Pawn Storm Abuses OAuth In Social Engineering Attacks
Por um escritor misterioso
Last updated 15 abril 2025
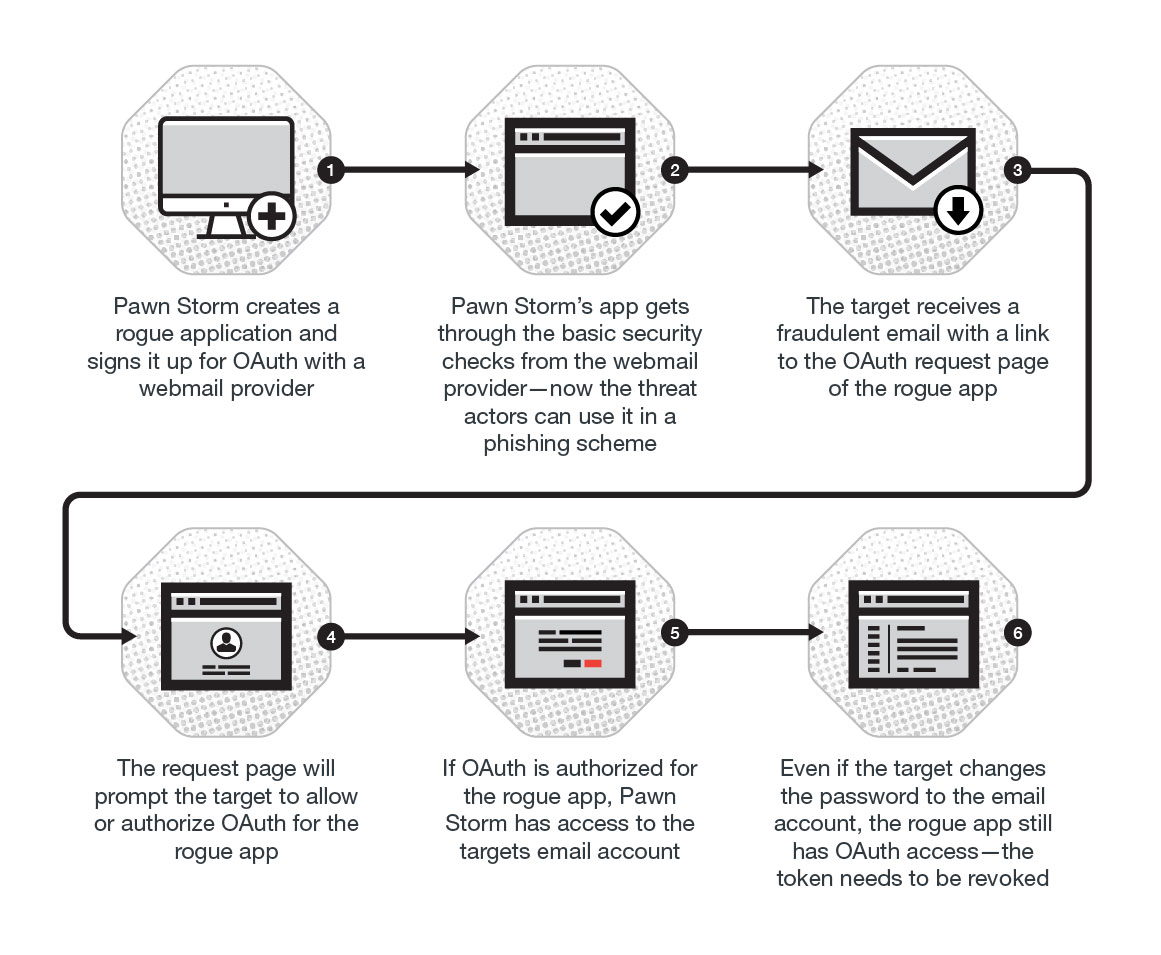
This blog post discusses how Pawn Storm abused Open Authentication (OAuth) in advanced social engineering schemes. High profile users of free webmail were targeted by campaigns between 2015 and 2016.

