R. on X: Again #RIFT #IoT #Botnet #Mirai #ELF #malware #Trojan.Linux #Backdoor Exploit Target : #GPON #HUAWEI #REALTEK #Linksys #DLINK 𝗜𝗣: 176.223.135(.)216 Payload 𝗟𝗜𝗡𝗞: 176.223.135.216/bins/rift.* Country: Poland Currently 𝗔𝗰𝘁𝗶𝘃𝗲 CC: @_
Por um escritor misterioso
Last updated 16 abril 2025
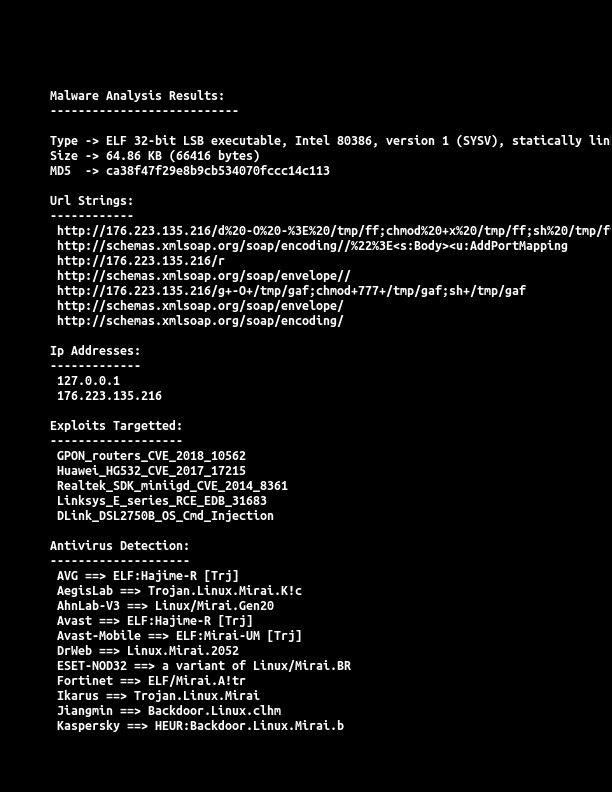

R. on X: Again #RIFT #IoT #Botnet #Mirai #ELF #malware #Trojan.Linux #Backdoor Exploit Target : #GPON #HUAWEI #REALTEK #Linksys #DLINK 𝗜𝗣: 176.223.135(.)216 Payload 𝗟𝗜𝗡𝗞: 176.223.135.216/bins/rift.* Country: Poland Currently 𝗔𝗰𝘁𝗶𝘃𝗲 CC: @_
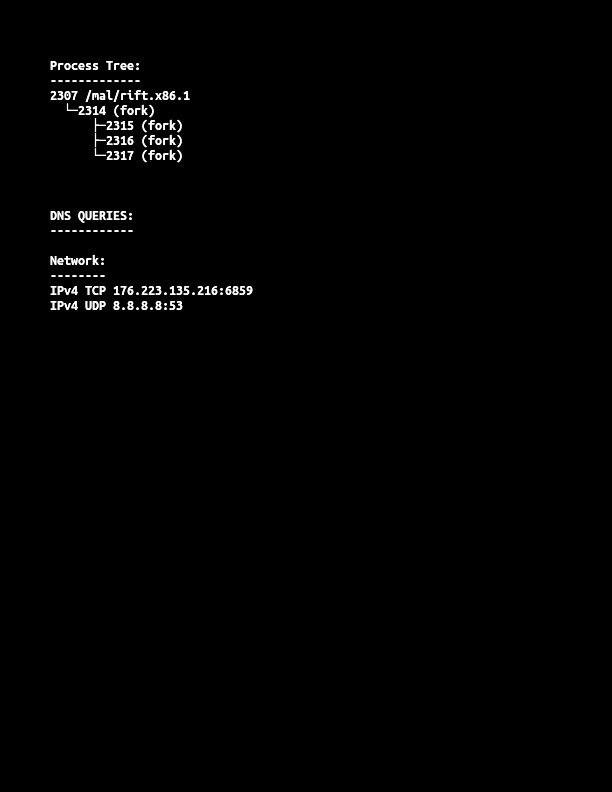
R. on X: Again #RIFT #IoT #Botnet #Mirai #ELF #malware #Trojan.Linux #Backdoor Exploit Target : #GPON #HUAWEI #REALTEK #Linksys #DLINK 𝗜𝗣: 176.223.135(.)216 Payload 𝗟𝗜𝗡𝗞: 176.223.135.216/bins/rift.* Country: Poland Currently 𝗔𝗰𝘁𝗶𝘃𝗲 CC: @_
Recomendado para você
-
 malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange16 abril 2025
malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange16 abril 2025 -
