Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 25 abril 2025
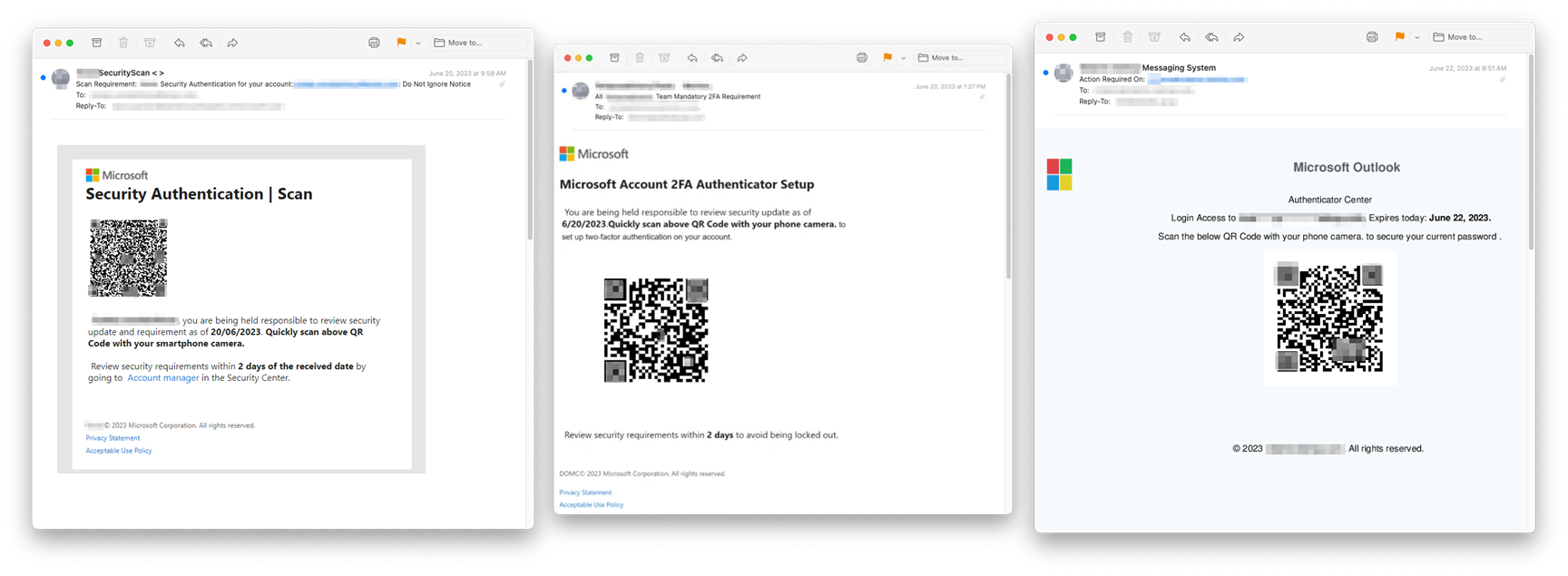
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't

News, Ironscales Combats Image-based Email Security Attacks with Latest Machine Learning Capabilities

Staying One Step Ahead: Advanced Techniques for Email Security

Cybercriminals Bypass OpenAI's Restrictions on Malicious Use

Antivirus & Malware Evasion Techniques

Understanding Phishing Emails: Why They Slip Through Spam Filters

Cybercrime and AI : same threats now powered with advanced technology - Michalsons

How AI Protects (and Attacks) Your Inbox: The Battle Against Email Threats by Nova Deer Cyber Productions LLC - Issuu

Cybercriminals use automated bot to bypass 2FA authentication at wide scale

The 10 Worst Cyber Crimes Analysed
Cyber Security For Email Communication: Why You need it and its Best Practices

300+ Terrifying Cybercrime & Cybersecurity Statistics (2023)

