Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix
Por um escritor misterioso
Last updated 22 abril 2025
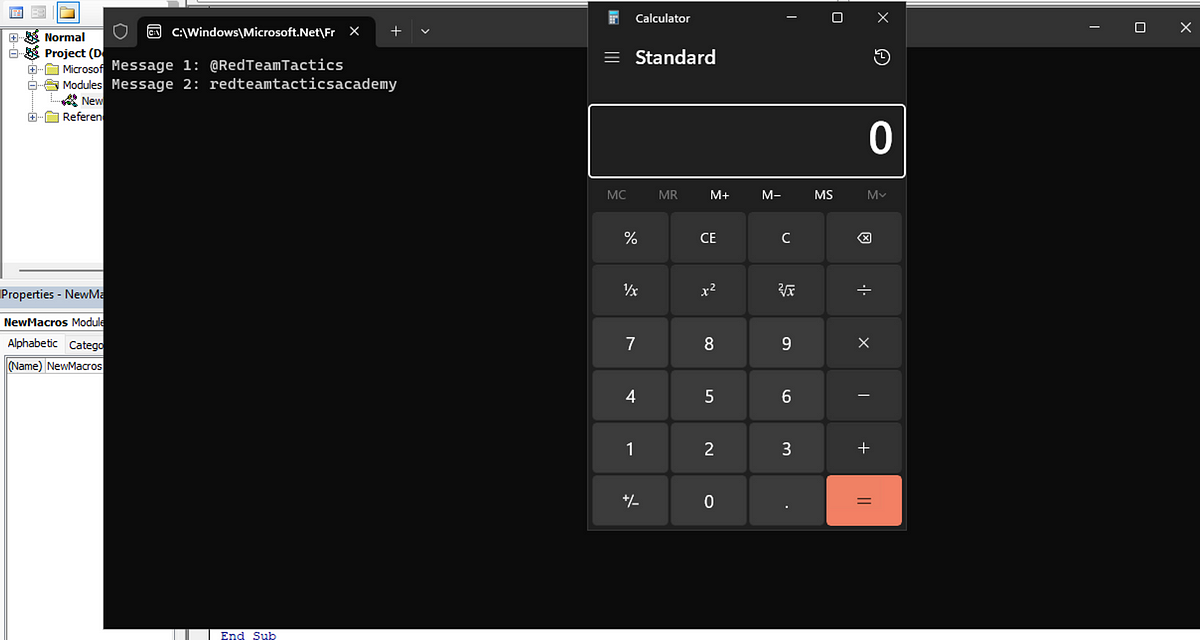
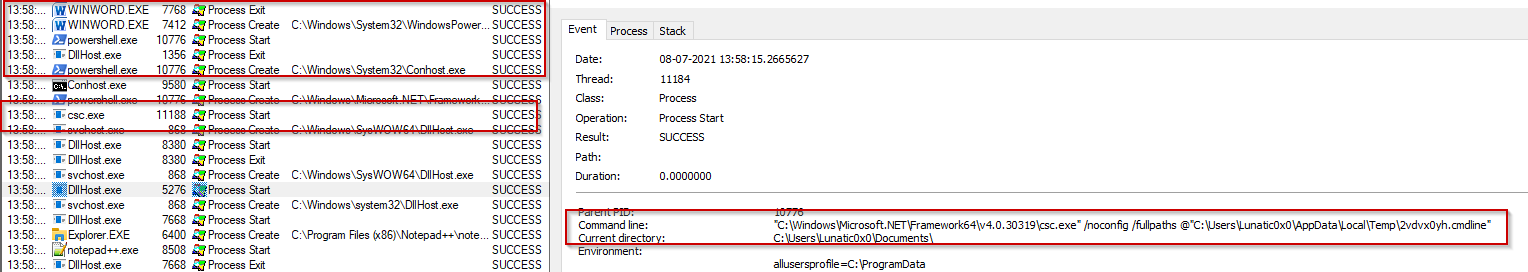
LOLBins Are No Laughing Matter: How Attackers Operate Quietly

