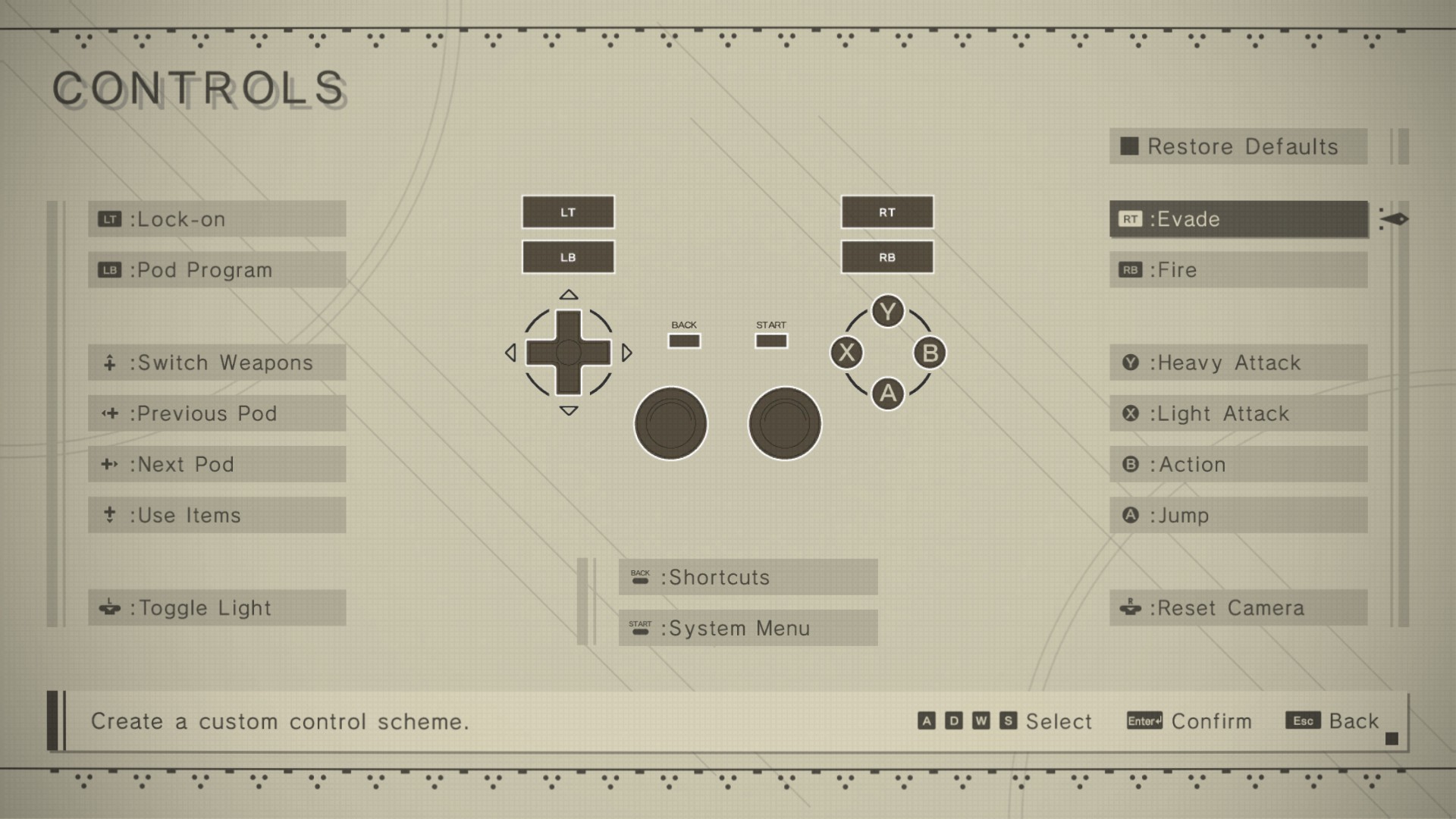
Suspicious User Controls
Por um escritor misterioso
Last updated 15 abril 2025


Stronger Access Control Management - Enterprise Network Security Blog from IS Decisions
Tip 5: Search for related party transactions – MindBridge: English (US)
