Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 22 abril 2025
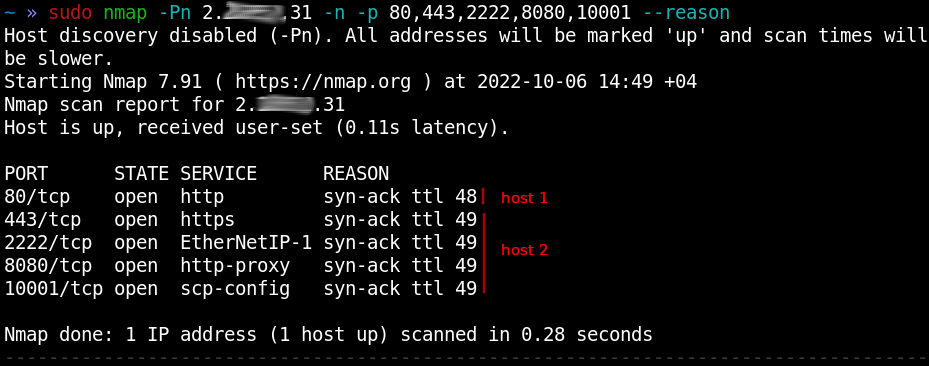

HackMag – Page 2 – Security, malware, coding, devops

Indiana systems falling prey to increasing hacks into medical records

Defending Byzantine attacks in ensemble federated learning: A
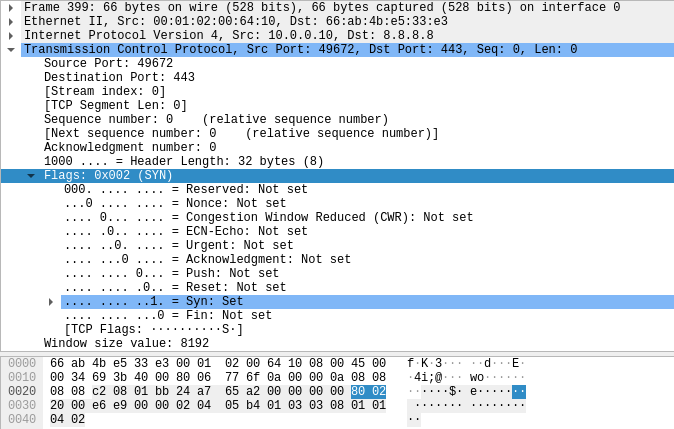
Kung fu enumeration. Data collection in attacked systems – HackMag

USDA is investigating a 'possible data breach' related to global
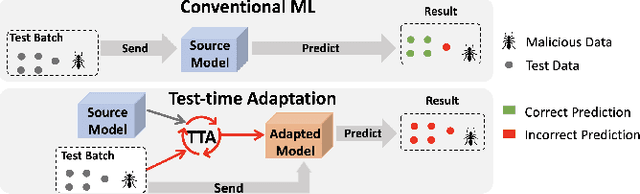
Xiangyu Qi - CatalyzeX
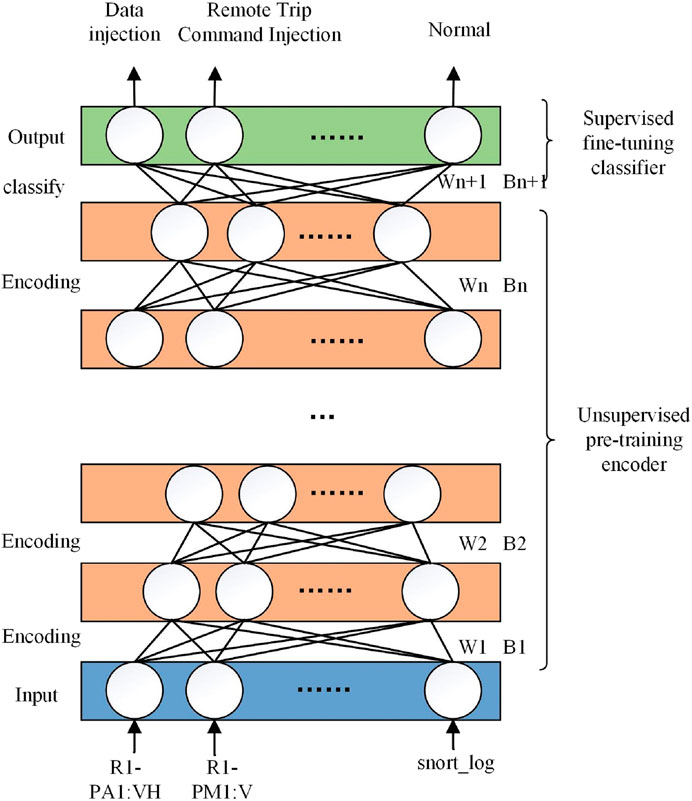
Frontiers False Data Injection Attack Detection in Power Systems

