11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 19 abril 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.
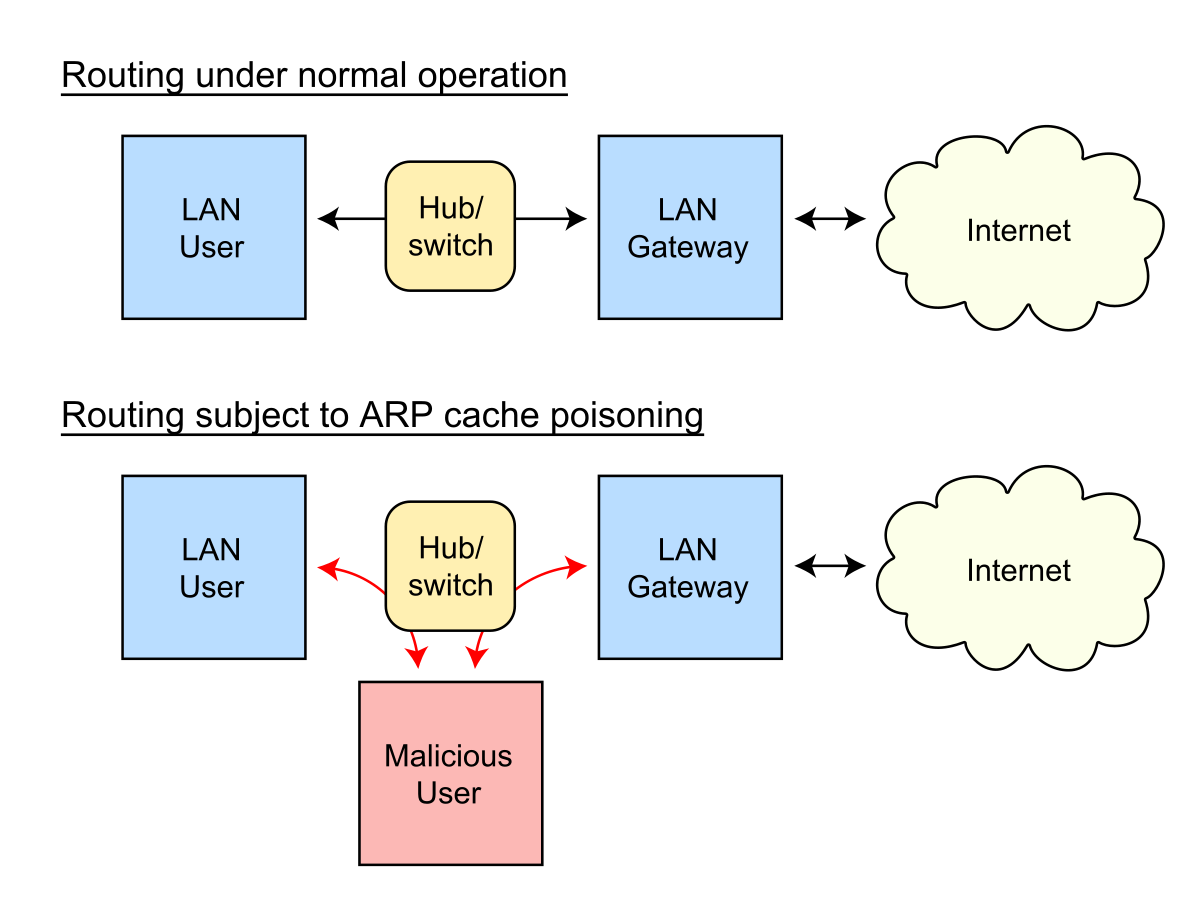
ARP spoofing - Wikipedia
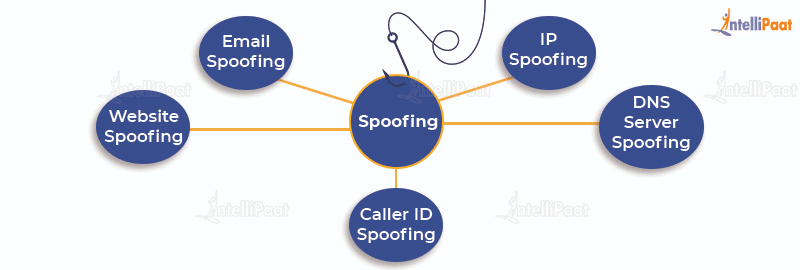
Spoofing vs Phishing - Difference between Phishing and Spoofing