APT28 relies on PowerPoint Mouseover to deliver Graphite malware

The 13 Most Common Types of Social Engineering Attacks + How to Defend Against Them

OAuth, Breaking Cybersecurity News

Pawn Storm behind cyber-attacks on organisations conducting Winter Olympics

TrustedSec Practical OAuth Abuse for Offensive Operations – Part 1
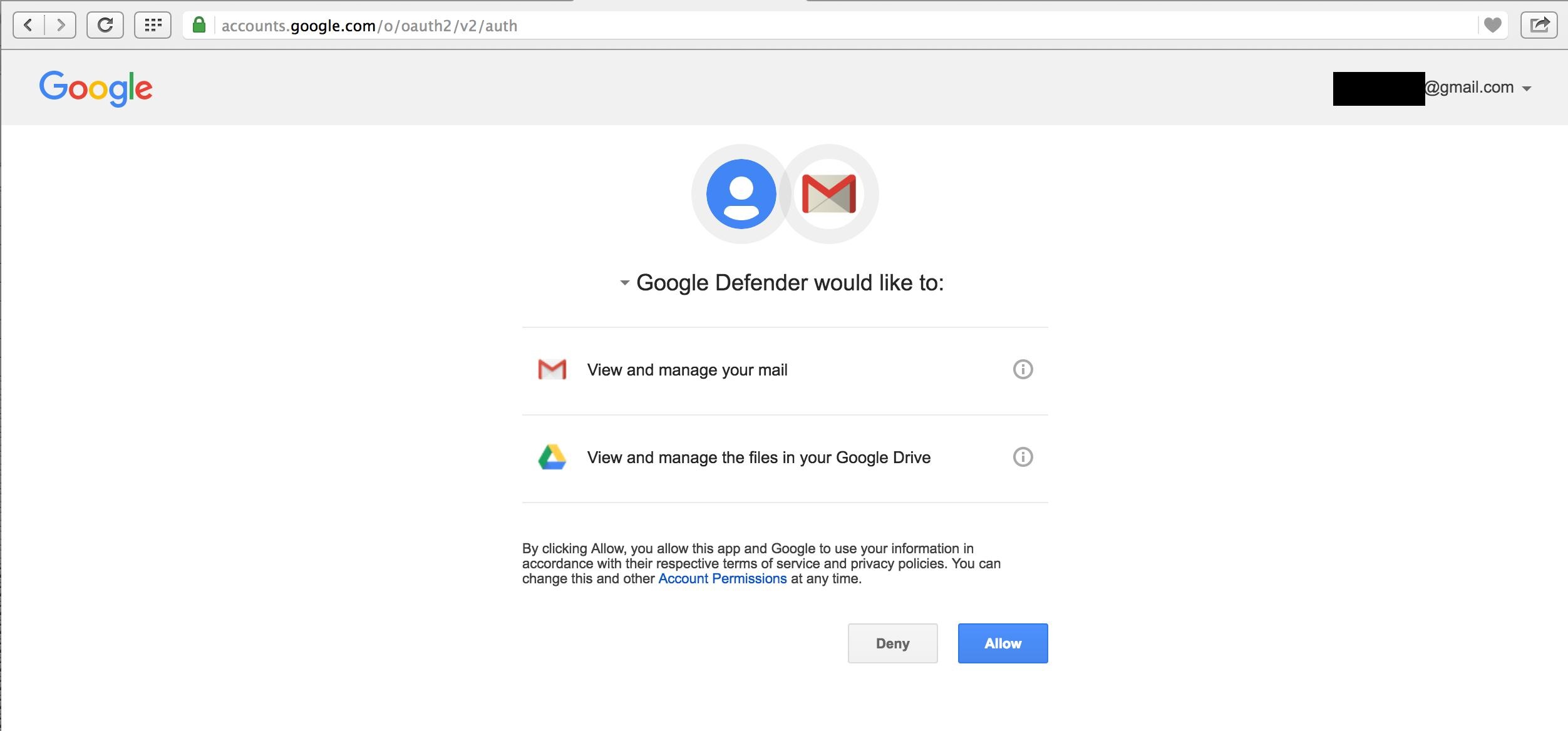
Pawn Storm Abuses OAuth In Social Engineering Attacks
What are Social Engineering Attacks? Types of Attacks in 2023
GitHub - netskopeoss/phish_oauth: POC code to explore phishing attacks using OAuth 2.0 authorization flows, such as the device authorization grant.

