Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Last updated 10 abril 2025
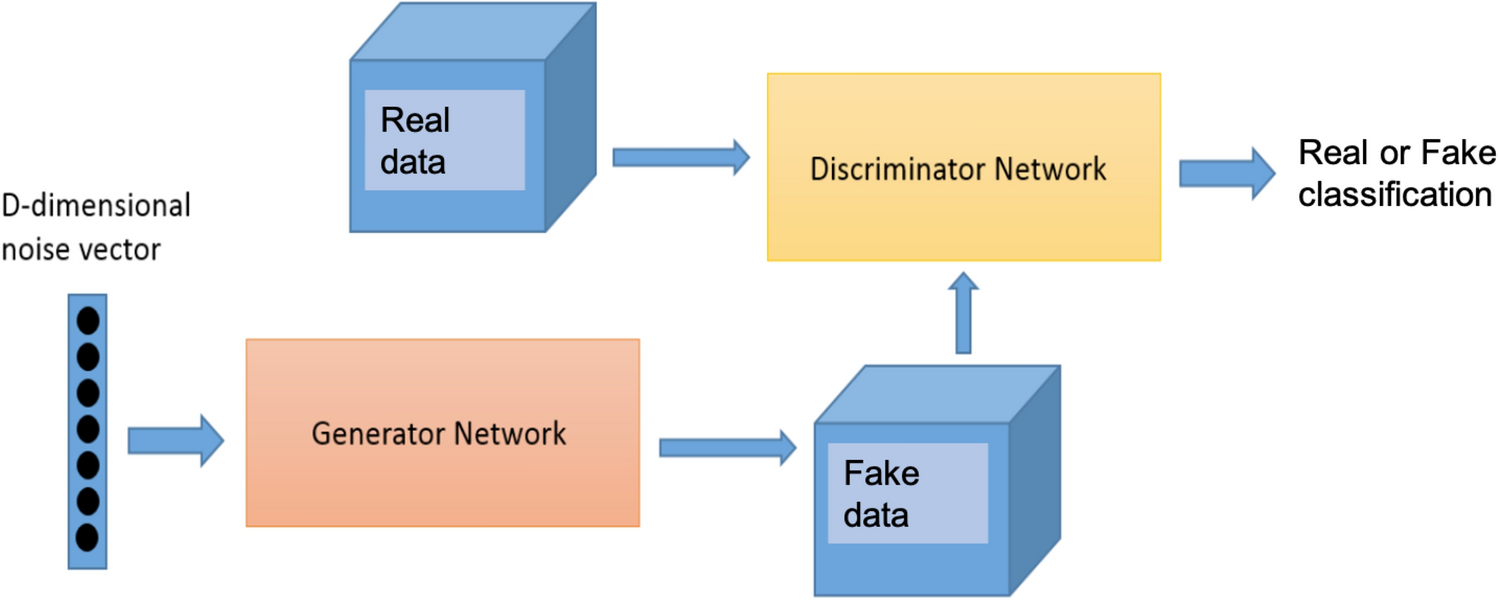
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks

A Comprehensive Survey of Recent Internet Measurement Techniques for Cyber Security - ScienceDirect
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity

A mining multitool - vulnerability database
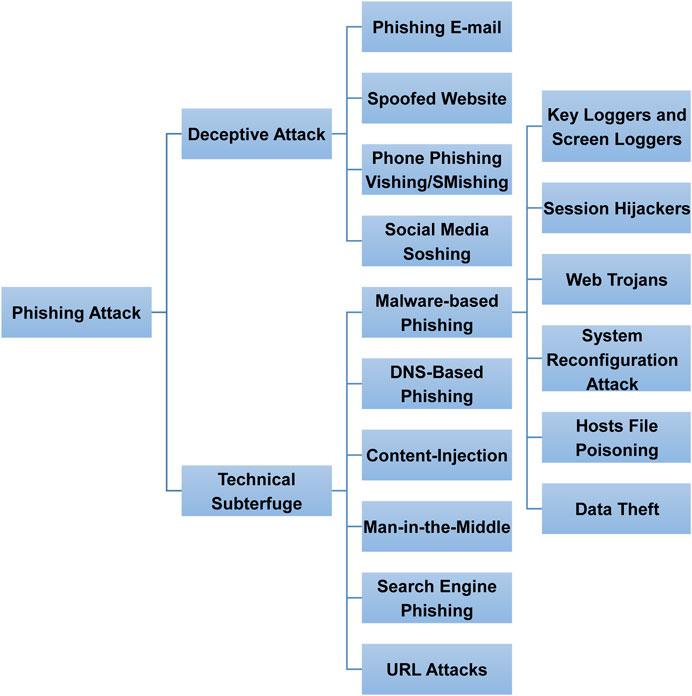
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

A Comprehensive Survey of Recent Internet Measurement Techniques for Cyber Security - ScienceDirect