Rhizosphere control of soil nitrogen cycling: a key component of plant economic strategies - Henneron - 2020 - New Phytologist - Wiley Online Library

How Do Attackers Use LOLBins In Fileless Attacks? - Phoenix Technology Solutions
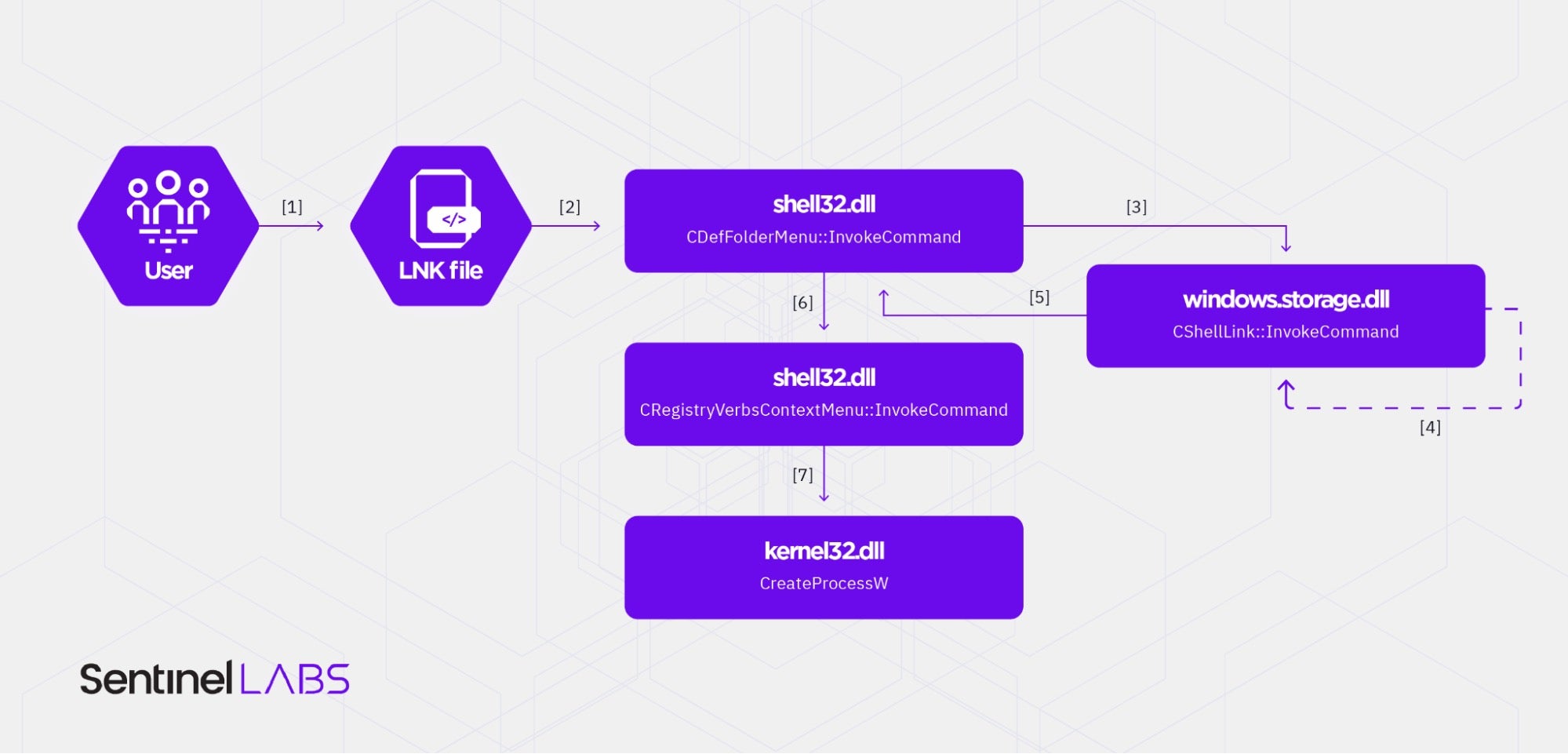
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne

Threat Hunting: From LOLBins to Your Crown Jewels

Bring your own LOLBin: Multi-stage, fileless Nodersok campaign delivers rare Node.js-based malware