Selected Publications and Preprints - Yiming Li
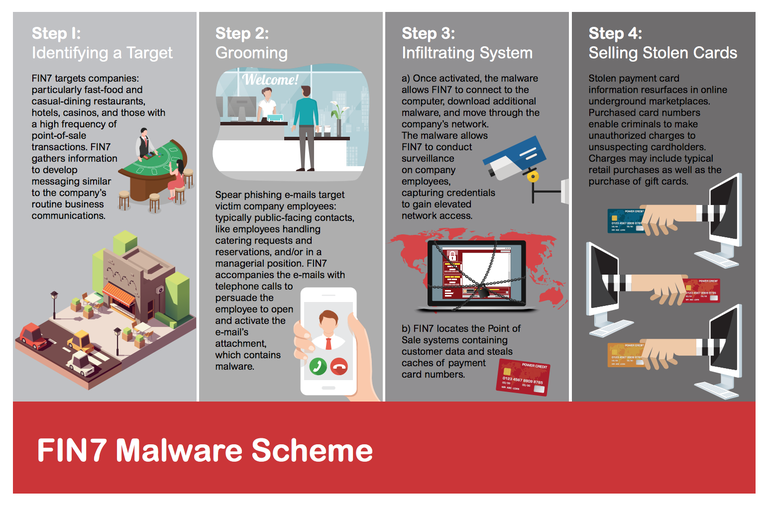
How Cyber Crime Group FIN7 Attacked and Stole Data from Hundreds
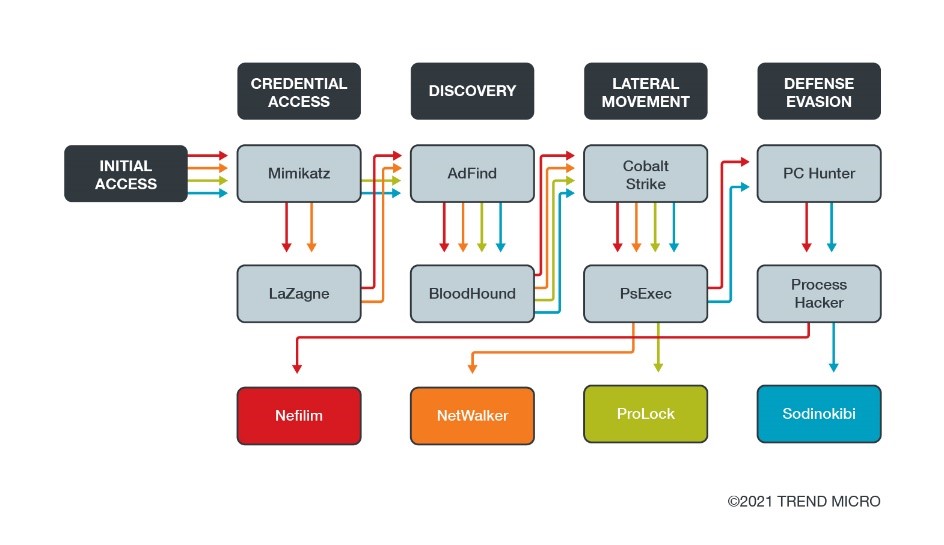
Locked, Loaded, and in the Wrong Hands: Legitimate Tools

