Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Last updated 15 abril 2025

[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]
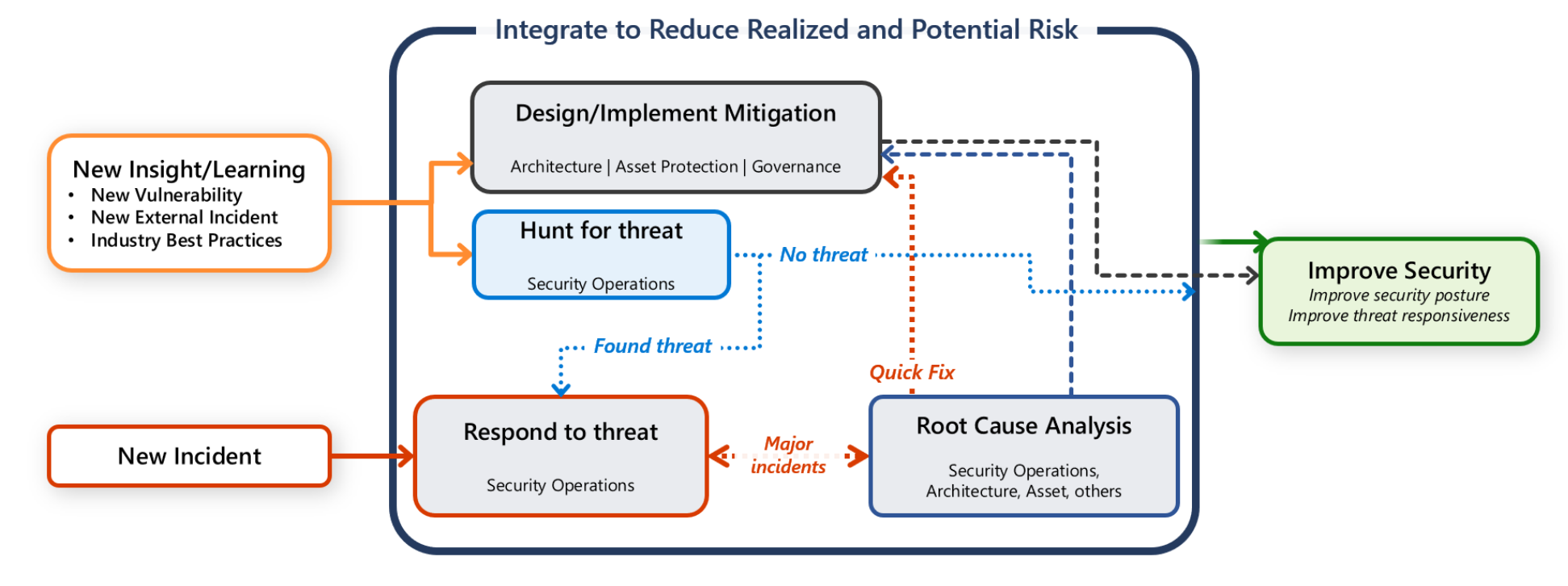
Recommendations for security incident response - Microsoft Azure
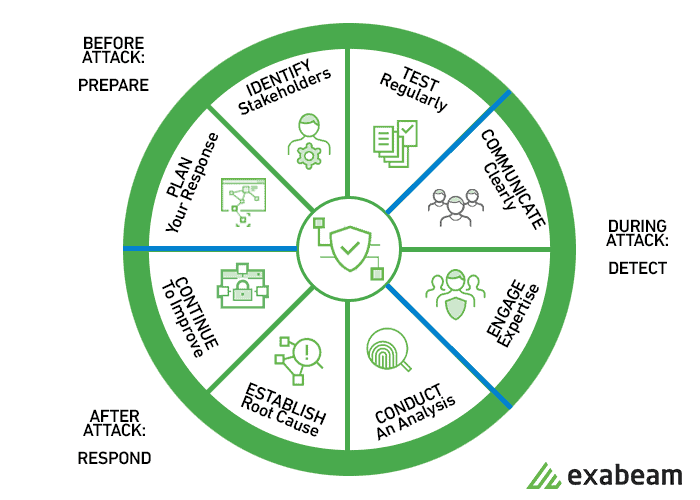
Incident Response Plan 101: How to Build On - Exabeam
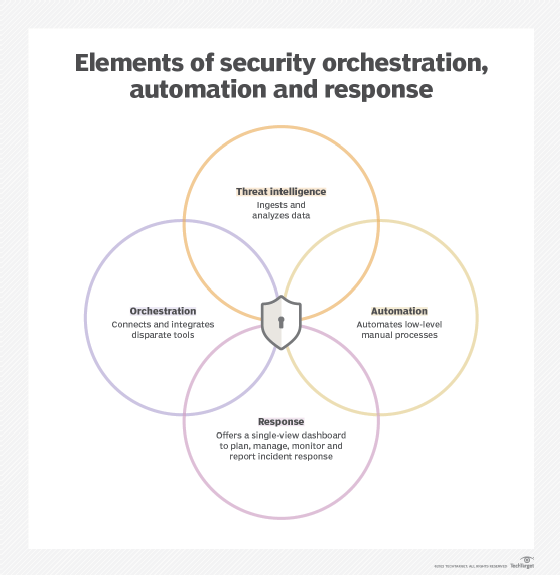
What is Incident Response? Plans, Teams and Tools

Cybersecurity Incident Response Exercise Guidance

What is Zero Trust Security? Principles of the Zero Trust Model
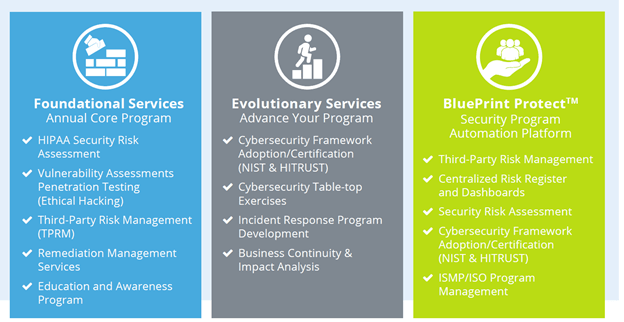
Healthcare Security Essentials Program for VC & PE Portfolio

What is SOAR (Security Orchestration, Automation, and Response

Information & Cyber Security Policy Templates
