Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 15 abril 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Cyberattack Disrupts Hospital Computer Systems Across US, Oregon

Technical Advisory – New York State Excelsior Pass Vaccine

Google Play threat market: overview of dark web offers

Basic principle of code reuse attacks. For simplicity, we

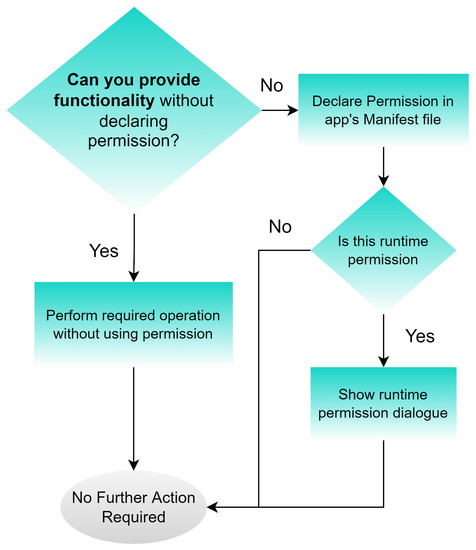
Android Applications Pentesting - HackTricks

Objective-See
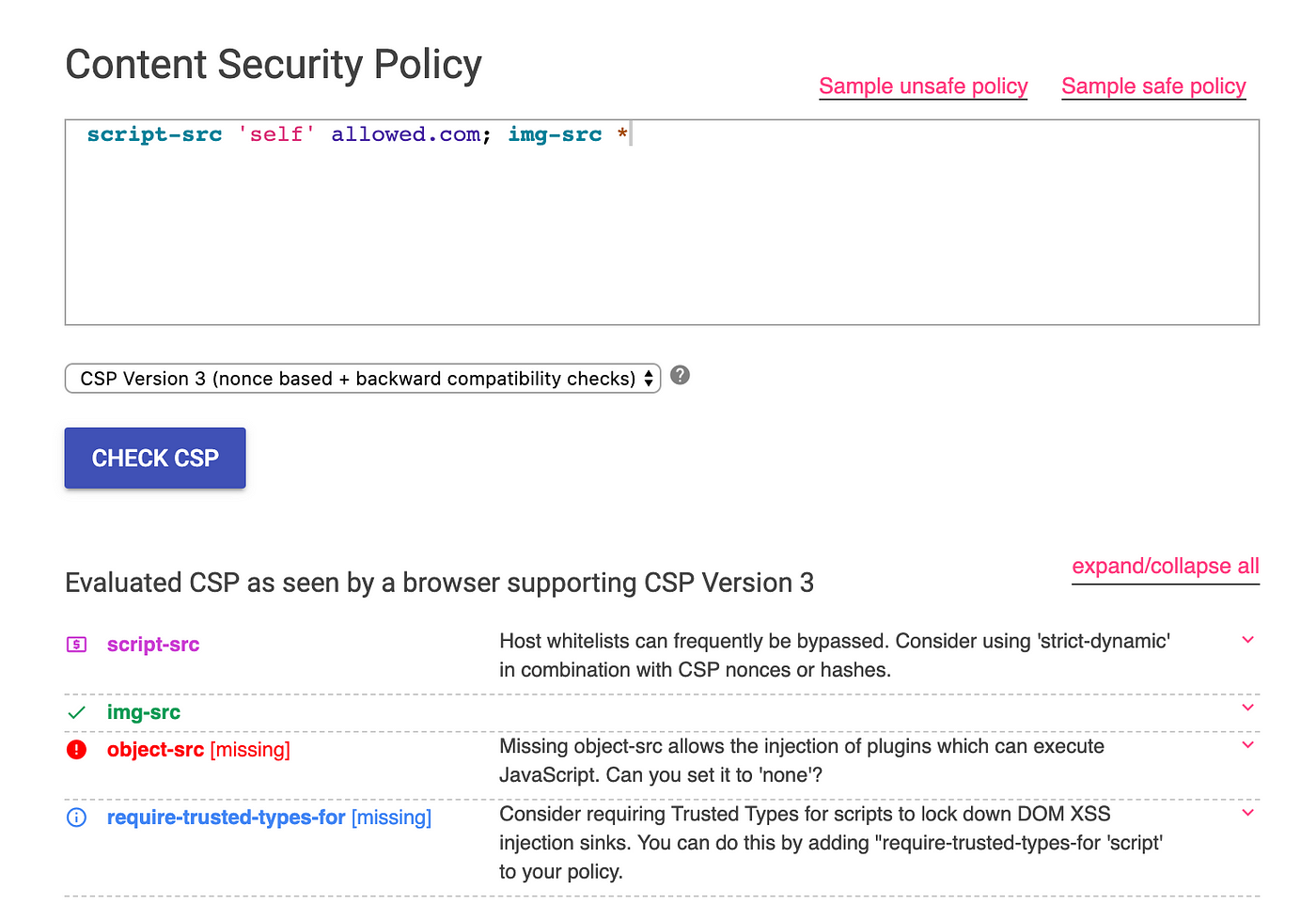
Content Security Bypass Techniques to perform XSS