Cyberattackers Double Down on Bypassing MFA

New Perception Point and Osterman Research Report Shows

4 best email security tools you need in your stack

Fast Flux 101: How Cybercriminals Improve the Resilience of Their Infrastructure to Evade Detection and Law Enforcement Takedowns
Recomendado para você
-
 Roblox: Evade codes in December 202325 abril 2025
Roblox: Evade codes in December 202325 abril 2025 -
Roblox evade id codes pt.5 #roblox#evade#idcodesroblox#boombox@bananap, how to get boombox in evade25 abril 2025
-
 Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X25 abril 2025
Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X25 abril 2025 -
 Evade: Nextbbot chasing Codes in 202325 abril 2025
Evade: Nextbbot chasing Codes in 202325 abril 2025 -
 Evade Codes November 2023 - Pillar Of Gaming25 abril 2025
Evade Codes November 2023 - Pillar Of Gaming25 abril 2025 -
 All Evade Codes For November 2023 - GameRiv25 abril 2025
All Evade Codes For November 2023 - GameRiv25 abril 2025 -
Swarajya on LinkedIn: “Academic Freedom” To Evade Accountability?25 abril 2025
-
 Asad Asad: Engage and Evade: How Latino Immigrant Families Manage25 abril 2025
Asad Asad: Engage and Evade: How Latino Immigrant Families Manage25 abril 2025 -
 College Presidents Under Fire After Dodging Questions About25 abril 2025
College Presidents Under Fire After Dodging Questions About25 abril 2025 -
 20% Off Evade PROMO CODE, COUPONS October 202325 abril 2025
20% Off Evade PROMO CODE, COUPONS October 202325 abril 2025
você pode gostar
-
 Roblox on PS4 and PS525 abril 2025
Roblox on PS4 and PS525 abril 2025 -
![Super Figure Action [JoJolion] -JoJo`s Bizarre Adventure Part 8- [Soft & Wet] (Completed) - HobbySearch Anime Robot/SFX Store](https://www.1999.co.jp/itbig85/10851337.jpg) Super Figure Action [JoJolion] -JoJo`s Bizarre Adventure Part 8- [Soft & Wet] (Completed) - HobbySearch Anime Robot/SFX Store25 abril 2025
Super Figure Action [JoJolion] -JoJo`s Bizarre Adventure Part 8- [Soft & Wet] (Completed) - HobbySearch Anime Robot/SFX Store25 abril 2025 -
 Home-schooler clinches bee by spelling 'cruciferous25 abril 2025
Home-schooler clinches bee by spelling 'cruciferous25 abril 2025 -
 PHONEKY - Asta Black Clover HD Wallpapers25 abril 2025
PHONEKY - Asta Black Clover HD Wallpapers25 abril 2025 -
 AI generated Ambush (Roblox Doors) by MemeHoovy on DeviantArt25 abril 2025
AI generated Ambush (Roblox Doors) by MemeHoovy on DeviantArt25 abril 2025 -
 Arquivo Corte - Kit Digital Luluca Games-cod-55525 abril 2025
Arquivo Corte - Kit Digital Luluca Games-cod-55525 abril 2025 -
 Piano Music Game - APK Download for Android25 abril 2025
Piano Music Game - APK Download for Android25 abril 2025 -
Crunchyroll.pt - ✨ NOVO EPISÓDIO DUBLADO DISPONÍVEL ✨ Tokyo Revengers #19 Assista25 abril 2025
-
 Menina de 12 anos está desaparecida em Ivaí. - Rádio Copas Verdes25 abril 2025
Menina de 12 anos está desaparecida em Ivaí. - Rádio Copas Verdes25 abril 2025 -
 Jogo de cozinha em crochê kit 3 peças (Modelo: Flor Bordada) - Variedades Santos - Kit Capas para Cozinha - Magazine Luiza25 abril 2025
Jogo de cozinha em crochê kit 3 peças (Modelo: Flor Bordada) - Variedades Santos - Kit Capas para Cozinha - Magazine Luiza25 abril 2025


