Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 16 abril 2025

Confusion Matrix: How To Use It & Interpret Results [Examples]

Clean Water through Nanotechnology: Needs, Gaps, and Fulfillment

100+ AI Use Cases & Applications: In-Depth Guide for 2023
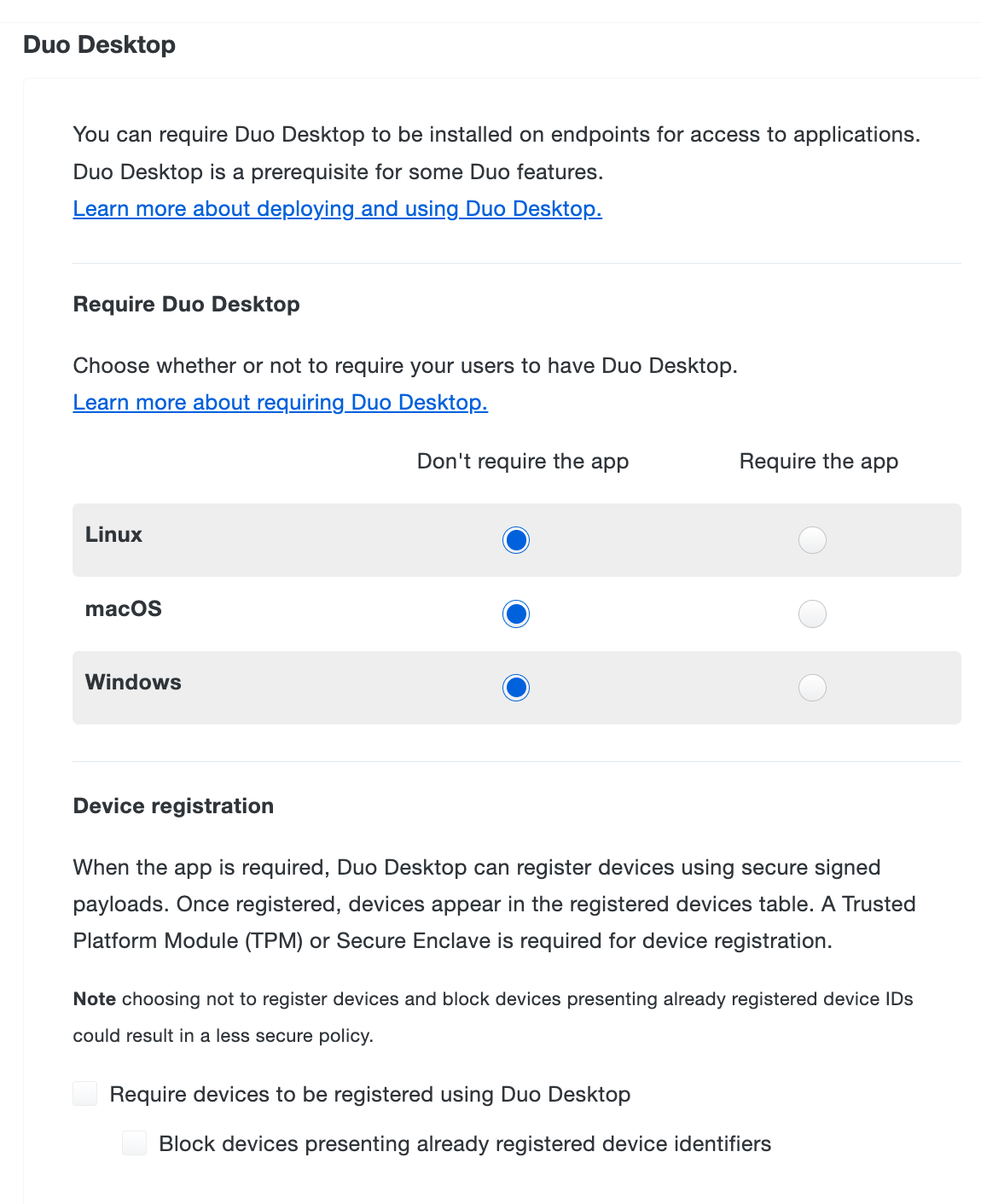
Duo Administration - Policy & Control
Triggering events in Cloud One - Workload Security
Cloaked Ursa (APT29) Hackers Use Trusted Online Storage Services

Climate change - Wikipedia
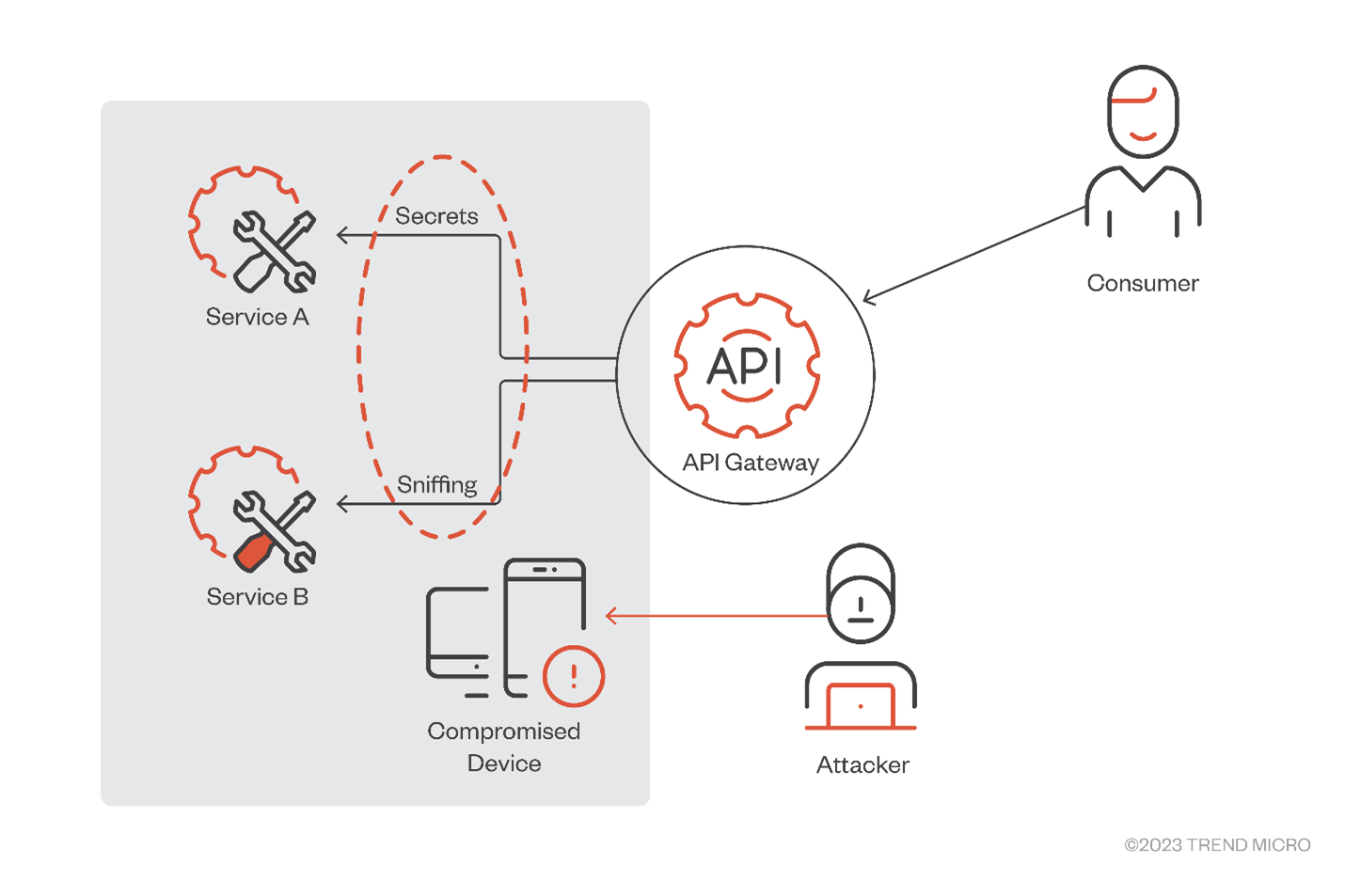
Threat Modeling API Gateways: A New Target for Threat Actors? - Noticias de seguridad - Trend Micro ES
Viewing encrypted mails