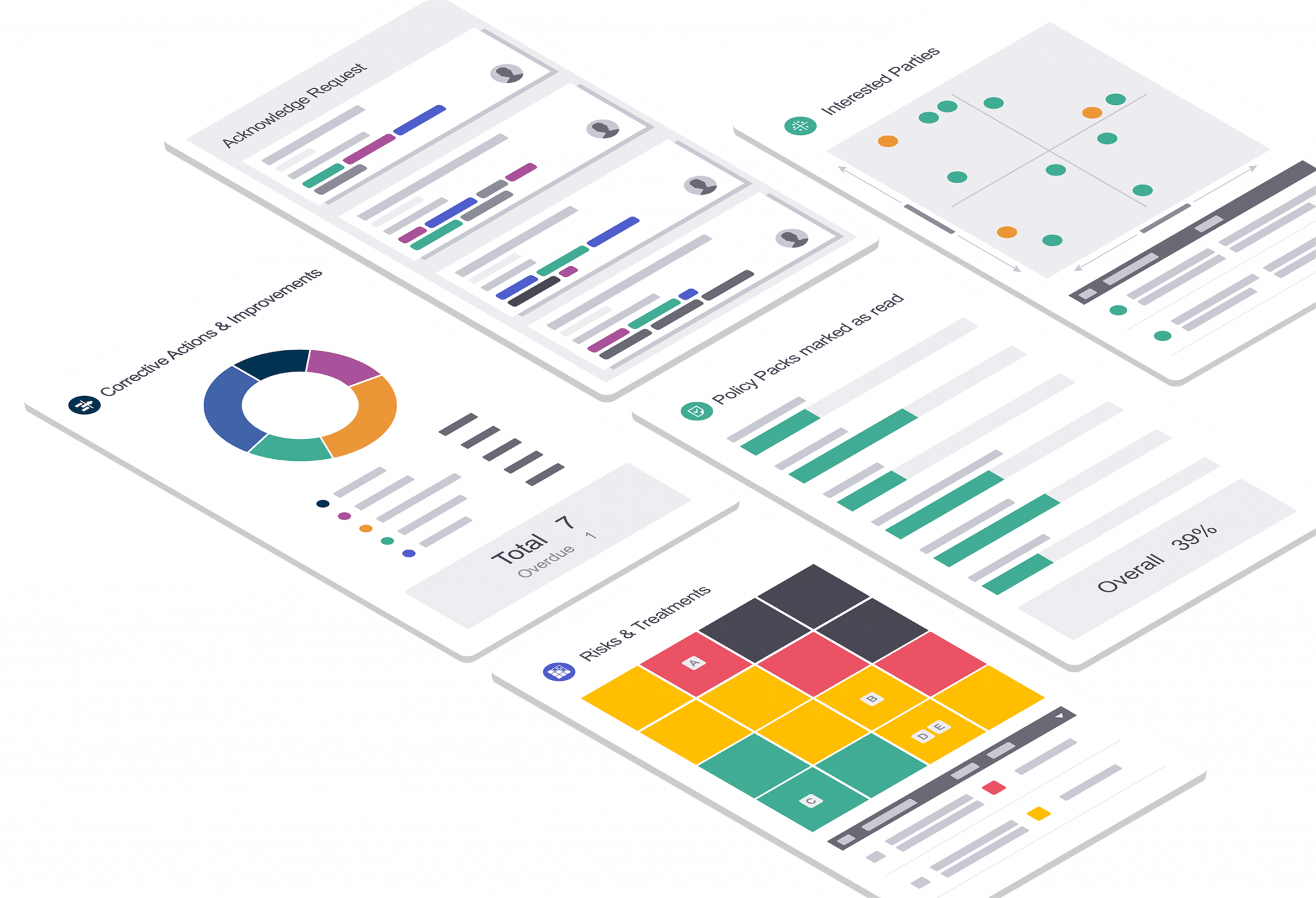
Information Security Management System (Pre-configured ISMS) Solution

MasterClass Incident Handler and Response Program

What is Incident Response? Plans, Teams and Tools

Top 5 Most Common Incident Response Scenarios
Cybersecurity vs. Information Security, Blog

How to Create a Cybersecurity Incident Response Plan - Hyperproof
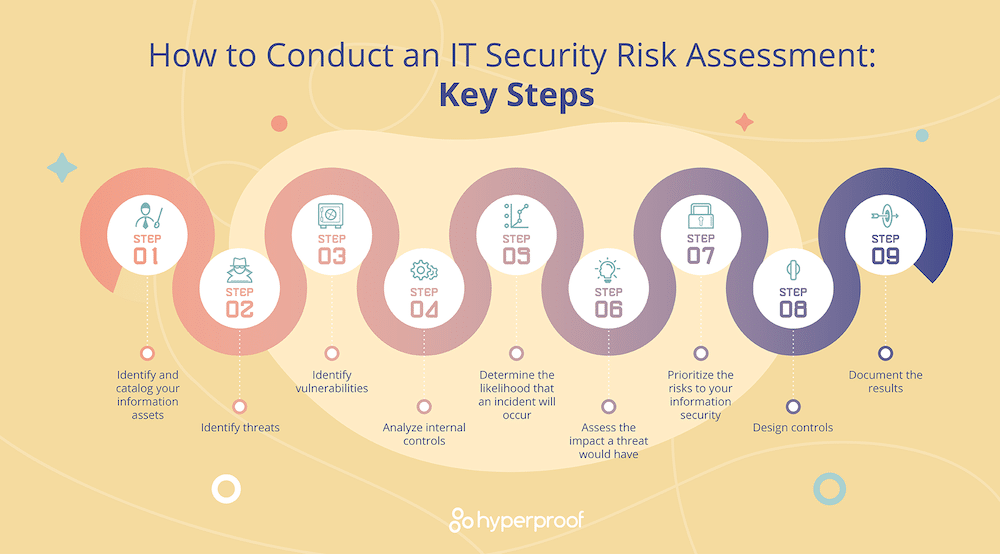
How to Perform a Successful IT Risk Assessment - Hyperproof
Recomendado para você
-
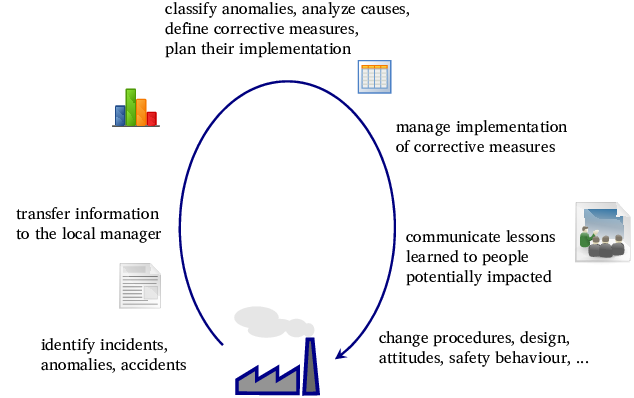 Learning from incidents and accidents: The gift of failure15 abril 2025
Learning from incidents and accidents: The gift of failure15 abril 2025 -
CalQRisk on LinkedIn: #incidentmanagement #freewebinar15 abril 2025
-