OAuth, Breaking Cybersecurity News

Salt Labs Oh-Auth - Abusing OAuth to take over millions of accounts
Pawn Storm's Lack of Sophistication as a Strategy
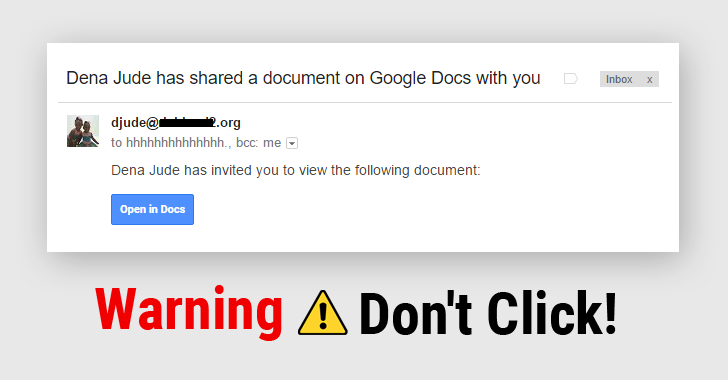
OAuth, Breaking Cybersecurity News
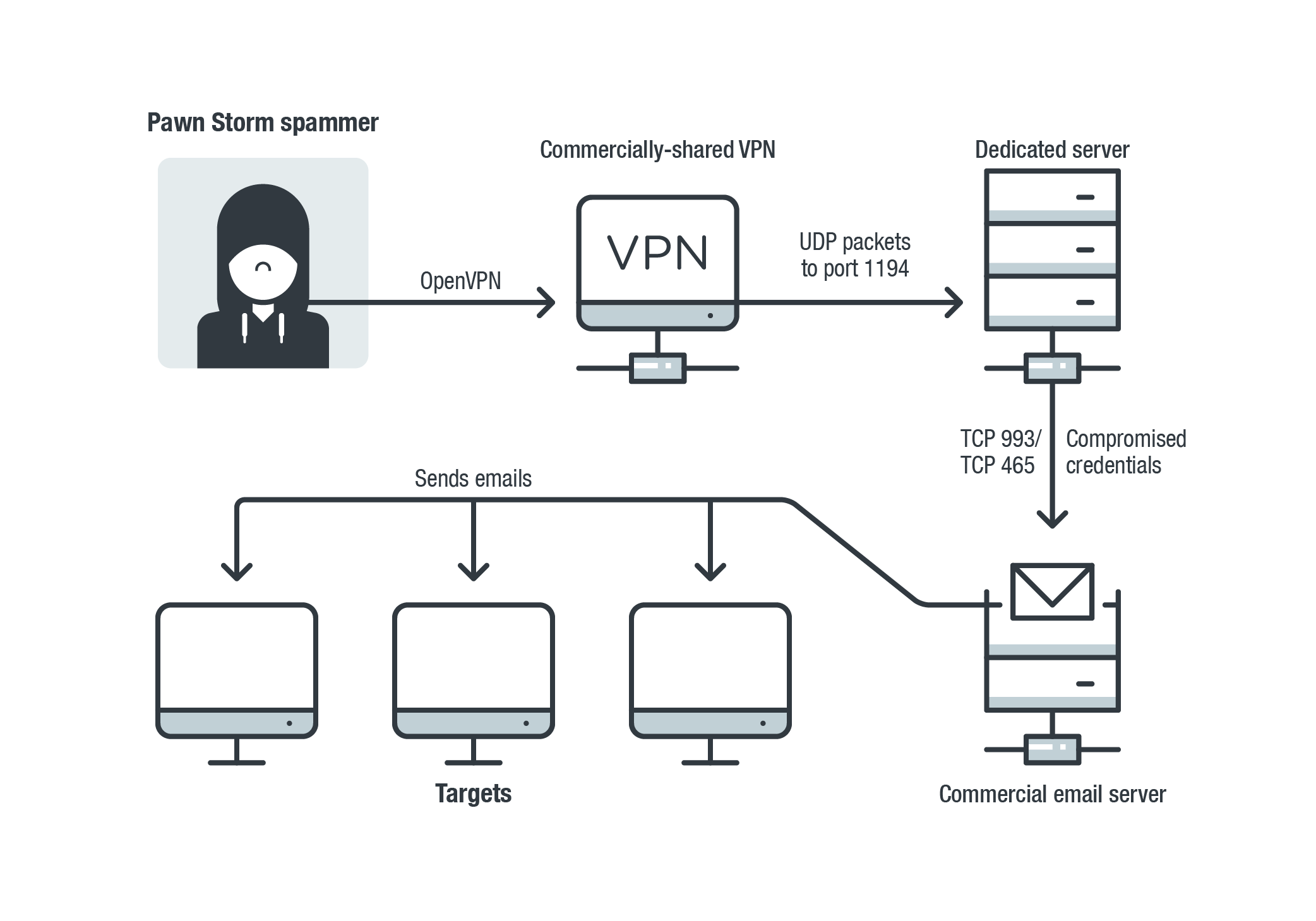
Probing Pawn Storm: Cyberespionage Campaign Through Scanning, Credential Phishing and More - Security News
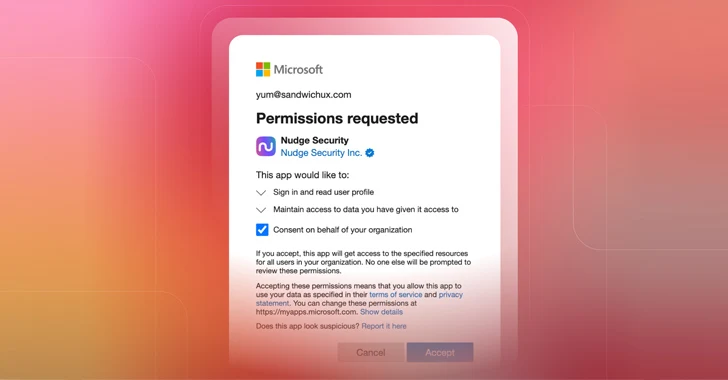
OAuth, Breaking Cybersecurity News