Deep Learning for Zero-day Malware Detection and Classification: A Survey

PDF) Survey on the Usage of Machine Learning Techniques for Malware Analysis

A Survey of Binary Code Fingerprinting Approaches: Taxonomy, Methodologies, and Features

PDF) Malware Detection: Issues and Challenges
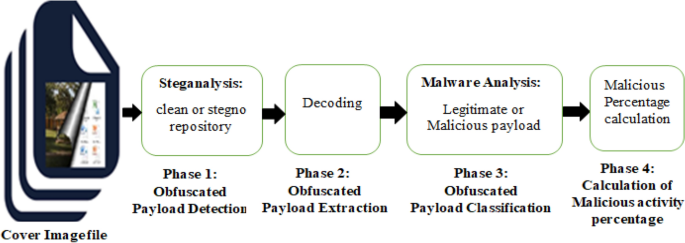
An ensemble-based stegware detection system for information hiding malware attacks

PDF) Dynamic malware detection and phylogeny analysis using process mining
Recomendado para você
-
 Do Free Robux Generators work?10 abril 2025
Do Free Robux Generators work?10 abril 2025 -
200%-FREE!!~ROBLOX ROBUX-GENERATOR UPDATES 2023-202410 abril 2025
-
SURE-WORKS))**FREE ROBUX GENERATOR FOR ROBUX 2022 WEEKLY UPDATES10 abril 2025
-
 unused-robux (ROBUX GENERATOR FREE ROBLIX NEW CODES) - Replit10 abril 2025
unused-robux (ROBUX GENERATOR FREE ROBLIX NEW CODES) - Replit10 abril 2025 -
 0eg22aa4Bj9VK5WlvWe7o.jpg10 abril 2025
0eg22aa4Bj9VK5WlvWe7o.jpg10 abril 2025 -
 Pamela Rowles on X: Robux Generator and Legit Ways to Earn Free10 abril 2025
Pamela Rowles on X: Robux Generator and Legit Ways to Earn Free10 abril 2025 -
 Hiperblox.org Free Robux Generator 202310 abril 2025
Hiperblox.org Free Robux Generator 202310 abril 2025 -
FREE ROBUX 2022 ROBLOX FREE ROBUX GENERATOR UPDATED - Collection10 abril 2025
-
 Kids_Fave) Free Robux Generator 2022 Get 500K Free Robux Instantly { D10 abril 2025
Kids_Fave) Free Robux Generator 2022 Get 500K Free Robux Instantly { D10 abril 2025 👇👇Click in the link bellow 👇👇 Roblox gifts, Gift card giveaway, Xbox gift card10 abril 2025você pode gostar
👇👇Click in the link bellow 👇👇 Roblox gifts, Gift card giveaway, Xbox gift card10 abril 2025você pode gostar-
Recent Cisco 500-210 Exam Questions PDF Version [2023]10 abril 2025
-
 royale high halo answers 2023 adventure by E_melxa|TikTok Search10 abril 2025
royale high halo answers 2023 adventure by E_melxa|TikTok Search10 abril 2025 -
 FNF vs Baldi's Basics in Funkin Mod - Play Online Free10 abril 2025
FNF vs Baldi's Basics in Funkin Mod - Play Online Free10 abril 2025 -
 MTGNexus - Hollow Ichigo, Vasto Lorde10 abril 2025
MTGNexus - Hollow Ichigo, Vasto Lorde10 abril 2025 -
 Skibidi Toilet GMOD para Android - Download10 abril 2025
Skibidi Toilet GMOD para Android - Download10 abril 2025 -
 FINAL FANTASY Pixel Remaster series on PS4 and Nintendo Switch10 abril 2025
FINAL FANTASY Pixel Remaster series on PS4 and Nintendo Switch10 abril 2025 -
 The Lost Bastille - DarkSouls II Wiki10 abril 2025
The Lost Bastille - DarkSouls II Wiki10 abril 2025 -
 NVIDIA GeForce RTX 4060 Ti Founders Edition Review - PC Perspective10 abril 2025
NVIDIA GeForce RTX 4060 Ti Founders Edition Review - PC Perspective10 abril 2025 -
 Peças de xadrez ícones de linha fina rei rainha bispo gralha cavaleiro peão – Artofit10 abril 2025
Peças de xadrez ícones de linha fina rei rainha bispo gralha cavaleiro peão – Artofit10 abril 2025 -
 Disney Parks Mickey and Friends Pirate Ship Deluxe Play Set New10 abril 2025
Disney Parks Mickey and Friends Pirate Ship Deluxe Play Set New10 abril 2025
© 2014-2025 progresstn.com. All rights reserved.

![Recent Cisco 500-210 Exam Questions PDF Version [2023]](https://media.licdn.com/dms/image/D4D12AQEaxtsp3YJv4w/article-cover_image-shrink_600_2000/0/1689924865615?e=2147483647&v=beta&t=dxk4XIIW9PyH9yb3IwwyFPB-Fe9ypzogihO3DFKrlQw)