Vare Stealer - Malware removal instructions
Por um escritor misterioso
Last updated 26 abril 2025
The Use of Cryptocurrencies as a Tool for the Development of Marketing in Tourism
Frontiers The Impact of Diet on the Involvement of Non-Coding RNAs, Extracellular Vesicles, and Gut Microbiome-Virome in Colorectal Cancer Initiation and Progression

Software Attacks (1 of 5), PDF, Denial Of Service Attack
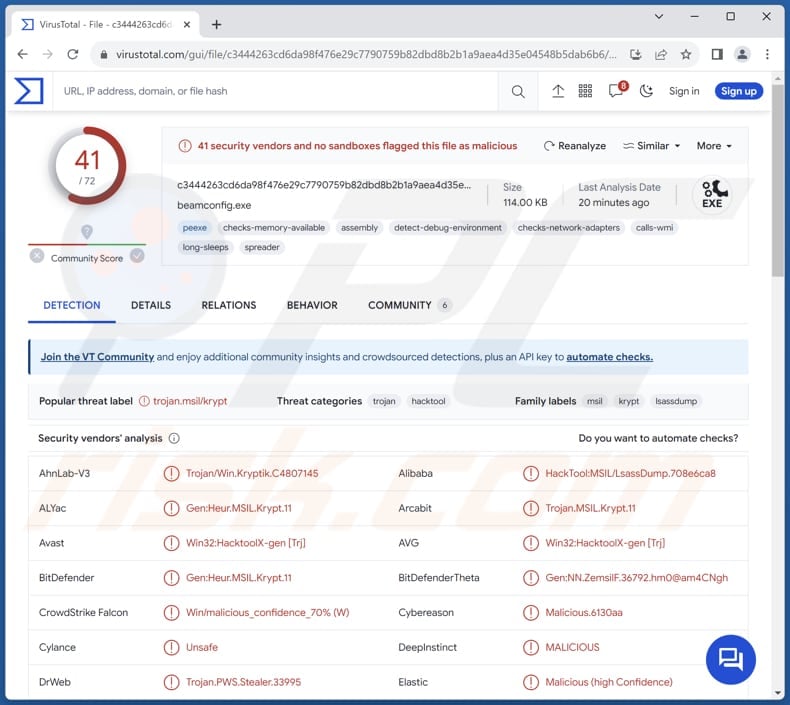
Malware analysis Malicious activity

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect

Artificial intelligence for cybersecurity: Literature review and future research directions - ScienceDirect

Vare Stealer Removal

How to use Windows Malicious Software Removal Tool - 2022 Tutorial

Cyber Security News 15/03/2021 - Swascan
Recomendado para você
-
 People Make Games Exploited Me For Views on Roblox.26 abril 2025
People Make Games Exploited Me For Views on Roblox.26 abril 2025 -
 Private Servers, Blox Fruits Wiki26 abril 2025
Private Servers, Blox Fruits Wiki26 abril 2025 -
Roblox Cancel Pending Requests26 abril 2025
-
 How to UNFRIEND people in the FASTEST & EASIEST way!! Roblox26 abril 2025
How to UNFRIEND people in the FASTEST & EASIEST way!! Roblox26 abril 2025 -
 How to Remove Friends on Roblox Fast by Using Friend Removal Button26 abril 2025
How to Remove Friends on Roblox Fast by Using Friend Removal Button26 abril 2025 -
 Download Roblox Friend Removal Button 1.1.0 CRX File for Chrome26 abril 2025
Download Roblox Friend Removal Button 1.1.0 CRX File for Chrome26 abril 2025 -
 Why, ROBLOXWHY? : r/roblox26 abril 2025
Why, ROBLOXWHY? : r/roblox26 abril 2025 -
 How To Remove All Friends on Roblox26 abril 2025
How To Remove All Friends on Roblox26 abril 2025 -
 remove friend roblox extension26 abril 2025
remove friend roblox extension26 abril 2025 -
 Do your kids play Roblox? Don't let them download this Chrome26 abril 2025
Do your kids play Roblox? Don't let them download this Chrome26 abril 2025
você pode gostar
-
 SOLUTION: Pdfcoffee com oisd std 154 pdf jp9667pdf pdf free - Studypool26 abril 2025
SOLUTION: Pdfcoffee com oisd std 154 pdf jp9667pdf pdf free - Studypool26 abril 2025 -
 Fundy, Monster Legends Competitive Wiki26 abril 2025
Fundy, Monster Legends Competitive Wiki26 abril 2025 -
 Papa Louie When Pizzas Attack: Walkthrough First Floor 🍕26 abril 2025
Papa Louie When Pizzas Attack: Walkthrough First Floor 🍕26 abril 2025 -
 God of War Ragnarok: Kratos — Secret Compass26 abril 2025
God of War Ragnarok: Kratos — Secret Compass26 abril 2025 -
 Texas Parks and Wildlife Now Has a SWAT Team : r/texas26 abril 2025
Texas Parks and Wildlife Now Has a SWAT Team : r/texas26 abril 2025 -
 Topo de Bolo Barbie Princesa Glitter com Arquivo Grátis26 abril 2025
Topo de Bolo Barbie Princesa Glitter com Arquivo Grátis26 abril 2025 -
 Rurouni Kenshin, Vol. 4, Book by Nobuhiro Watsuki, Official Publisher Page26 abril 2025
Rurouni Kenshin, Vol. 4, Book by Nobuhiro Watsuki, Official Publisher Page26 abril 2025 -
 Forza Horizon 3 Review: The big gets bigger26 abril 2025
Forza Horizon 3 Review: The big gets bigger26 abril 2025 -
Zuckerberg Circles Traffic Lights in Real-Life Captcha Joke26 abril 2025
-
 Glenn Frey - True Love26 abril 2025
Glenn Frey - True Love26 abril 2025