How to report misrated websites to Trend Micro
Trend Micro Update Toolset - Endpoint Application Control 2.0
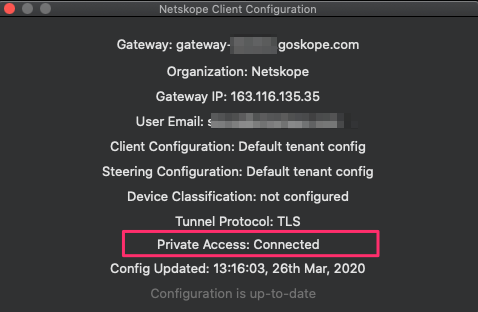
General Troubleshooting Methods - Netskope Knowledge Portal
Recomendado para você
-
 Warning: FaceStealer iOS and Android apps steal your Facebook login16 abril 2025
Warning: FaceStealer iOS and Android apps steal your Facebook login16 abril 2025 -
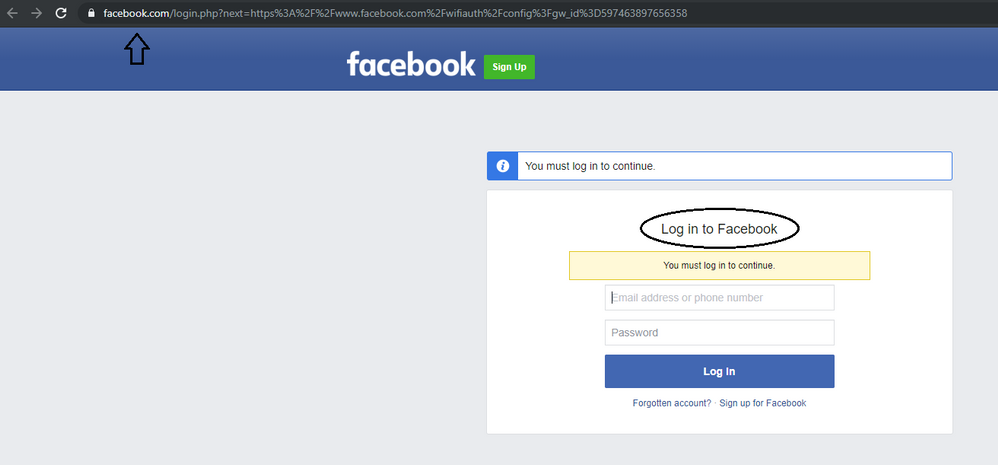
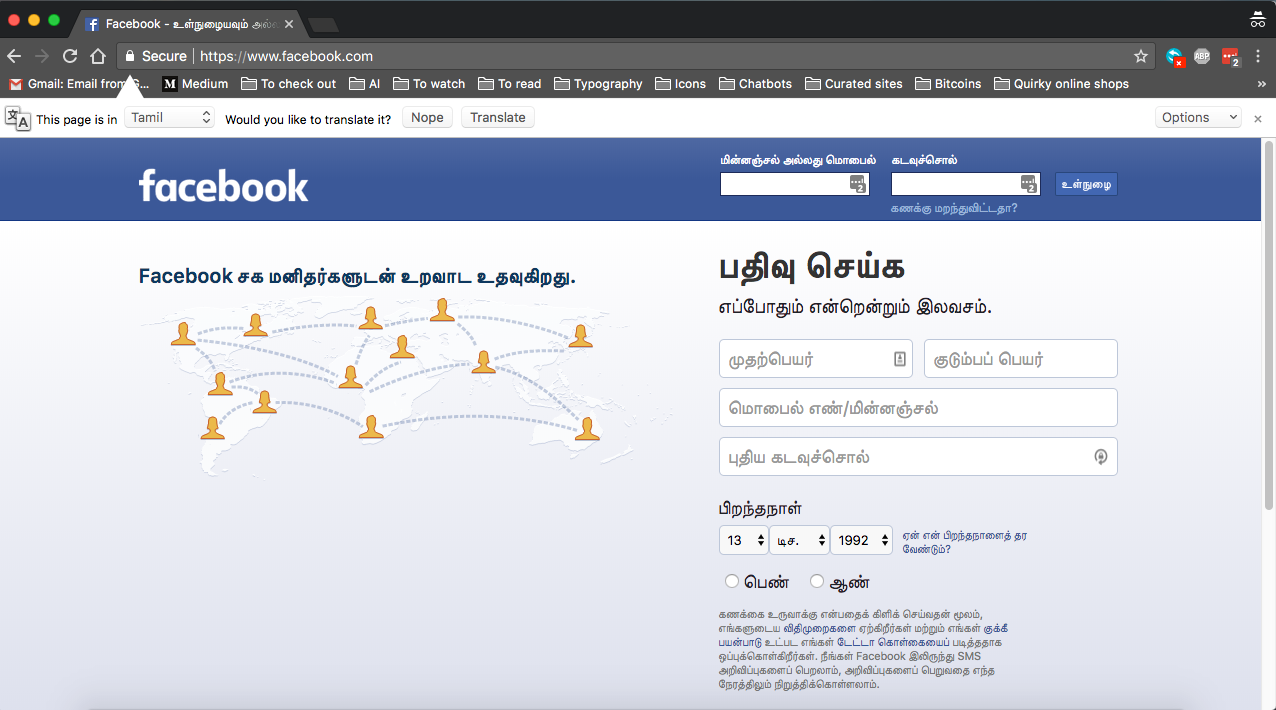 What to do when Facebook's homepage looks like gibberish?16 abril 2025
What to do when Facebook's homepage looks like gibberish?16 abril 2025 -