Why Lessons Learned Is The Most Critical Step In Incident Response15 abril 2025
-
![PDF] Guidance on Learning From Incidents, Accidents and Events](https://d3i71xaburhd42.cloudfront.net/598ee0ba63c9cf1cc1b27f26669d11052485384d/9-Table4-1.png) PDF] Guidance on Learning From Incidents, Accidents and Events15 abril 2025
PDF] Guidance on Learning From Incidents, Accidents and Events15 abril 2025 -
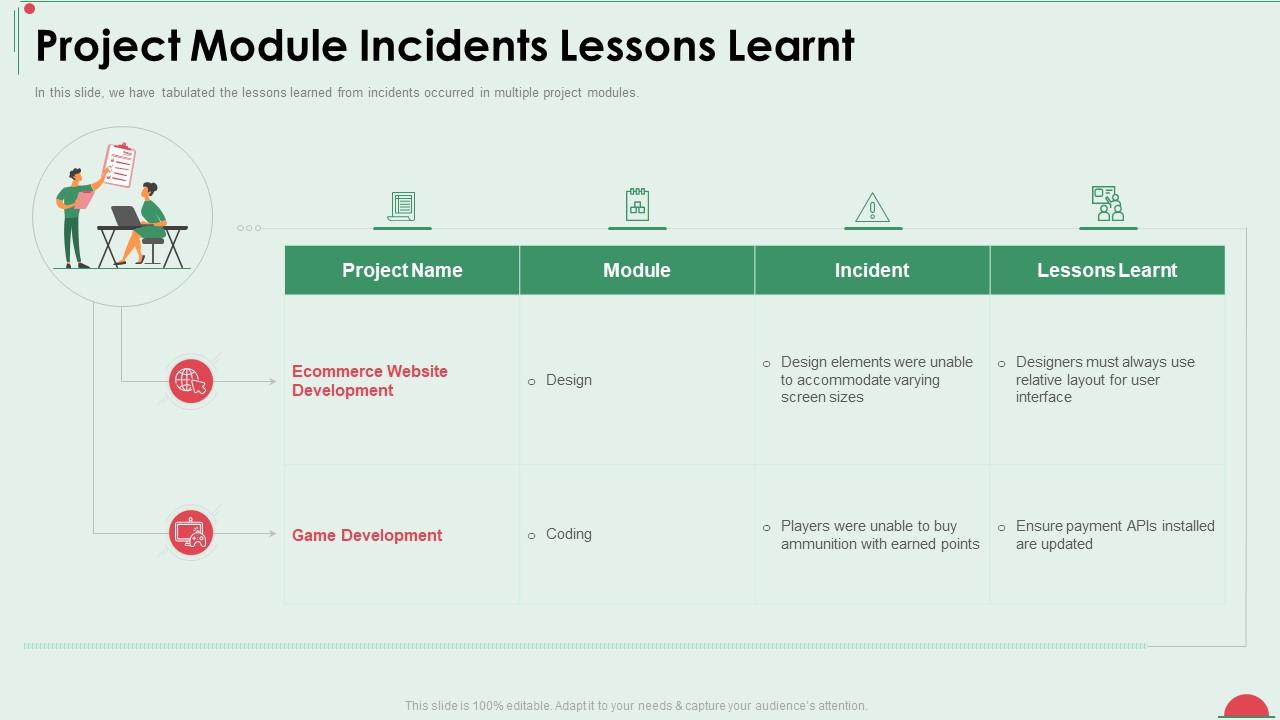 Project In Controlled Environment Project Module Incidents Lessons15 abril 2025
Project In Controlled Environment Project Module Incidents Lessons15 abril 2025 -
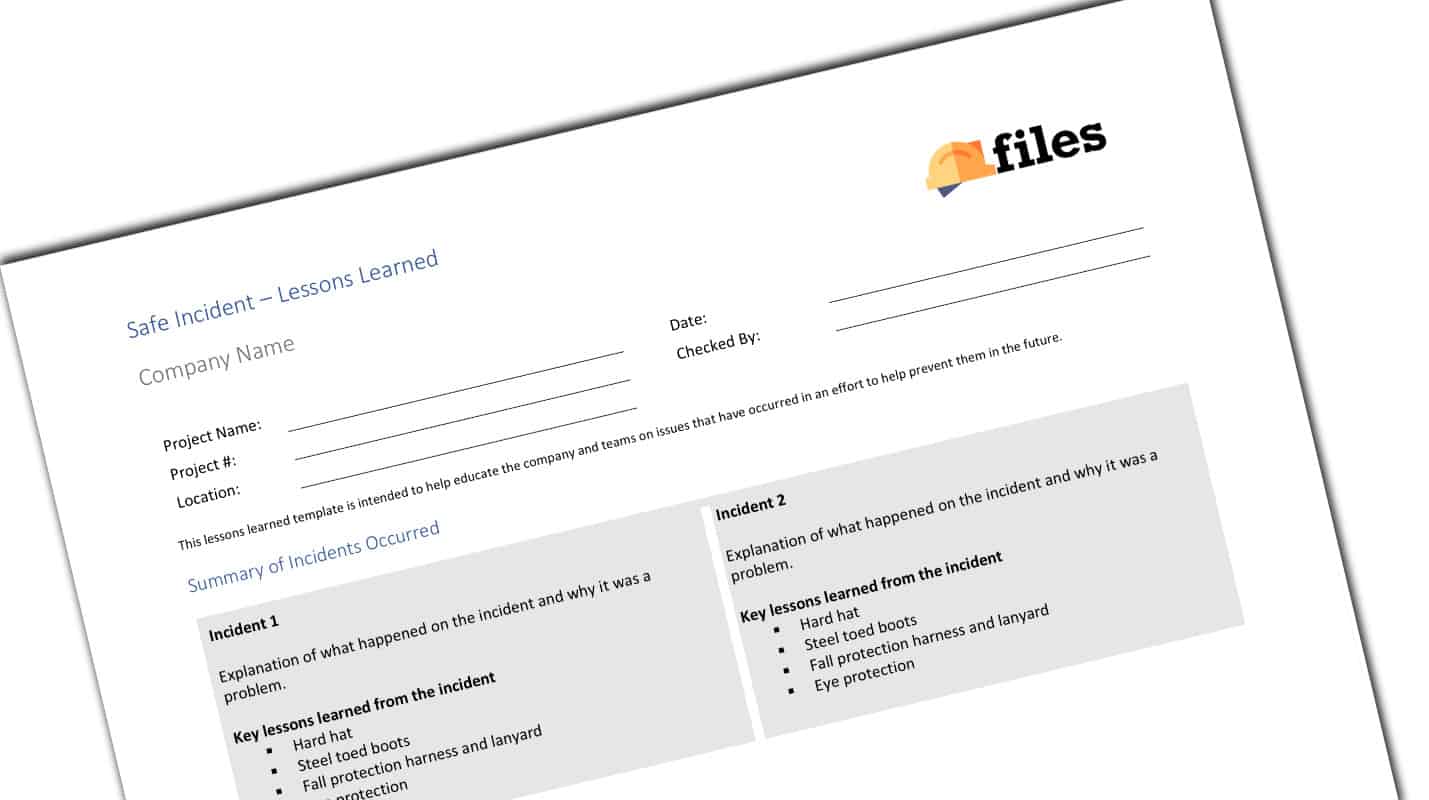 Safety Lessons Learned Template - Construction Documents And Templates15 abril 2025
Safety Lessons Learned Template - Construction Documents And Templates15 abril 2025 -