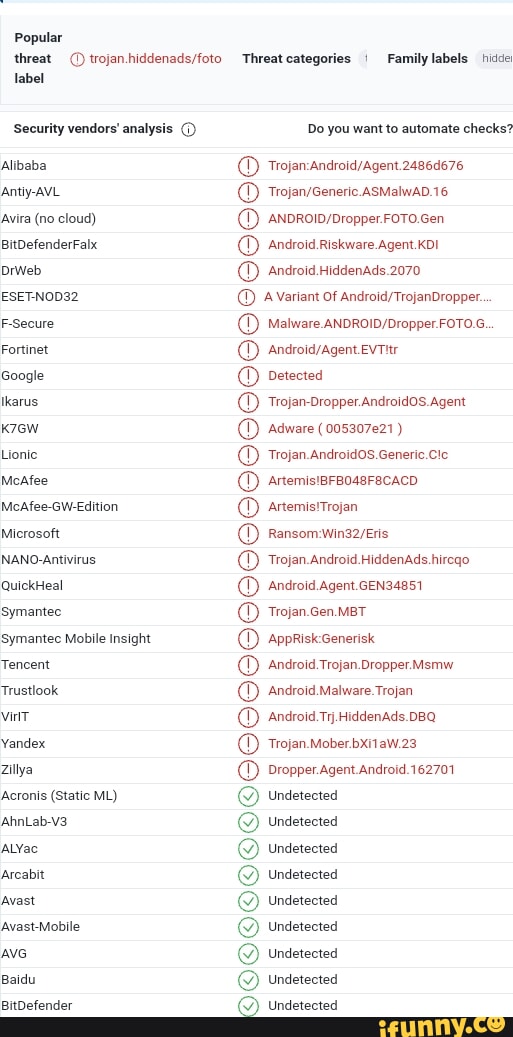 Ikarus memes. Best Collection of funny Ikarus pictures on iFunny Brazil16 abril 2025
Ikarus memes. Best Collection of funny Ikarus pictures on iFunny Brazil16 abril 2025 -
 How To Remove Trojan Vundo (Trojan:Win32/Vundo And TR/Drop.Vundo)16 abril 2025
How To Remove Trojan Vundo (Trojan:Win32/Vundo And TR/Drop.Vundo)16 abril 2025 -
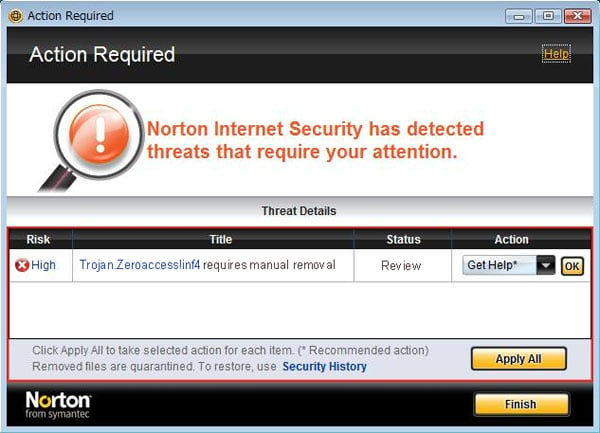 How To Easily Remove ZeroAccess Trojan (Virus Removal Guide)16 abril 2025
How To Easily Remove ZeroAccess Trojan (Virus Removal Guide)16 abril 2025 -
 Analysis results for wget.exe on two different dates.16 abril 2025
Analysis results for wget.exe on two different dates.16 abril 2025 -
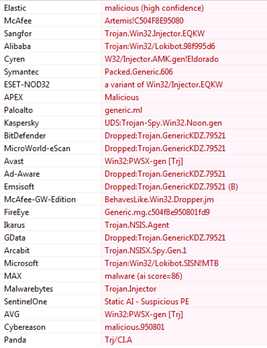 FormBook Malware Technical Analysis - CYFIRMA16 abril 2025
FormBook Malware Technical Analysis - CYFIRMA16 abril 2025 -
 Trojan Horse (Windows): HackIt16 abril 2025
Trojan Horse (Windows): HackIt16 abril 2025 -
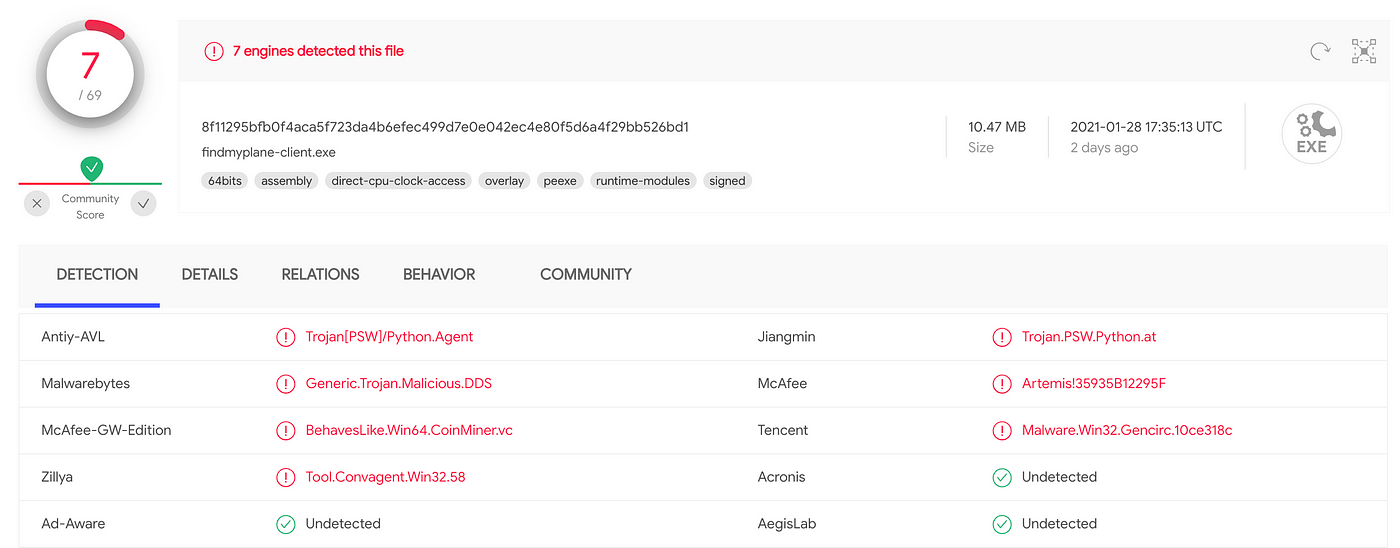 How to stop your Python programs being seen as malware, by Mark Hank16 abril 2025