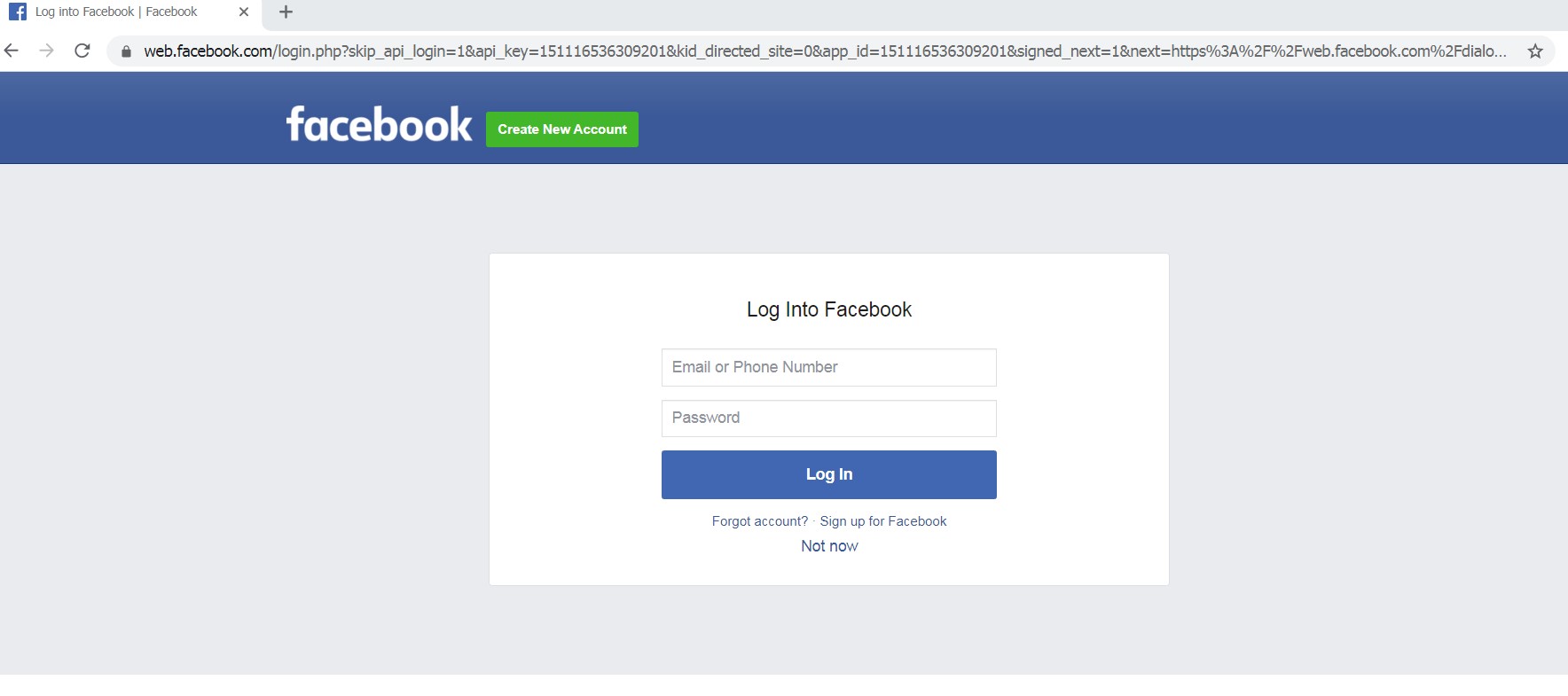
 Facebook login page redesign on Behance16 abril 2025
Facebook login page redesign on Behance16 abril 2025 -
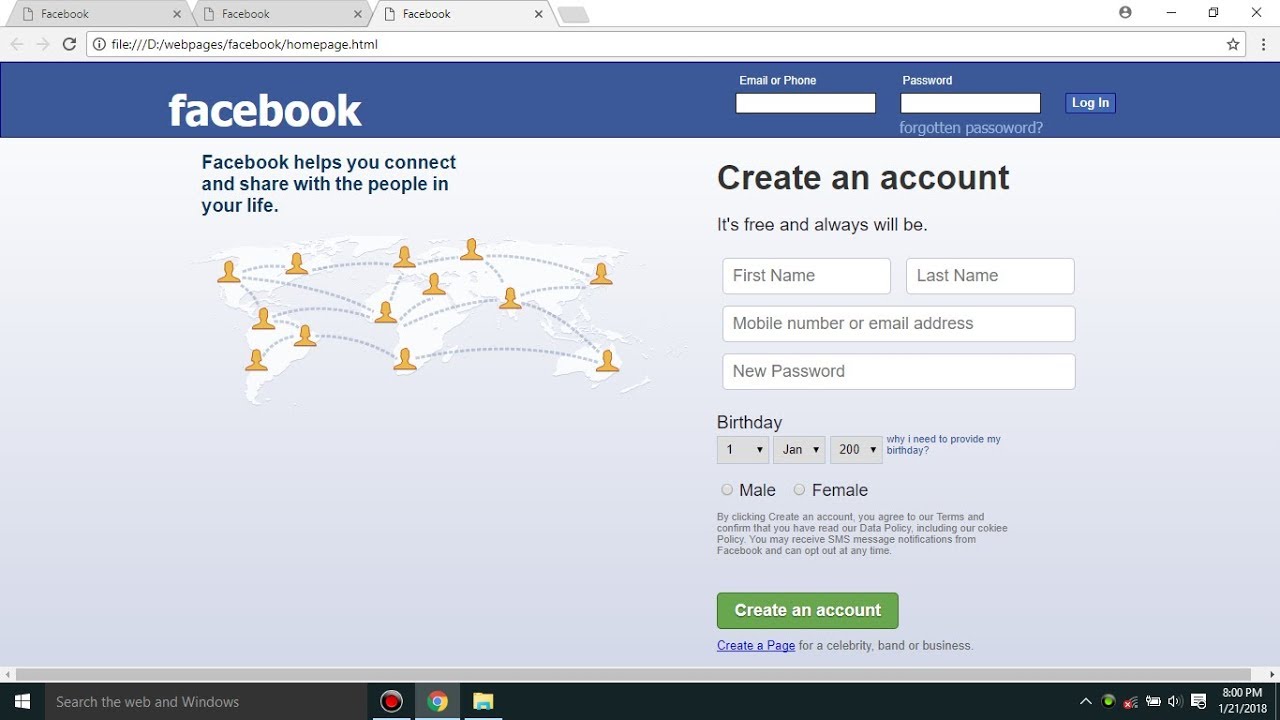 Facebook Login page Design, HTML, CSS16 abril 2025
Facebook Login page Design, HTML, CSS16 abril 2025 -
 Inspiration Login Screen on Android by Facebook - UI Garage16 abril 2025
Inspiration Login Screen on Android by Facebook - UI Garage16 abril 2025 -
 Facebook Login Page Stock Photos - 863 Images16 abril 2025
Facebook Login Page Stock Photos - 863 Images16 abril 2025 -
 Facebook opens Ads Page instead of regular homepage after login16 abril 2025