X BLOCK effective ADVANCED TECHNIQUE - Kung Fu Report

Hamby's Tiger & Crane Kung Fu - Vol-7 12 Bridge Hands (Steel
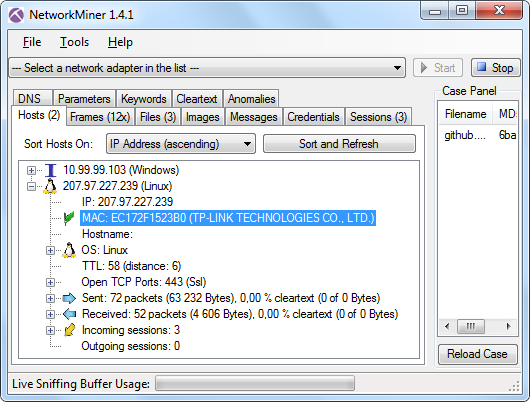
Forensics of Chinese MITM on GitHub
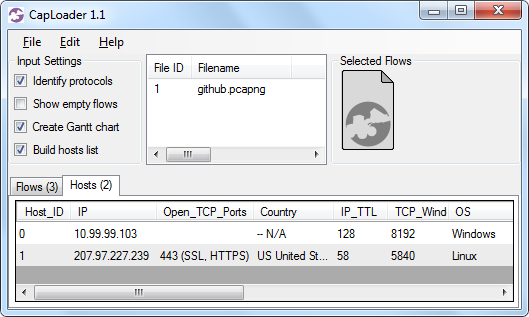
Forensics of Chinese MITM on GitHub
Recomendado para você
-
 SCP ref by Silverfang10001 on DeviantArt22 abril 2025
SCP ref by Silverfang10001 on DeviantArt22 abril 2025 -
Mummy Ana!! Yay for spooky season 😭🍂! #overwatchfanart22 abril 2025
-
 Elastos Info - Manifesto22 abril 2025
Elastos Info - Manifesto22 abril 2025 -
The SCP Foundation22 abril 2025
-
 Strange goings on - Services & Integrations - Wyze Forum22 abril 2025
Strange goings on - Services & Integrations - Wyze Forum22 abril 2025 -
 SCP reprocontrol for HP Designjet Printers - Reprocontrol.monitor22 abril 2025
SCP reprocontrol for HP Designjet Printers - Reprocontrol.monitor22 abril 2025 -
 Pixel Art — Shrinking. Painting a small image pixel by pixel…, by Joana Borges Late22 abril 2025
Pixel Art — Shrinking. Painting a small image pixel by pixel…, by Joana Borges Late22 abril 2025 -
 Astral Conflict - The RuneScape Wiki22 abril 2025
Astral Conflict - The RuneScape Wiki22 abril 2025 -
 SCP -- Bad Time--VIDEO IS OUT:. by XenomorphicDragon on DeviantArt22 abril 2025
SCP -- Bad Time--VIDEO IS OUT:. by XenomorphicDragon on DeviantArt22 abril 2025 -
 Best Executioner Mask Royalty-Free Images, Stock Photos & Pictures22 abril 2025
Best Executioner Mask Royalty-Free Images, Stock Photos & Pictures22 abril 2025
você pode gostar
-
 Resident Evil 4 Albert Wesker22 abril 2025
Resident Evil 4 Albert Wesker22 abril 2025 -
 1,000 + Calcudoku sudoku 6x6: Logic puzzles hard - extreme levels (Sudoku CalcuDoku): Holmes, Basford: 9781676199922: : Books22 abril 2025
1,000 + Calcudoku sudoku 6x6: Logic puzzles hard - extreme levels (Sudoku CalcuDoku): Holmes, Basford: 9781676199922: : Books22 abril 2025 -
 Mortal Kombat 2': Atriz do primeiro filme NÃO voltará para sequência - CinePOP22 abril 2025
Mortal Kombat 2': Atriz do primeiro filme NÃO voltará para sequência - CinePOP22 abril 2025 -
 Randomness and Lyfe Stuff - John Doe (Roblox) - Wattpad22 abril 2025
Randomness and Lyfe Stuff - John Doe (Roblox) - Wattpad22 abril 2025 -
 Shizu tensura slime iphone rimuru soei in 202322 abril 2025
Shizu tensura slime iphone rimuru soei in 202322 abril 2025 -
 Crunchyroll APK Download for Android Free - Anime22 abril 2025
Crunchyroll APK Download for Android Free - Anime22 abril 2025 -
 How to Use Cheat Engine on BlueStacks Android Emulator22 abril 2025
How to Use Cheat Engine on BlueStacks Android Emulator22 abril 2025 -
 Highschool of the Dead (Color Edition), Vol. 3 Manga eBook by22 abril 2025
Highschool of the Dead (Color Edition), Vol. 3 Manga eBook by22 abril 2025 -
 Disney Moana Princesa Vestidos para Meninas, Trajes Cosplay, Roupas Vaiana, Festa para 3, 6, 8, 10 Anos Menina Roupa, Presente - AliExpress22 abril 2025
Disney Moana Princesa Vestidos para Meninas, Trajes Cosplay, Roupas Vaiana, Festa para 3, 6, 8, 10 Anos Menina Roupa, Presente - AliExpress22 abril 2025 -
 16 ideias de Uniforme id bloxburg roblox, foto de roupas, roupas de personagens22 abril 2025
16 ideias de Uniforme id bloxburg roblox, foto de roupas, roupas de personagens22 abril 2025

