How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 15 abril 2025
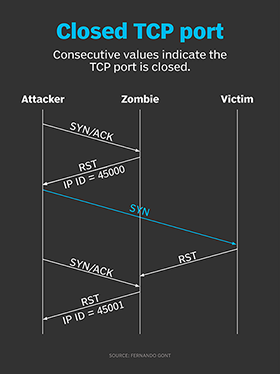
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
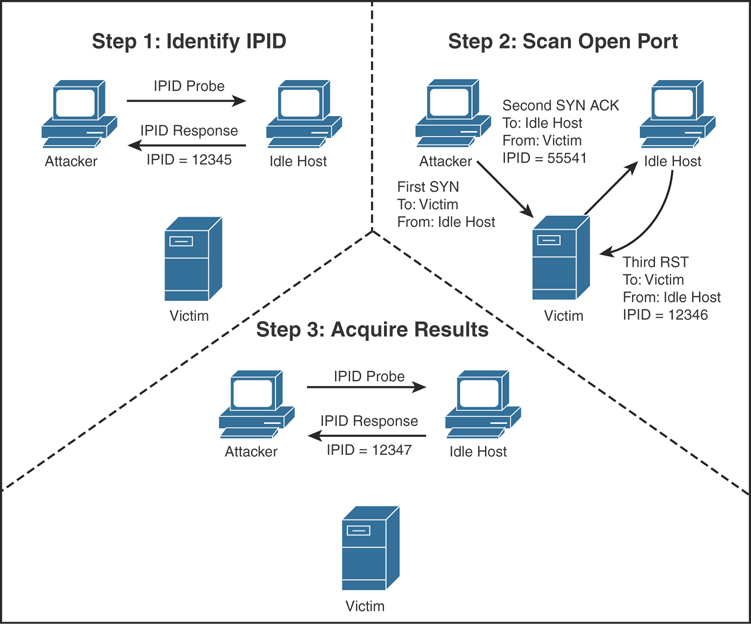
Scanning, Footprinting, Reconnaissance, and Scanning

What Is A Port Scan? How To Prevent Port Scan Attacks?
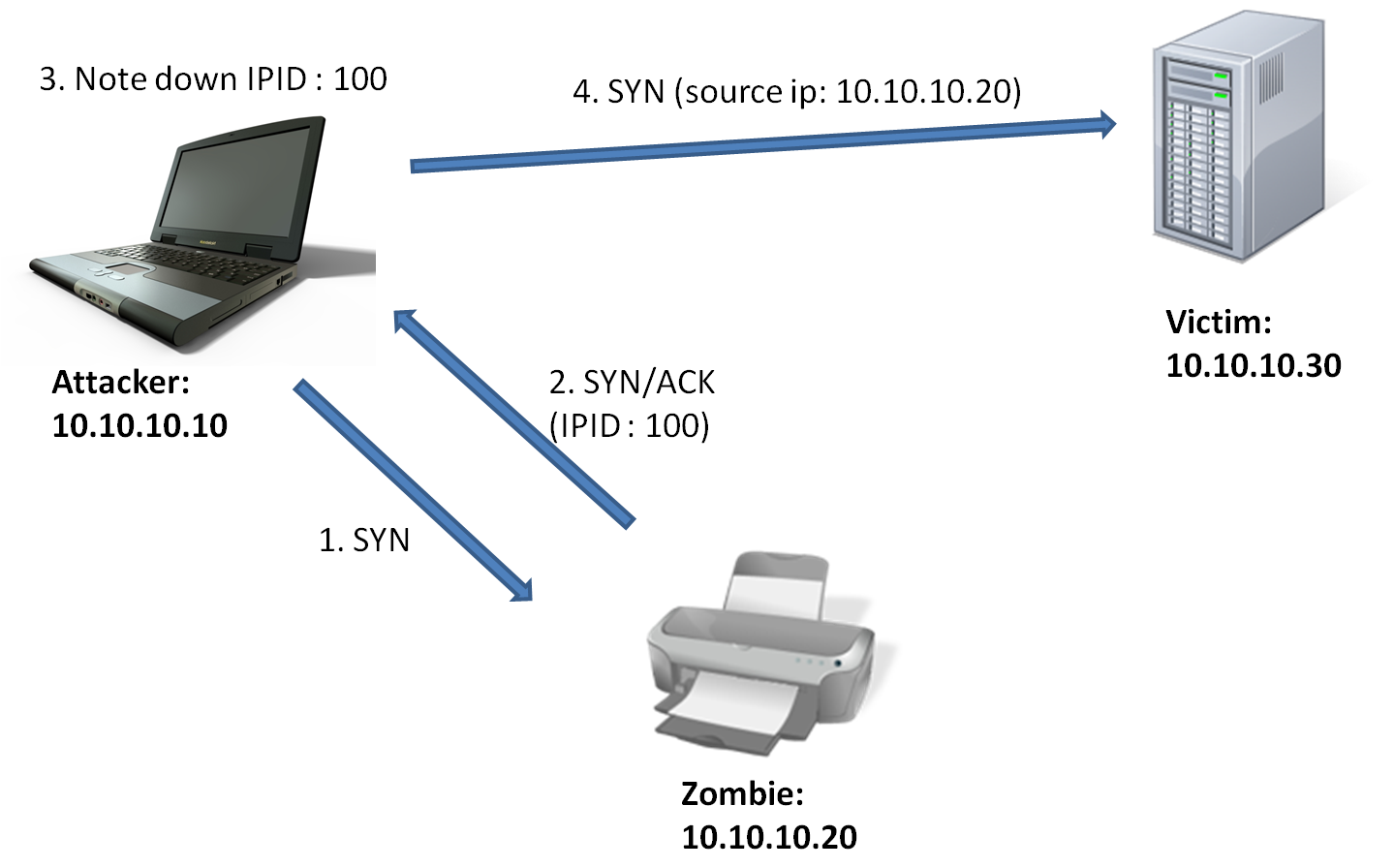
Vipul Chaskar's Blog: How does idle scan work?
Port Scanning based Attacks

