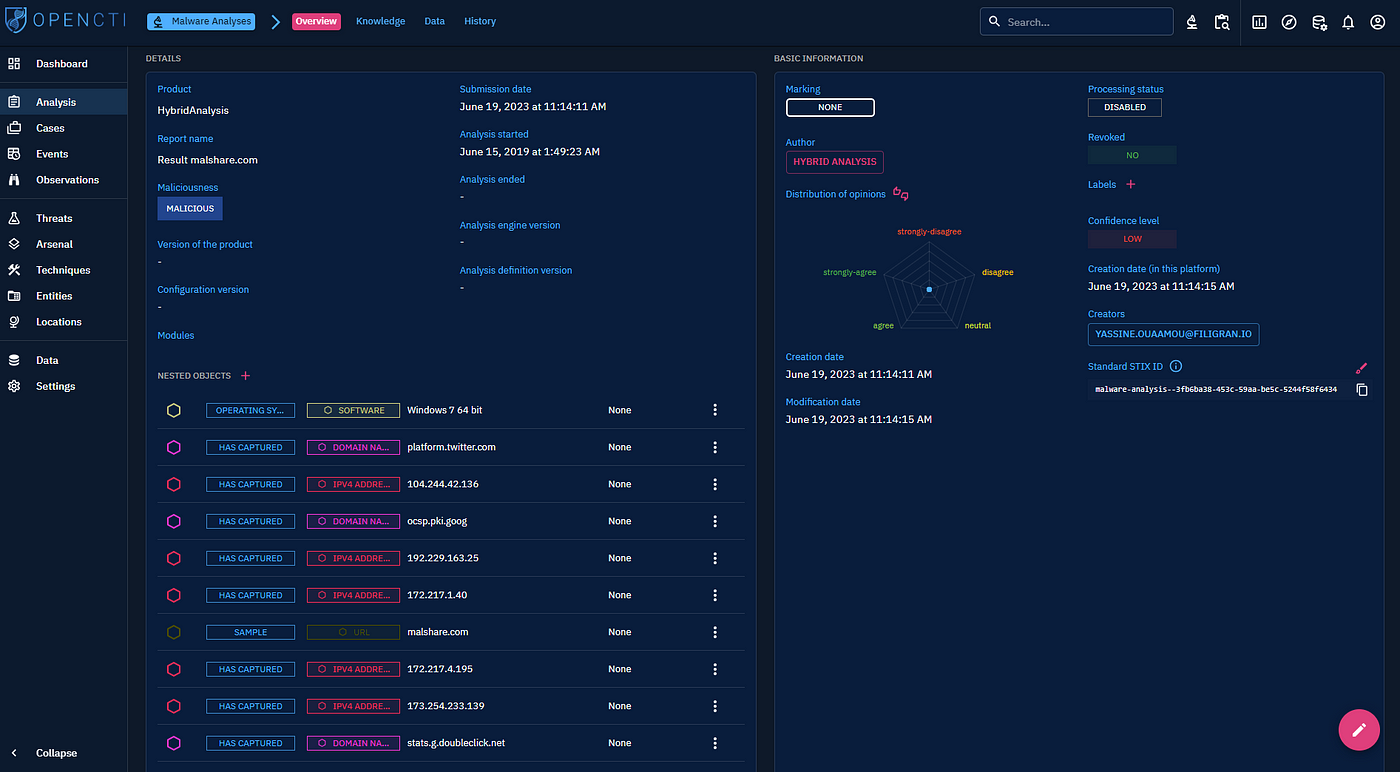
Malware Analysis Framework v1.0

What is Malware Analysis? Types and Stages of Malware Analysis
Recomendado para você
-
WRT - Ever NEED to know your IP ADDRESS? When syncing security cameras & other smart home devices, you sometimes need to re-configure your IP address. Simple go to www.ipchicken.com & it03 abril 2025
-
 Pascal Gujer on X: / : not only showing your remote IP but also your remote port #ipchicken #ipmonkey #identification deanonymize within carrier-grade natted networks :sigh: / X03 abril 2025
Pascal Gujer on X: / : not only showing your remote IP but also your remote port #ipchicken #ipmonkey #identification deanonymize within carrier-grade natted networks :sigh: / X03 abril 2025 -
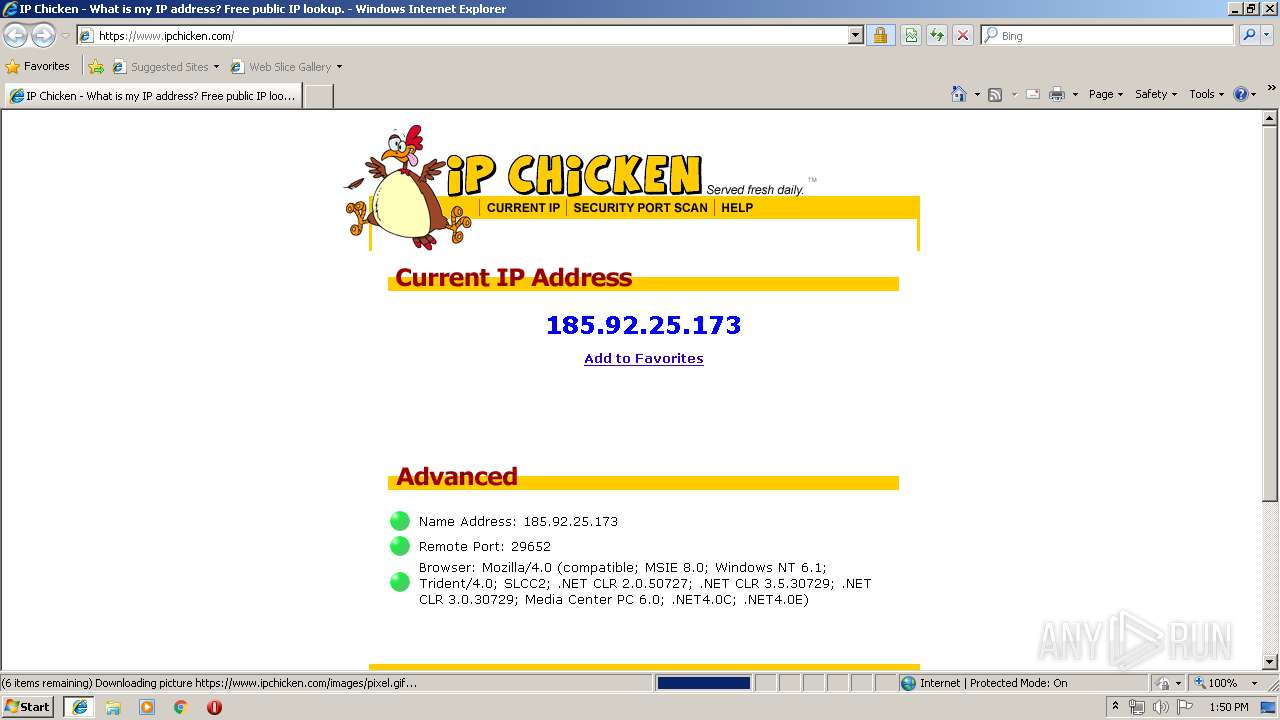
 Access ipchicken.com. IP Chicken - What is my IP address? Free public IP lookup.03 abril 2025
Access ipchicken.com. IP Chicken - What is my IP address? Free public IP lookup.03 abril 2025 -
ipchicken.com - IP Chicken - What is my IP address? Free public IP lookup. - DomainsData03 abril 2025
-
 IP Chicken - What is my IP address Free public IP lookup03 abril 2025
IP Chicken - What is my IP address Free public IP lookup03 abril 2025 -
 HY-VPN – Checking functionality and errors (Linux)03 abril 2025
HY-VPN – Checking functionality and errors (Linux)03 abril 2025 -
 shell - SSH socks proxy via jumphost - Stack Overflow03 abril 2025
shell - SSH socks proxy via jumphost - Stack Overflow03 abril 2025 -
 Heads up on ddoses03 abril 2025
Heads up on ddoses03 abril 2025 -
 Instant Pot Whole Chicken: Whole30, Paleo, Keto, Easy! - Whole Kitchen Sink03 abril 2025
Instant Pot Whole Chicken: Whole30, Paleo, Keto, Easy! - Whole Kitchen Sink03 abril 2025 -