What is email spoofing? A complete guide - Norton

6 Common Phishing Attacks and How to Protect Against Them

As biometrics adoption surges, anti-spoofing is non-negotiable

Spoofing Attacks, Spoofing Vs Phishing

What is IP Spoofing? Definition, Types & Protection

Sensors, Free Full-Text

Cyber Security Terms Everyone Should Know- ThriveDX

Don't Be Fooled By A Spoofing Attack
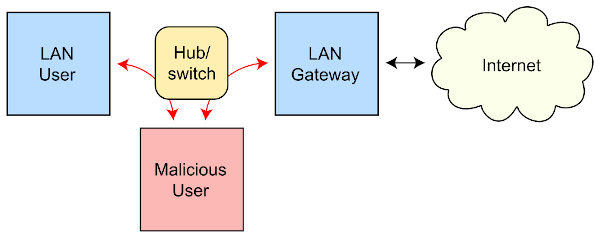
11 Types of Spoofing Attacks You Should Know About

Cyber Security Terms Everyone Should Know- ThriveDX
Recomendado para você
-
Bbc android iplayer download19 abril 2025
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG19 abril 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG19 abril 2025 -
 Risk Intelligence & Device Fingerprinting Solution19 abril 2025
Risk Intelligence & Device Fingerprinting Solution19 abril 2025 -
 1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for19 abril 2025
1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for19 abril 2025 -
 Interfacing with CAST Navigation GNSS/INS Simulation Solutions19 abril 2025
Interfacing with CAST Navigation GNSS/INS Simulation Solutions19 abril 2025 -
 Beware of Spoof Websites - RCB Bank19 abril 2025
Beware of Spoof Websites - RCB Bank19 abril 2025 -
 GootBot - Gootloader's new approach to post-exploitation19 abril 2025
GootBot - Gootloader's new approach to post-exploitation19 abril 2025 -
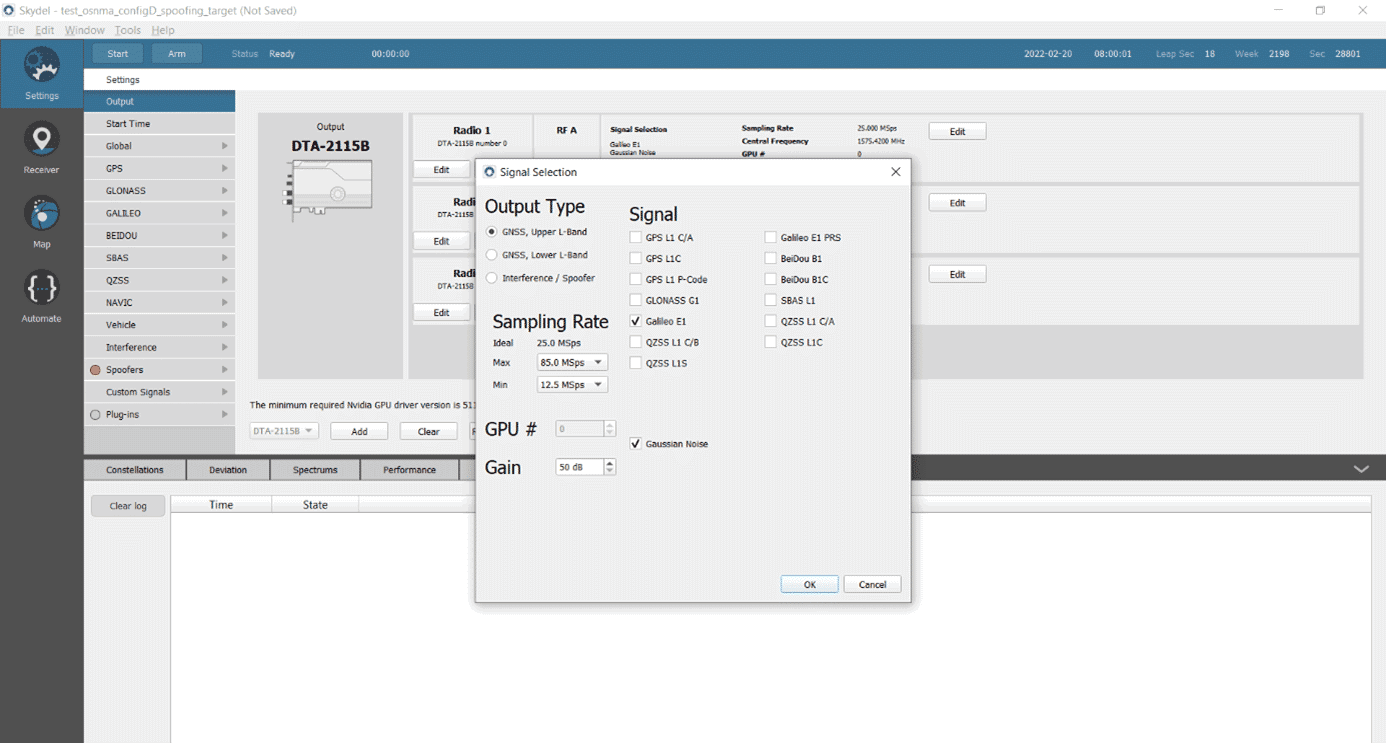 Testing a Receiver's Galileo OS-NMA Capability Using Skydel19 abril 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel19 abril 2025 -
 DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural19 abril 2025
DeepPOSE: Detecting GPS spoofing attack via deep recurrent neural19 abril 2025 -
 Autonomous aerial robotics for package delivery: A technical19 abril 2025
Autonomous aerial robotics for package delivery: A technical19 abril 2025
você pode gostar
-
 Marvel Heroes and Villains — NATE JONES DESIGN19 abril 2025
Marvel Heroes and Villains — NATE JONES DESIGN19 abril 2025 -
 Mamahaha no Tsurego ga Moto Kano datta (Manga) - NeoSekai Translations19 abril 2025
Mamahaha no Tsurego ga Moto Kano datta (Manga) - NeoSekai Translations19 abril 2025 -
Resident Evil: Origins Collection - PlayStation 419 abril 2025
-
 How To Get Out Of Toxic Friendships - KDM Counseling Group19 abril 2025
How To Get Out Of Toxic Friendships - KDM Counseling Group19 abril 2025 -
 Gregory van der Wiel - Swimsuit19 abril 2025
Gregory van der Wiel - Swimsuit19 abril 2025 -
 Camisas do Besiktas 2016-2017 Adidas » Mantos do Futebol19 abril 2025
Camisas do Besiktas 2016-2017 Adidas » Mantos do Futebol19 abril 2025 -
 O INCRÍVEL GAME DO HOMEM ARANHA DO PS219 abril 2025
O INCRÍVEL GAME DO HOMEM ARANHA DO PS219 abril 2025 -
 Dva penala donela pobedu Radničkom nad Javorom : Sport : Južne vesti19 abril 2025
Dva penala donela pobedu Radničkom nad Javorom : Sport : Južne vesti19 abril 2025 -
 Pin de Fabio em Salvamentos rápidos em 202319 abril 2025
Pin de Fabio em Salvamentos rápidos em 202319 abril 2025 -
 Seminario vescovile hi-res stock photography and images - Alamy19 abril 2025
Seminario vescovile hi-res stock photography and images - Alamy19 abril 2025