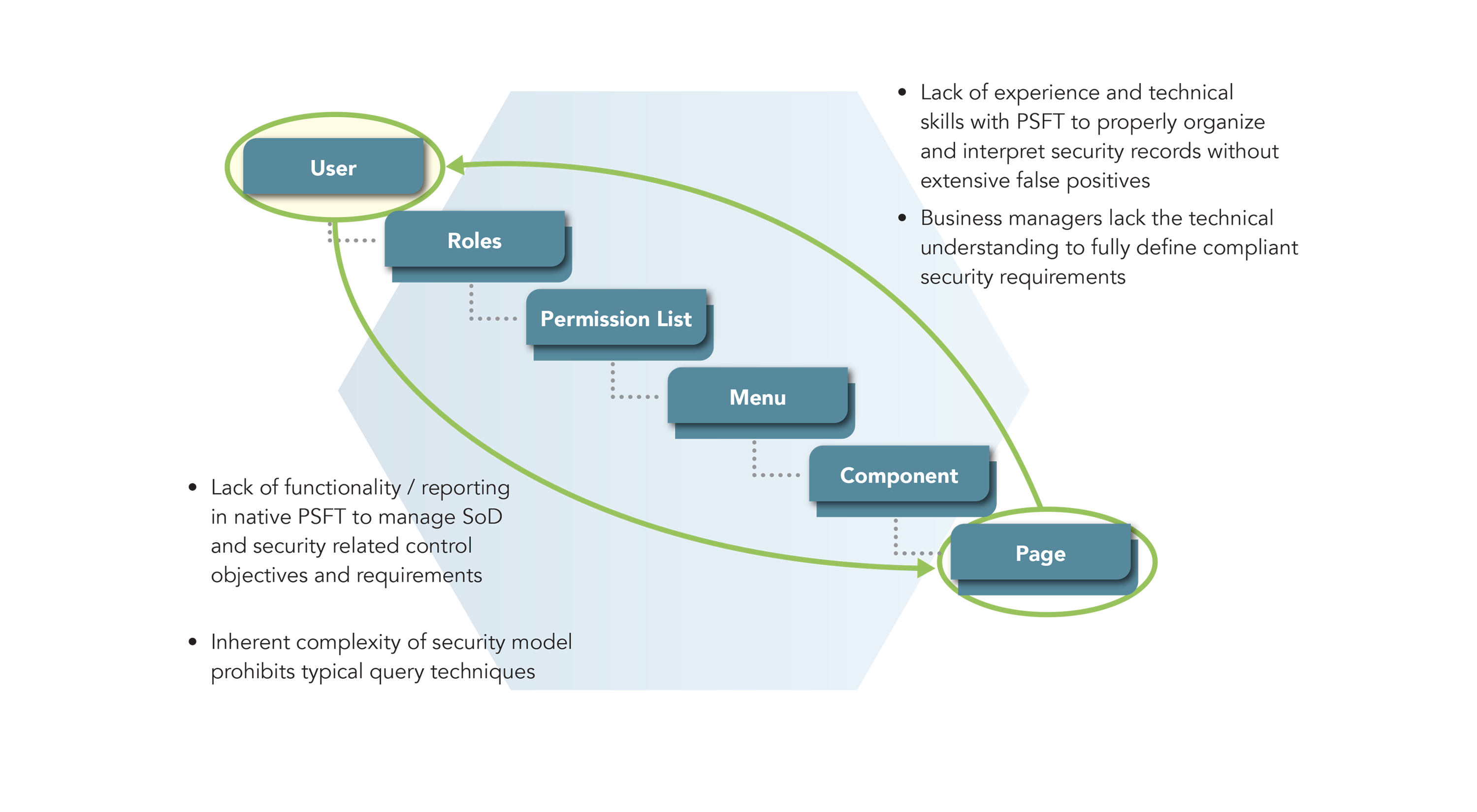
Segregation of Duties for PeopleSoft
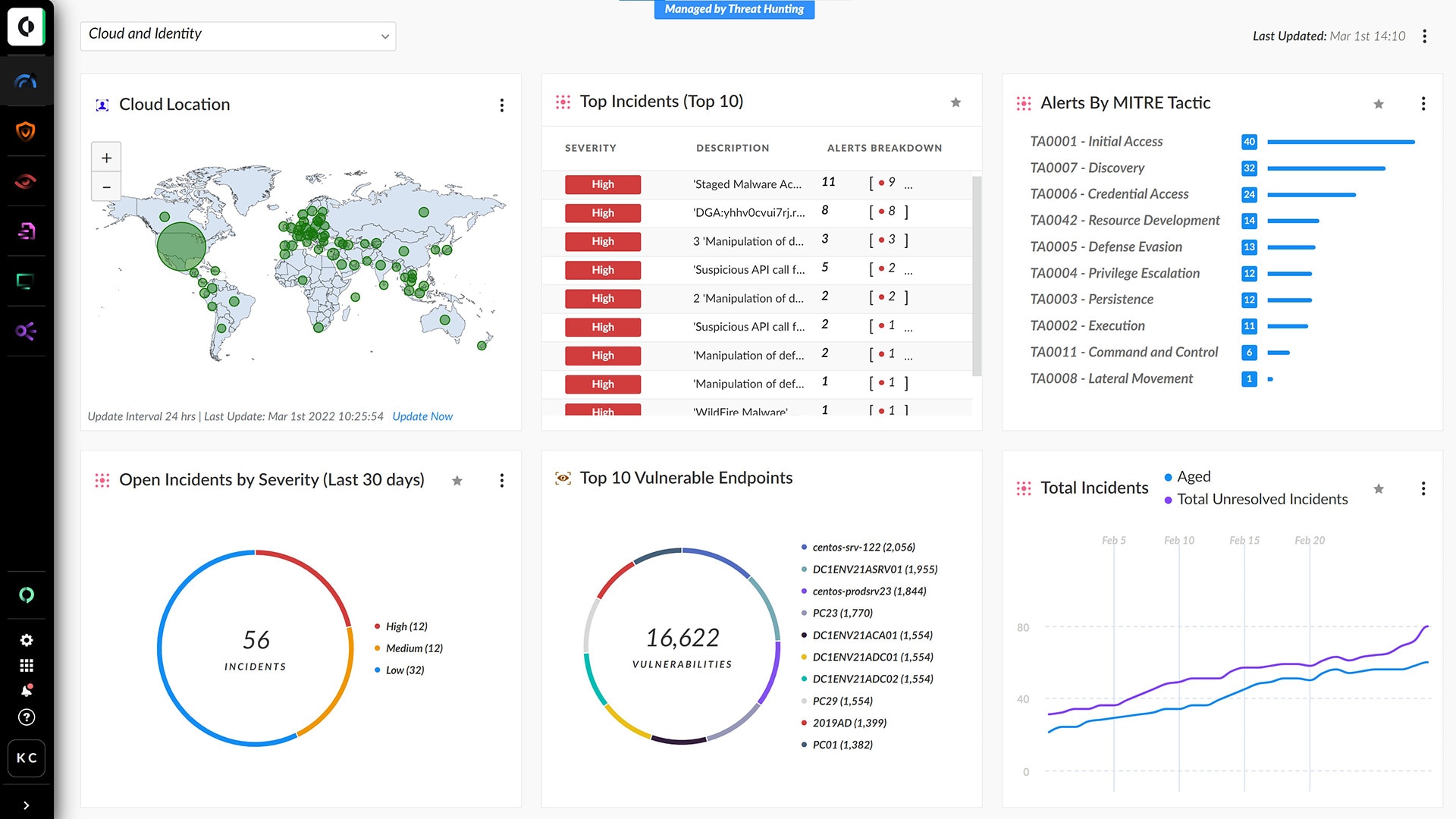
Cortex XDR- Extended Detection and Response - Palo Alto Networks

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks

Protect Your Device Your Way with Samsung Auto Blocker – Samsung Newsroom U.K.

Phishing attacks: defending your organisation
Taking Back Control of Your SOC with Risk Based Alerting

Essential Cybersecurity Controls for Organizations - Evergreen Insurance, LLC.