What Is Rootkit?
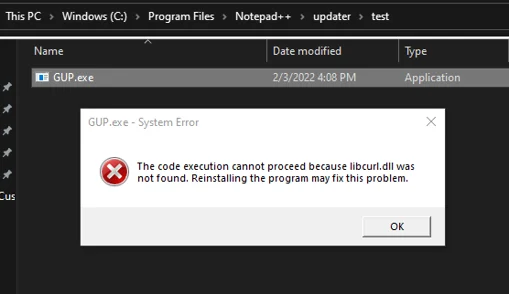
THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Used
Technologies, Free Full-Text
Recomendado para você
-
 Roblox: Evade Codes15 abril 2025
Roblox: Evade Codes15 abril 2025 -
 All Roblox Zo Samurai codes for free Shards & Spins in December15 abril 2025
All Roblox Zo Samurai codes for free Shards & Spins in December15 abril 2025 -
Codes, Roblox Evade Wiki15 abril 2025
-
 Evade Codes November 2023 - Pillar Of Gaming15 abril 2025
Evade Codes November 2023 - Pillar Of Gaming15 abril 2025 -
 Utilizing Morse Code to Evade Signature Based Detection Systems15 abril 2025
Utilizing Morse Code to Evade Signature Based Detection Systems15 abril 2025 -
 Codes Roblox Evolution Evade (août 2021)15 abril 2025
Codes Roblox Evolution Evade (août 2021)15 abril 2025 -
 NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade15 abril 2025
NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade15 abril 2025 -
 roblox evade song ids 2023 june|TikTok Search15 abril 2025
roblox evade song ids 2023 june|TikTok Search15 abril 2025 -
Instagram photo by Derrick Van Orden • Oct 1, 2023 at 5:51 AM15 abril 2025
-
 20% Off Evade PROMO CODE, COUPONS October 202315 abril 2025
20% Off Evade PROMO CODE, COUPONS October 202315 abril 2025
você pode gostar
-
 PlayStation Store $25 Gift Card15 abril 2025
PlayStation Store $25 Gift Card15 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_da025474c0c44edd99332dddb09cabe8/internal_photos/bs/2022/r/z/6KAKr6Q3aLOdAUUEmPew/101626338-a-fan-holds-t-shirt-bearing-the-name-ronaldo-and-number-7-at-the-saudi-al-nassr-fc-sho.jpg) Contratação de Cristiano Ronaldo causa correria às lojas por15 abril 2025
Contratação de Cristiano Ronaldo causa correria às lojas por15 abril 2025 -
 Pin em Jogos Educativos15 abril 2025
Pin em Jogos Educativos15 abril 2025 -
 Chess for Beginners: A Comprehensive Guide to Chess Openings by Magnus Templar - Audiobook15 abril 2025
Chess for Beginners: A Comprehensive Guide to Chess Openings by Magnus Templar - Audiobook15 abril 2025 -
 CapCut_madagascar motomoto saindo da água15 abril 2025
CapCut_madagascar motomoto saindo da água15 abril 2025 -
 Polly Pocket - Casa Do Lago Da Polly Gigante C/ 36 Cm - Alfabay15 abril 2025
Polly Pocket - Casa Do Lago Da Polly Gigante C/ 36 Cm - Alfabay15 abril 2025 -
 Natureza Estranha - Animais Bizarros - Quebra-cabeça - 500 peças - Toyster Brinquedos - Toyster15 abril 2025
Natureza Estranha - Animais Bizarros - Quebra-cabeça - 500 peças - Toyster Brinquedos - Toyster15 abril 2025 -
 Alan Wake Remastered - Part 1 - ITS FINALLY HERE15 abril 2025
Alan Wake Remastered - Part 1 - ITS FINALLY HERE15 abril 2025 -
 Ding Liren drops to rank #4 after losing a World Championship match15 abril 2025
Ding Liren drops to rank #4 after losing a World Championship match15 abril 2025 -
 Baixa pressão combustível bomba filtro módulo, remetente unidade Assy 16117243974 para BMW 3 F30 320i 328i 335i, novo - AliExpress15 abril 2025
Baixa pressão combustível bomba filtro módulo, remetente unidade Assy 16117243974 para BMW 3 F30 320i 328i 335i, novo - AliExpress15 abril 2025