 Assignment #2 debriefing - ppt download03 abril 2025
Assignment #2 debriefing - ppt download03 abril 2025
você pode gostar
-
 Um peão na cidade, Vol. 1 by Charles é Show on Apple Music03 abril 2025
Um peão na cidade, Vol. 1 by Charles é Show on Apple Music03 abril 2025 -
 Jedi, Wookieepedia03 abril 2025
Jedi, Wookieepedia03 abril 2025 -
sonic and shadow ligma|TikTok Search03 abril 2025
-
/arc-anglerfish-arc2-prod-pmn.s3.amazonaws.com/public/KIIHSVY4LJC5PEVXGKWXGN4D4E.jpg) Angels pitcher Tyler Skaggs died of accidental overdose, coroner says03 abril 2025
Angels pitcher Tyler Skaggs died of accidental overdose, coroner says03 abril 2025 -
 Anime Meme Triggered Face GIF03 abril 2025
Anime Meme Triggered Face GIF03 abril 2025 -
 Galloping Games,LLC Crazy A's - Levels 1-6 Package Deal - Phonics Game03 abril 2025
Galloping Games,LLC Crazy A's - Levels 1-6 Package Deal - Phonics Game03 abril 2025 -
 Dango Balango estourado Roblox ID - Roblox music codes03 abril 2025
Dango Balango estourado Roblox ID - Roblox music codes03 abril 2025 -
 TERCERA TEMPORADA DE KORE WA ZOMBIE DESU KA?03 abril 2025
TERCERA TEMPORADA DE KORE WA ZOMBIE DESU KA?03 abril 2025 -
 MEMES HILÁRIOS DE HARRY POTTER! ~~QUEM RIR É TROUXA #REDDIT03 abril 2025
MEMES HILÁRIOS DE HARRY POTTER! ~~QUEM RIR É TROUXA #REDDIT03 abril 2025 -
:format(jpg)/f.elconfidencial.com%2Foriginal%2Fb1a%2Fb42%2F267%2Fb1ab42267123b92c5f9a36f92430ff99.jpg) Este es el significado del nombre elegido por Serena Williams y su marido, Alexis Ohanian, para su segunda hija03 abril 2025
Este es el significado del nombre elegido por Serena Williams y su marido, Alexis Ohanian, para su segunda hija03 abril 2025