 The Importance of Accident Investigation and Learning from Incidents15 abril 2025
The Importance of Accident Investigation and Learning from Incidents15 abril 2025 -
Solved SCEN You have a dual role as an experienced and15 abril 2025
-
 Incident Report Definition, Types & Examples - Video & Lesson15 abril 2025
Incident Report Definition, Types & Examples - Video & Lesson15 abril 2025 -
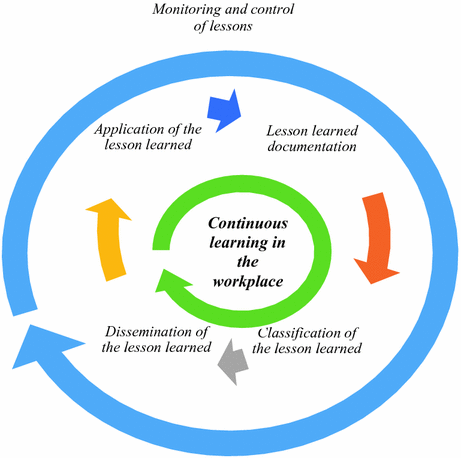 Lesson Learned Management Model for Solving Incidents in a Company15 abril 2025
Lesson Learned Management Model for Solving Incidents in a Company15 abril 2025
você pode gostar
-
 Hermannstadt: Kleine Geschichte einer Stadt in Siebenbürgen - Roth, Harald: 9783412051068 - AbeBooks15 abril 2025
