Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 22 abril 2025

Describing activities of a crime group attacking Ukraine.

Balancing act: countering digital disinformation while respecting freedom of expression: Broadband Commission research report on 'Freedom of Expression and Addressing Disinformation on the Internet
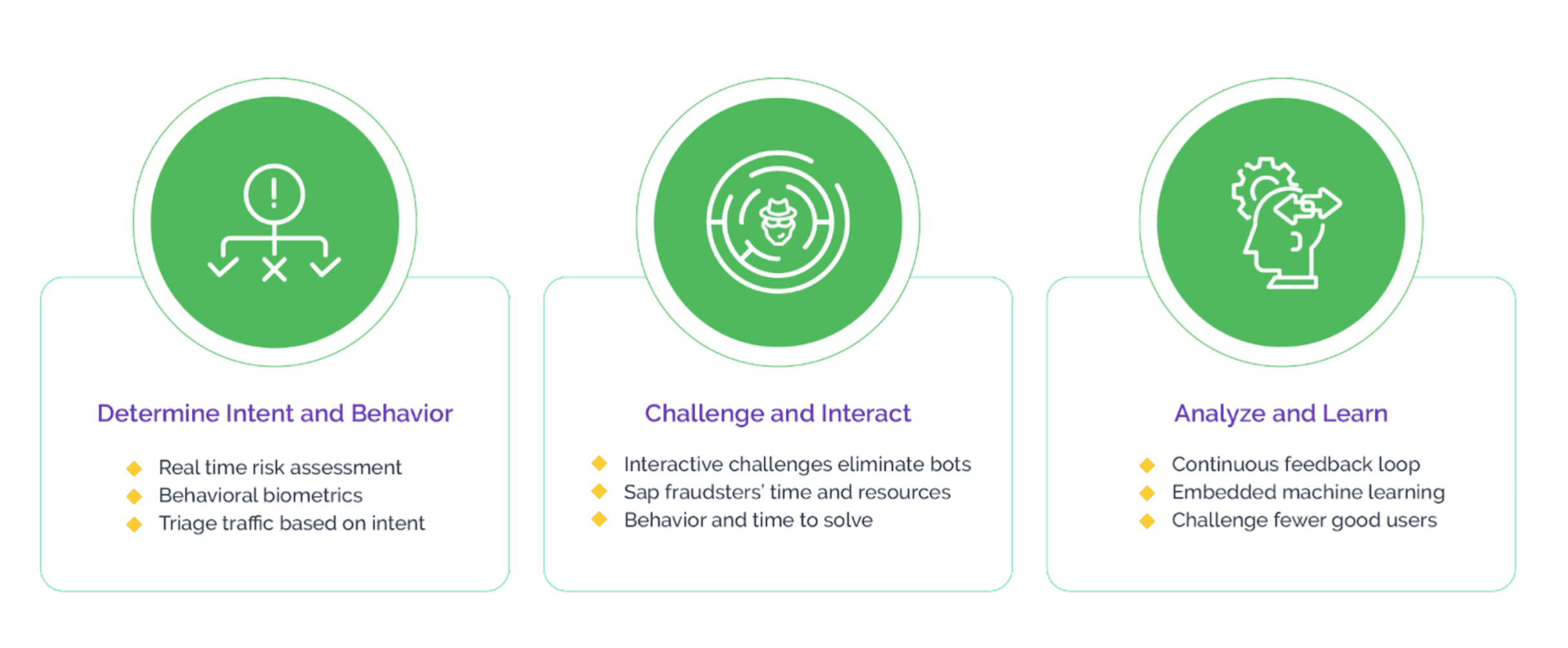
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Security in product lifecycle of IoT devices: A survey - ScienceDirect

Toward a New Momentum: Trend Micro Security Predictions for 2022 - Security Predictions

System model of attribute-based access control for proxy re-encryption

Security in product lifecycle of IoT devices: A survey - ScienceDirect

The Rise of Initial Access Brokers - ReliaQuest
GitHub - CyberMonitor/APT_CyberCriminal_Campagin_Collections: APT & CyberCriminal Campaign Collection

Growing Cybercrime Outsourcing Model: Initial Access Brokers

Targeted Cyberattacks: A Superset of Advanced Persistent Threats

Initial access broker repurposing techniques in targeted attacks against Ukraine
Recomendado para você
-
 Analysis Group New York22 abril 2025
Analysis Group New York22 abril 2025 -
Analysis Group HealthEconomics.com Jobs Portal22 abril 2025
-
 Analysis Group - Vault22 abril 2025
Analysis Group - Vault22 abril 2025 -
IAG, Image Analysis Group22 abril 2025
-
 Analysis Group Office Photos22 abril 2025
Analysis Group Office Photos22 abril 2025 -
 Annual Meeting of the Lunar Exploration Analysis Group22 abril 2025
Annual Meeting of the Lunar Exploration Analysis Group22 abril 2025 -
 Manager - Analysis Group22 abril 2025
Manager - Analysis Group22 abril 2025 -
 Human Rights Data Analysis Group - Wikipedia22 abril 2025
Human Rights Data Analysis Group - Wikipedia22 abril 2025 -
 Active North Korean campaign targeting security researchers22 abril 2025
Active North Korean campaign targeting security researchers22 abril 2025 -
 Job Listings at Analysis Group, Inc.22 abril 2025
Job Listings at Analysis Group, Inc.22 abril 2025
você pode gostar
-
 Ghost of Tsushima Director's Cut PS5 Review - Bigger, Bolder And More Beautiful Than Ever22 abril 2025
Ghost of Tsushima Director's Cut PS5 Review - Bigger, Bolder And More Beautiful Than Ever22 abril 2025 -
 Naruto: Guia Oficial De Personagens - O Livro Secreto Do Confronto22 abril 2025
Naruto: Guia Oficial De Personagens - O Livro Secreto Do Confronto22 abril 2025 -
 Axe VS Club - Comparing SOULEATER and SOULMAIMER22 abril 2025
Axe VS Club - Comparing SOULEATER and SOULMAIMER22 abril 2025 -
 Dino Jump22 abril 2025
Dino Jump22 abril 2025 -
 Sonhar com cabelo caindo - Confira 7 interpretações22 abril 2025
Sonhar com cabelo caindo - Confira 7 interpretações22 abril 2025 -
 Baixei Dark souls na steam verde, finalmente posso ser humilhado de diversas formas, quem quiser é só pedir na chat que eu ensino. - iFunny Brazil22 abril 2025
Baixei Dark souls na steam verde, finalmente posso ser humilhado de diversas formas, quem quiser é só pedir na chat que eu ensino. - iFunny Brazil22 abril 2025 -
Prevention and Control of a Staphylococcus aureus Infection22 abril 2025
-
 The Best Roblox Auto Clicker for Mobile! (Tutorial)22 abril 2025
The Best Roblox Auto Clicker for Mobile! (Tutorial)22 abril 2025 -
 TOP NOMES (masculinos) PARA USAR COMO NICK NO FREE FIRE🔥😱 MELHORES NOMES EM 202222 abril 2025
TOP NOMES (masculinos) PARA USAR COMO NICK NO FREE FIRE🔥😱 MELHORES NOMES EM 202222 abril 2025 -
 animehotgirl : Free Download, Borrow, and Streaming : Internet Archive22 abril 2025
animehotgirl : Free Download, Borrow, and Streaming : Internet Archive22 abril 2025