Port Scan in Ethical Hacking - GeeksforGeeks

Port Scanning: A Comprehensive Guide for Safeguarding Cyberspace

Port Scanning - an overview

A Complete Guide to Nmap, Nmap Tutorial
What is a Cyber Attack? Definition and Related FAQs
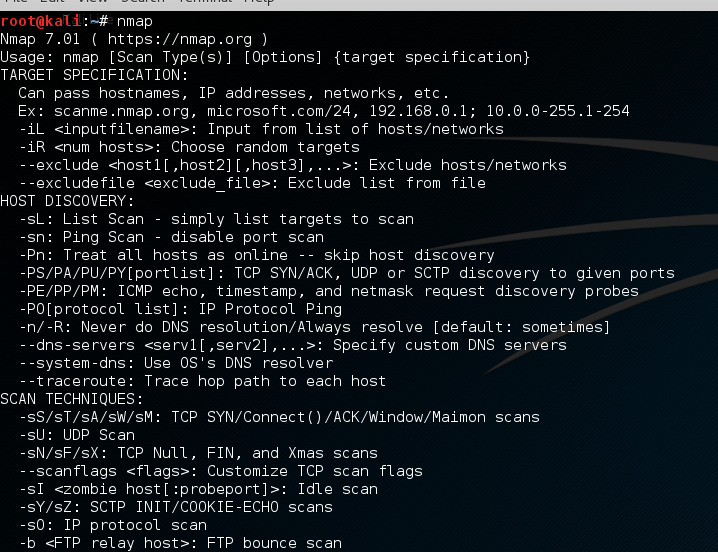
Applied Network Security