Hermannstadt: Kleine Geschichte einer Stadt in Siebenbürgen - Roth, Harald: 9783412051068 - AbeBooks15 abril 2025 -
 The Owl House Luz Noceda #1 Jigsaw Puzzle15 abril 2025
The Owl House Luz Noceda #1 Jigsaw Puzzle15 abril 2025 -
 Disney characters as logo's Nfl funny, Nfl teams logos, Nfl15 abril 2025
Disney characters as logo's Nfl funny, Nfl teams logos, Nfl15 abril 2025 -
 Paulistão: Como funciona a distribuição de vagas na Copa do Brasil15 abril 2025
Paulistão: Como funciona a distribuição de vagas na Copa do Brasil15 abril 2025 -
 cr: @mbti.baby in 2023 Intj personality, Intj characters, Intj enfp15 abril 2025
cr: @mbti.baby in 2023 Intj personality, Intj characters, Intj enfp15 abril 2025 -
 Onde assistir: Manchester City x Chelsea ao vivo vai passar pela ESPN hoje? · Notícias da TV15 abril 2025
Onde assistir: Manchester City x Chelsea ao vivo vai passar pela ESPN hoje? · Notícias da TV15 abril 2025 -
 Por que antigamente a Internet não subia de elevador? - Charada e Resposta - Geniol15 abril 2025
Por que antigamente a Internet não subia de elevador? - Charada e Resposta - Geniol15 abril 2025 -
 Hitman 3 July 2022 roadmap brings new free Ambrose Island location15 abril 2025
Hitman 3 July 2022 roadmap brings new free Ambrose Island location15 abril 2025 -
 Entei Raikou Suicune Glas in Lood / Aangepaste Holografische15 abril 2025
Entei Raikou Suicune Glas in Lood / Aangepaste Holografische15 abril 2025 -
 Dica: Quatro filmes anime para você assistir na Netflix e se15 abril 2025
Dica: Quatro filmes anime para você assistir na Netflix e se15 abril 2025