How to stop your Python programs being seen as malware, by Mark Hank16 abril 2025 -
 The contents of the compressed file in B6500360.exe. Analysis 2016 abril 2025
The contents of the compressed file in B6500360.exe. Analysis 2016 abril 2025 -
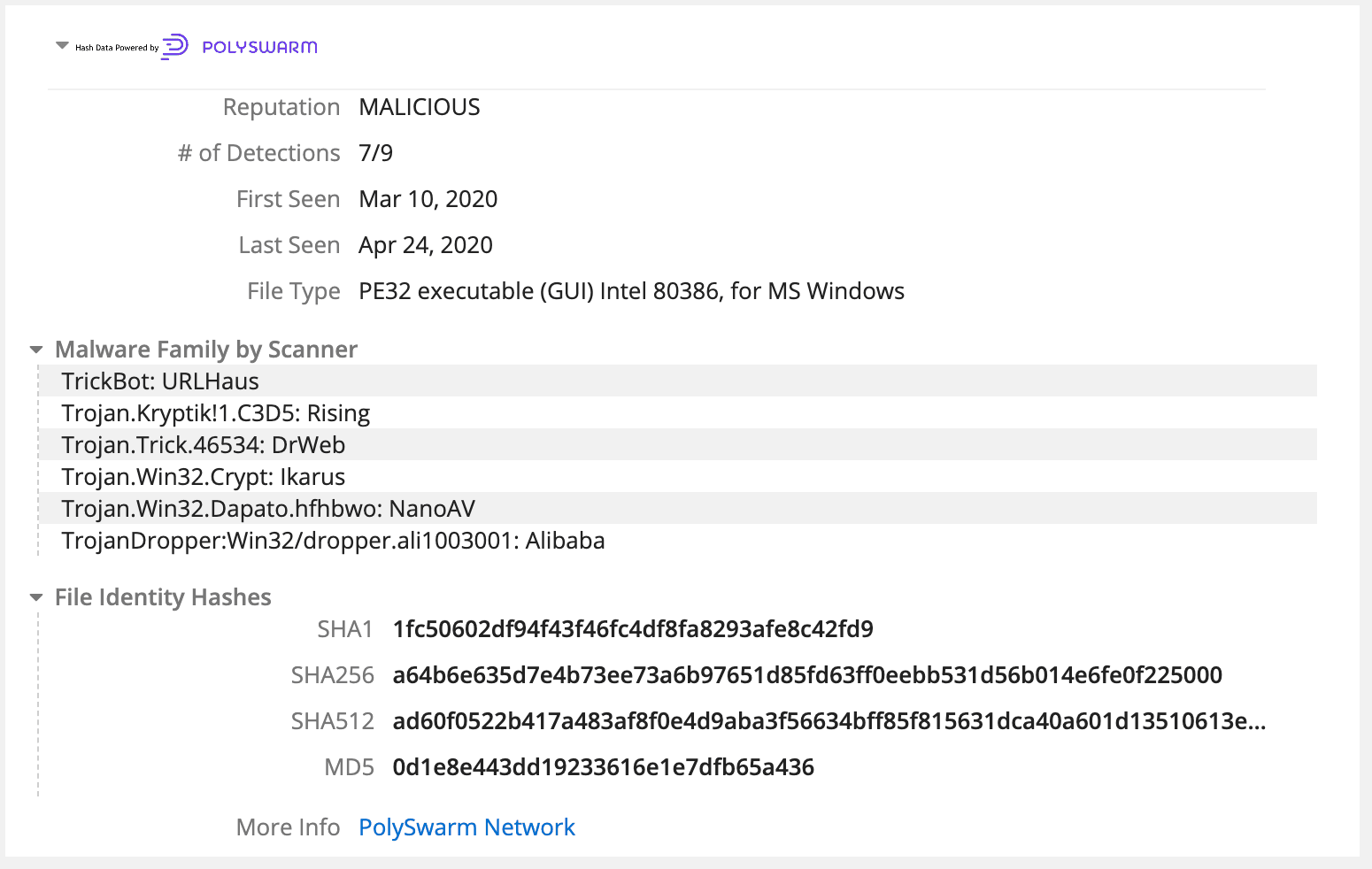 Polyswarm16 abril 2025
Polyswarm16 abril 2025
você pode gostar
-
 4+ Free The Scarlet Eggplant & Scarlet Eggplant Images - Pixabay16 abril 2025
4+ Free The Scarlet Eggplant & Scarlet Eggplant Images - Pixabay16 abril 2025 -
 Mahjong Spelen16 abril 2025
Mahjong Spelen16 abril 2025 -
 Anime Vietsub Online - Xem Phim Anime mới nhất16 abril 2025
Anime Vietsub Online - Xem Phim Anime mới nhất16 abril 2025 -
![ROBLOX LITE✓]NOVA ATUALIZAÇÃO DO ROBLOX LITE PARA ANDROID📲tire seu lag agora!!](https://i.ytimg.com/vi/8RSd-ZE4ANs/maxresdefault.jpg) ROBLOX LITE✓]NOVA ATUALIZAÇÃO DO ROBLOX LITE PARA ANDROID📲tire seu lag agora!!16 abril 2025
ROBLOX LITE✓]NOVA ATUALIZAÇÃO DO ROBLOX LITE PARA ANDROID📲tire seu lag agora!!16 abril 2025 -