The Ultimate Guide to Port Scanning using Nmap
Recomendado para você
-
 What does your IP address say about you? - CNET15 abril 2025
What does your IP address say about you? - CNET15 abril 2025 -
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack15 abril 2025
-
 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman15 abril 2025
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman15 abril 2025 -
Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly15 abril 2025
-
 What Is A Port Scan? How To Prevent Port Scan Attacks?15 abril 2025
What Is A Port Scan? How To Prevent Port Scan Attacks?15 abril 2025 -
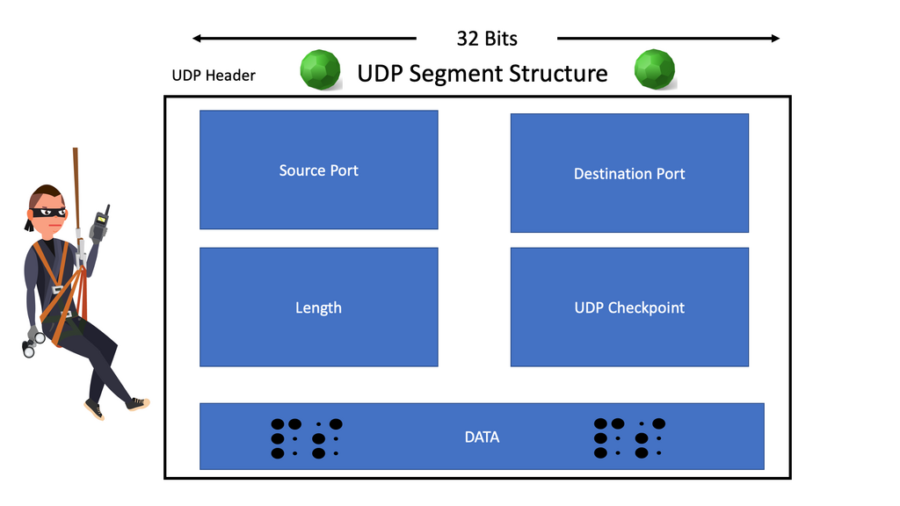 UDP Scan15 abril 2025
UDP Scan15 abril 2025 -
 How To Use Tor With Opera Web Browser (With Polipo) For Beginners15 abril 2025
How To Use Tor With Opera Web Browser (With Polipo) For Beginners15 abril 2025 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager15 abril 2025
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager15 abril 2025 -
 PPT - Safe Browsing PowerPoint Presentation, free download - ID:549326715 abril 2025
PPT - Safe Browsing PowerPoint Presentation, free download - ID:549326715 abril 2025 -
 PoC Guide: Citrix Secure Internet Access with Citrix SD-WAN15 abril 2025
PoC Guide: Citrix Secure Internet Access with Citrix SD-WAN15 abril 2025
você pode gostar
-
 My Tiny Senpai premieres this summer - Niche Gamer15 abril 2025
My Tiny Senpai premieres this summer - Niche Gamer15 abril 2025 -
 Nós avisamos sobre o escândalo da Blaze; conheça uma forma legítima e fácil de ganhar até R$ 118 por dia - Seu Dinheiro15 abril 2025
Nós avisamos sobre o escândalo da Blaze; conheça uma forma legítima e fácil de ganhar até R$ 118 por dia - Seu Dinheiro15 abril 2025 -
 Ketanji Brown Jackson to serve on the U.S. Supreme Court15 abril 2025
Ketanji Brown Jackson to serve on the U.S. Supreme Court15 abril 2025 -
 Como PERSONALIZAR a tape do seu skate de dedo ?15 abril 2025
Como PERSONALIZAR a tape do seu skate de dedo ?15 abril 2025 -
 86 – Eighty Six Episode 1 and 2 Review – Otaku Central15 abril 2025
86 – Eighty Six Episode 1 and 2 Review – Otaku Central15 abril 2025 -
 Cartoon Cactus Vector PNG Images, Cactus Green Cartoon Cactus15 abril 2025
Cartoon Cactus Vector PNG Images, Cactus Green Cartoon Cactus15 abril 2025 -
 Gran Turismo 6 maxed out Ford Ka on Nürburgring (just for laughs ;D)15 abril 2025
Gran Turismo 6 maxed out Ford Ka on Nürburgring (just for laughs ;D)15 abril 2025 -
 Minecraft: Redstone Logic Gates Explained15 abril 2025
Minecraft: Redstone Logic Gates Explained15 abril 2025 -
![Pre-Order] FINAL FANTASY X PLAY ARTS KAI Action Figures, NEWS, FINAL FANTASY PORTAL SITE](https://cache-na.finalfantasy.com/uploads/content/file/2023/08/25/17106/230825_ffxfigure_9.jpg) Pre-Order] FINAL FANTASY X PLAY ARTS KAI Action Figures, NEWS, FINAL FANTASY PORTAL SITE15 abril 2025
Pre-Order] FINAL FANTASY X PLAY ARTS KAI Action Figures, NEWS, FINAL FANTASY PORTAL SITE15 abril 2025 -
 Pino de esmalte offline do cacto de trex nenhum broche t-rex do botão do dinossauro do jogo da internet - AliExpress15 abril 2025
Pino de esmalte offline do cacto de trex nenhum broche t-rex do botão do dinossauro do jogo da internet - AliExpress15 abril 2025
![Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=2958303717738978)