What is a LOLBIN?. To me, the phrase 'Attackers Living off…, by Dan Crossley

LOLBins: how native tools are used to make threats stealthier

Hunting for LoLBins
Recomendado para você
-
 Cyber Era Codes Gift Code Wiki - MrGuider22 abril 2025
Cyber Era Codes Gift Code Wiki - MrGuider22 abril 2025 -
Dalarin22 abril 2025
-
 BINARY X - CYBER CHESS - FREE GIVEAWAYS22 abril 2025
BINARY X - CYBER CHESS - FREE GIVEAWAYS22 abril 2025 -
Chris Dale on LinkedIn: #security22 abril 2025
-
 CyberChess Weekly Rewards, Cyberland Trending22 abril 2025
CyberChess Weekly Rewards, Cyberland Trending22 abril 2025 -
 How to Play CyberChess? BinaryX CyberChess Tutorial with $140 Promo Code.22 abril 2025
How to Play CyberChess? BinaryX CyberChess Tutorial with $140 Promo Code.22 abril 2025 -
 Metamoonshots🚀 on X: 🚨 Attention all gamers! 🚨 Get ready to claim your 🔥 FREE NFTs 🔥 with BinaryX's latest launch - CyberChess! 🎉 Simply head to click on 'Game,' select22 abril 2025
Metamoonshots🚀 on X: 🚨 Attention all gamers! 🚨 Get ready to claim your 🔥 FREE NFTs 🔥 with BinaryX's latest launch - CyberChess! 🎉 Simply head to click on 'Game,' select22 abril 2025 -
The Only Guide You'll Need for CyberChess — plus How To Get Free22 abril 2025
-
 Metamoonshots🚀 on X: 🚨 Attention all gamers! 🚨 Get ready to22 abril 2025
Metamoonshots🚀 on X: 🚨 Attention all gamers! 🚨 Get ready to22 abril 2025 -
 CyberChess SEASON 3 STARTS! BinaryX Live Stream with PH Streamer22 abril 2025
CyberChess SEASON 3 STARTS! BinaryX Live Stream with PH Streamer22 abril 2025
você pode gostar
-
 Explore the Best Monsterpoint Art22 abril 2025
Explore the Best Monsterpoint Art22 abril 2025 -
New Friendships. New Adventures. Hello Kitty Island Adventure is22 abril 2025
-
 Scp 3008 Infinity Survivor APK Download for Android Free22 abril 2025
Scp 3008 Infinity Survivor APK Download for Android Free22 abril 2025 -
 Calendário da Copa do Mundo: veja tabela com os jogos das22 abril 2025
Calendário da Copa do Mundo: veja tabela com os jogos das22 abril 2025 -
 flyordie.com chess cheat22 abril 2025
flyordie.com chess cheat22 abril 2025 -
 Super Sonic Is Back In New Sonic Frontiers Trailer - Game Informer22 abril 2025
Super Sonic Is Back In New Sonic Frontiers Trailer - Game Informer22 abril 2025 -
 Facebook Marketing Strategy, Tips, Guides & News22 abril 2025
Facebook Marketing Strategy, Tips, Guides & News22 abril 2025 -
 Pokemon Go Plus review: This monster-catching button makes you less of a Pokemon zombie - CNET22 abril 2025
Pokemon Go Plus review: This monster-catching button makes you less of a Pokemon zombie - CNET22 abril 2025 -
 plantilla de diseño de calendario para 2022, el año del tigre según el calendario chino o oriental, con una ilustración del tigre. tabla horizontal con calendario para 2022. vector 3598272 Vector en Vecteezy22 abril 2025
plantilla de diseño de calendario para 2022, el año del tigre según el calendario chino o oriental, con una ilustración del tigre. tabla horizontal con calendario para 2022. vector 3598272 Vector en Vecteezy22 abril 2025 -
 Field Roast™️ Plant-Based Signature Stadium Dog Now Featured at22 abril 2025
Field Roast™️ Plant-Based Signature Stadium Dog Now Featured at22 abril 2025