 Foxzie on X: 🔥 SEASON 5 IS OUT! 🔥 🏆 New Season! 7 prizes! 🚗 1 limited car! 🏁 New Season race! 💰 Use code Season5 for $75,000 in-game money! / X16 abril 2025
Foxzie on X: 🔥 SEASON 5 IS OUT! 🔥 🏆 New Season! 7 prizes! 🚗 1 limited car! 🏁 New Season race! 💰 Use code Season5 for $75,000 in-game money! / X16 abril 2025 -
 Malware analysis Malicious activity16 abril 2025
Malware analysis Malicious activity16 abril 2025 -
 Read Peter Grill To Kenja No Jikan Chapter 13: Peter Grill And The Mega-Ton Ace Of Wrath - Manganelo16 abril 2025
Read Peter Grill To Kenja No Jikan Chapter 13: Peter Grill And The Mega-Ton Ace Of Wrath - Manganelo16 abril 2025 -
 Editable blanket drive flyer Editable blanket in need - Portugal16 abril 2025
Editable blanket drive flyer Editable blanket in need - Portugal16 abril 2025 -
 Digimon Adventure Tri.: Loss Combo16 abril 2025
Digimon Adventure Tri.: Loss Combo16 abril 2025 -
 Yu-Gi-Oh! 5D's - Episode 123 - Yugipedia - Yu-Gi-Oh! wiki16 abril 2025
Yu-Gi-Oh! 5D's - Episode 123 - Yugipedia - Yu-Gi-Oh! wiki16 abril 2025