What Are Social Engineering Attacks and How to Prevent Them - SEON
Recomendado para você
-
Pawns.app: Paid Surveys - Apps on Google Play15 abril 2025
-
 IPRoyal Pawns Just Became - Pawns15 abril 2025
IPRoyal Pawns Just Became - Pawns15 abril 2025 -
 FoxSell Slider & Carousel - FoxSell - Product Carousel & Product Slider for Shopify15 abril 2025
FoxSell Slider & Carousel - FoxSell - Product Carousel & Product Slider for Shopify15 abril 2025 -
 MobilePawn – Pay and Extend Online15 abril 2025
MobilePawn – Pay and Extend Online15 abril 2025 -
ATF Houston Field Division is offering a $5,000 reward for information leading to the arrest and conviction of the persons responsible for…15 abril 2025
-
 Maurice Ashley on X: Visualization training: How can the queen capture all 11 pawns in exactly 11 moves? The pawns do not move or protect each other. (From my app Maurice Ashley15 abril 2025
Maurice Ashley on X: Visualization training: How can the queen capture all 11 pawns in exactly 11 moves? The pawns do not move or protect each other. (From my app Maurice Ashley15 abril 2025 -
Pawns.app15 abril 2025
-
 Pawn Shop Map Announces App To Connect Pawn Shops With Customers Nearby15 abril 2025
Pawn Shop Map Announces App To Connect Pawn Shops With Customers Nearby15 abril 2025 -
 Meriden Pawn Now Available on Mobile Pawn App15 abril 2025
Meriden Pawn Now Available on Mobile Pawn App15 abril 2025 -
Is pawns.app best way to make passive income? - Quora15 abril 2025
você pode gostar
-
 Smartphone Samsung Galaxy A03 Core SM-A032M 32GB 8.0 MP em15 abril 2025
Smartphone Samsung Galaxy A03 Core SM-A032M 32GB 8.0 MP em15 abril 2025 -
 Everywhere You Look15 abril 2025
Everywhere You Look15 abril 2025 -
BoyWithUke - Toxic (Easy Version) Sheets by C Piano15 abril 2025
-
 Untitled Goose Game security hole could have allowed hackers to15 abril 2025
Untitled Goose Game security hole could have allowed hackers to15 abril 2025 -
 Quote The Anime on X: One Piece Episode 1017 is now trending on Twitter, unleashing the best animation to date. Henry Thurlow (The Last: Naruto Movie, Tokyo Ghoul) storyboarded 25% of the15 abril 2025
Quote The Anime on X: One Piece Episode 1017 is now trending on Twitter, unleashing the best animation to date. Henry Thurlow (The Last: Naruto Movie, Tokyo Ghoul) storyboarded 25% of the15 abril 2025 -
 San Andreas Cheats APK للاندرويد تنزيل15 abril 2025
San Andreas Cheats APK للاندرويد تنزيل15 abril 2025 -
 Hi Top Lona Camurça Preto/ Amarelo15 abril 2025
Hi Top Lona Camurça Preto/ Amarelo15 abril 2025 -
Arena Football League announces 16-team return in 202415 abril 2025
-
 Jogo Super Mario 3d World Bowsers Fury Nintendo Switch em Promoção15 abril 2025
Jogo Super Mario 3d World Bowsers Fury Nintendo Switch em Promoção15 abril 2025 -
Grand Theft Auto IV Complete - Xbox 360, Xbox 36015 abril 2025