Facebook opens Ads Page instead of regular homepage after login16 abril 2025 -
 Configure Facebook login for Discourse - admins - Discourse Meta16 abril 2025
Configure Facebook login for Discourse - admins - Discourse Meta16 abril 2025 -
How to configure Facebook login page for Guest users16 abril 2025
-
 Ionic Facebook Login16 abril 2025
Ionic Facebook Login16 abril 2025
você pode gostar
-
 The Watcher Season 2 Can Fix Season 1's Hated Ending Problem - IMDb16 abril 2025
The Watcher Season 2 Can Fix Season 1's Hated Ending Problem - IMDb16 abril 2025 -
La Casa Di Pizza delivery16 abril 2025
-
 UNCHARTED 2: Among Thieves™ Ps3 Psn Mídia Digital - kalangoboygames16 abril 2025
UNCHARTED 2: Among Thieves™ Ps3 Psn Mídia Digital - kalangoboygames16 abril 2025 -
 Dia Richesse # 5.31 - Praline Chestnut by L'Oreal Professional for16 abril 2025
Dia Richesse # 5.31 - Praline Chestnut by L'Oreal Professional for16 abril 2025 -
 Finally released my design of Skin-Stealer remixable, a Backrooms16 abril 2025
Finally released my design of Skin-Stealer remixable, a Backrooms16 abril 2025 -
 Carolina Herrera Blush Fragrance and Karlie Kloss on Femininity — Anne of Carversville16 abril 2025
Carolina Herrera Blush Fragrance and Karlie Kloss on Femininity — Anne of Carversville16 abril 2025 -
 Carro E Moto Png 5 Image - Carro E Moto Png,Moto Moto Png - free16 abril 2025
Carro E Moto Png 5 Image - Carro E Moto Png,Moto Moto Png - free16 abril 2025 -
 Roblox DOORS - Old Version of Seek Monster | Art Board Print16 abril 2025
Roblox DOORS - Old Version of Seek Monster | Art Board Print16 abril 2025 -
 Rave Madness Combat GIF - Rave Madness Combat Grunt - Discover & Share GIFs16 abril 2025
Rave Madness Combat GIF - Rave Madness Combat Grunt - Discover & Share GIFs16 abril 2025 -
 Naruto': Netflix responde fãs sobre a ausência da dublagem em16 abril 2025
Naruto': Netflix responde fãs sobre a ausência da dublagem em16 abril 2025