Suspicious User Controls
Hunting for Suspicious DNS Requests with Short Domain Extensions

Insider Threat Detection Recommendations
Recomendado para você
-
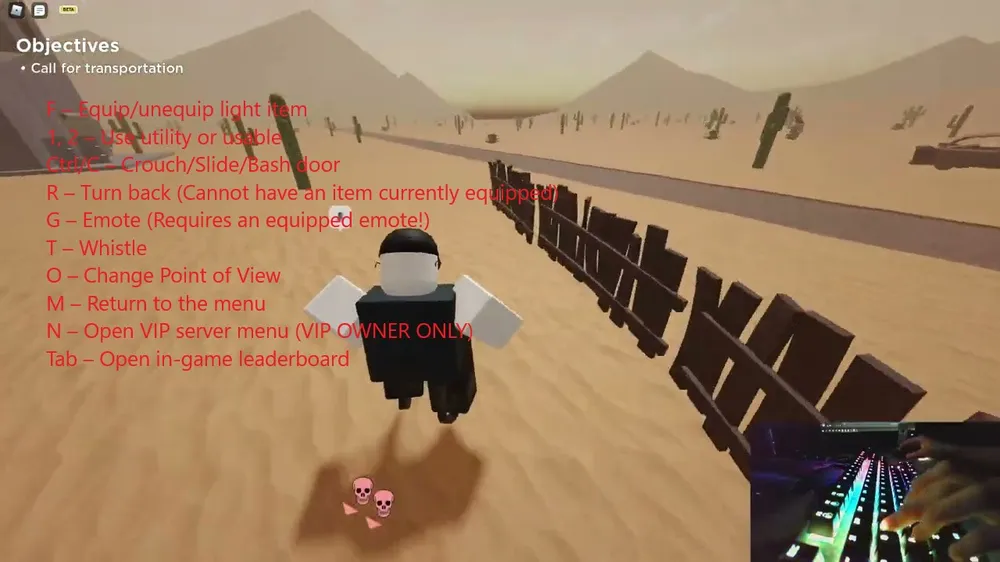 Evade Roblox – What is it, How to play, Codes, and More15 abril 2025
Evade Roblox – What is it, How to play, Codes, and More15 abril 2025 -
 Evade Roblox Tips, Tricks & Controls Guide - The Helpful Gamer15 abril 2025
Evade Roblox Tips, Tricks & Controls Guide - The Helpful Gamer15 abril 2025 -
Steam 社区 :: 指南 :: Setting Up NieR:Automata To Play With Keyboard And Mouse15 abril 2025
-
 Evade, Control Wiki15 abril 2025
Evade, Control Wiki15 abril 2025 -
 Never had a bad day phishing. How to set up GoPhish to evade security controls.15 abril 2025
Never had a bad day phishing. How to set up GoPhish to evade security controls.15 abril 2025 -
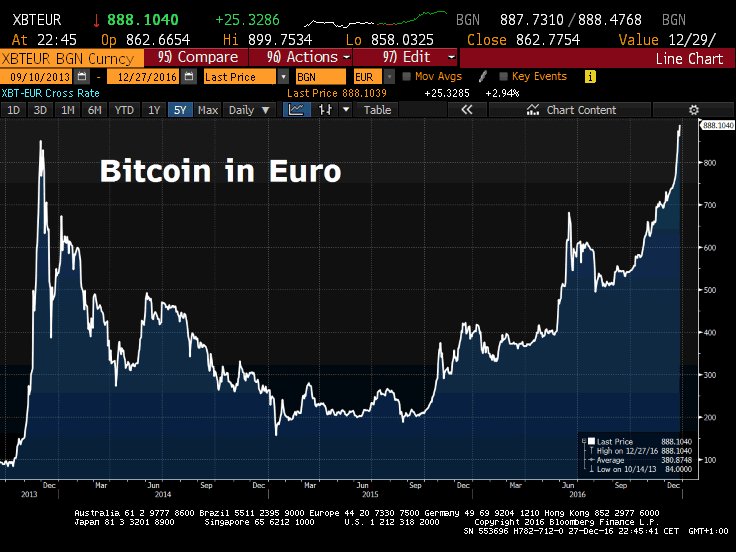 Holger Zschaepitz on X: #Bitcoin hit fresh life-time high vs Euro as Chinese & Indian investors hoping to evade capital controls & circumnavigate cash restrictions. / X15 abril 2025
Holger Zschaepitz on X: #Bitcoin hit fresh life-time high vs Euro as Chinese & Indian investors hoping to evade capital controls & circumnavigate cash restrictions. / X15 abril 2025 -
 Control: How To Get The 'Evade' Ability15 abril 2025
Control: How To Get The 'Evade' Ability15 abril 2025 -
Turnip Boy Commits Tax Evasion for Nintendo Switch - Nintendo Official Site15 abril 2025
-
 DEAD OR ALIVE 4: BASIC CONTROLS Punch - Paper Street15 abril 2025
DEAD OR ALIVE 4: BASIC CONTROLS Punch - Paper Street15 abril 2025 -
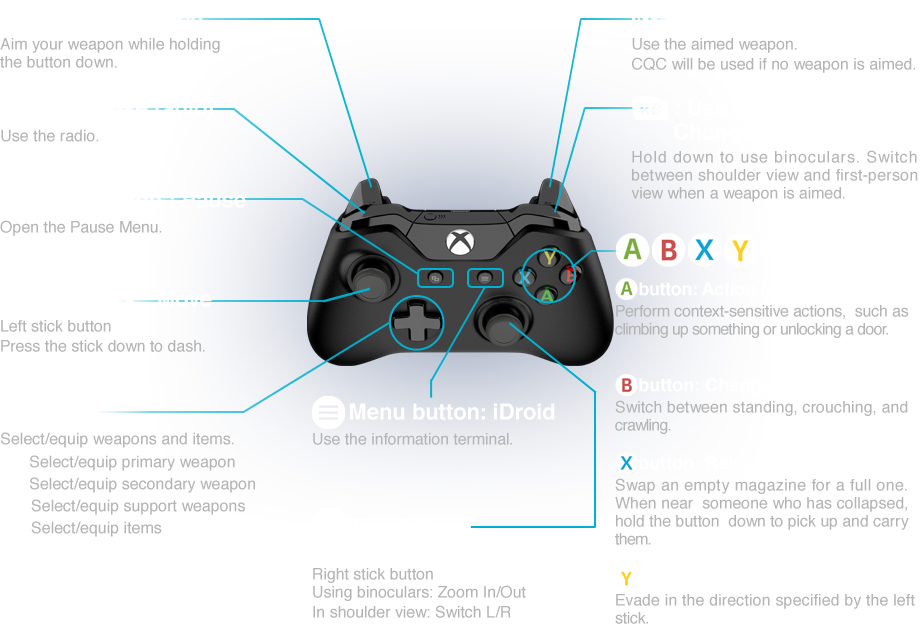 METAL GEAR SOLID V: GROUND ZEROES15 abril 2025
METAL GEAR SOLID V: GROUND ZEROES15 abril 2025
você pode gostar
-
 blox fruits cia 1 map location15 abril 2025
blox fruits cia 1 map location15 abril 2025 -
 Why Cobra Kai season 6 should be its last15 abril 2025
Why Cobra Kai season 6 should be its last15 abril 2025 -
 GTA Sindacco Chronicles just release, a total conversion mod for15 abril 2025
GTA Sindacco Chronicles just release, a total conversion mod for15 abril 2025 -
 Novo filme de Jogos Vorazes divulga tributos em novas imagens15 abril 2025
Novo filme de Jogos Vorazes divulga tributos em novas imagens15 abril 2025 -
 Nacional Club – Espaço para Eventos, Recepções e Buffet para15 abril 2025
Nacional Club – Espaço para Eventos, Recepções e Buffet para15 abril 2025 -
SMPS Boston - Meet Marsha Miller! Marsha is responsible for all things business development for Vanderweil Engineers in Boston, MA. In addition to serving as Director of Outreach for SMPS, Marsha is15 abril 2025
-
 Game FIFA 22 - Xbox em Promoção na Americanas15 abril 2025
Game FIFA 22 - Xbox em Promoção na Americanas15 abril 2025 -
 21 22 23 Hajduk Split VUSKOVIC KACANIKLIC Men World Cup 2022 Jerseys COLINA VUKOVIC K. DIMITROV Home Away Blue Red Shirt Short Sleeves Adult Uniforms From Sportjersey8, $13.5615 abril 2025
21 22 23 Hajduk Split VUSKOVIC KACANIKLIC Men World Cup 2022 Jerseys COLINA VUKOVIC K. DIMITROV Home Away Blue Red Shirt Short Sleeves Adult Uniforms From Sportjersey8, $13.5615 abril 2025 -
 A Game of Thrones: The Card Game 2nd Edition // Online Tournaments // Friendly Open15 abril 2025
A Game of Thrones: The Card Game 2nd Edition // Online Tournaments // Friendly Open15 abril 2025 -
 Roblox All Star Tower Defense New Code December 202315 abril 2025
Roblox All Star Tower Defense New Code December 202315 abril 2025