Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 17 abril 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Patching Perforce perforations: Critical RCE vulnerability discovered in Perforce Helix Core Server

Microsoft Defender Attack Surface Reduction recommendations

Code of Ethics for Government Services Poster
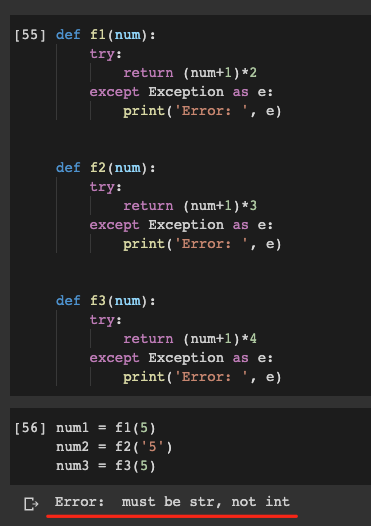
Do Not Abuse Try Except In Python, by Christopher Tao

Hackers Exploit Windows Policy Loophole to Forge Kernel-Mode Driver Signatures
Exploitation Protections From Old To Bleeding Edge pt 1, by Edward Amaral Toledano, stolabs

How to Fix a Toxic Culture

Evading Windows Defender with 1 Byte Change - Red Team Notes
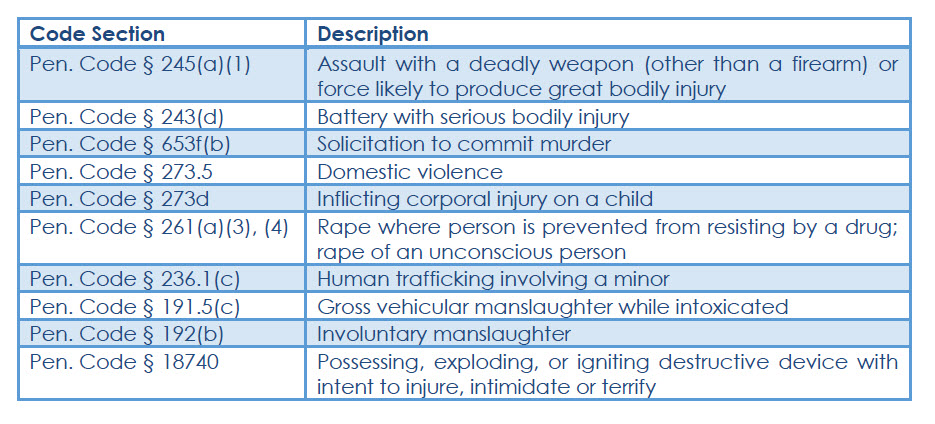
INTRODUCTION, DEFINITION, AND HISTORY OF NONVIOLENT PAROLE REVIEW - Board of Parole Hearings
Abusing Jenkins Groovy Script Console to get Shell, by Nishant Sharma
We believe urinary health should be proactive, but life happens. That’s why we created the UTI Emergency Kit. , This 3-in-1 bundle contains everything

UTI Emergency Kit
Recomendado para você
-
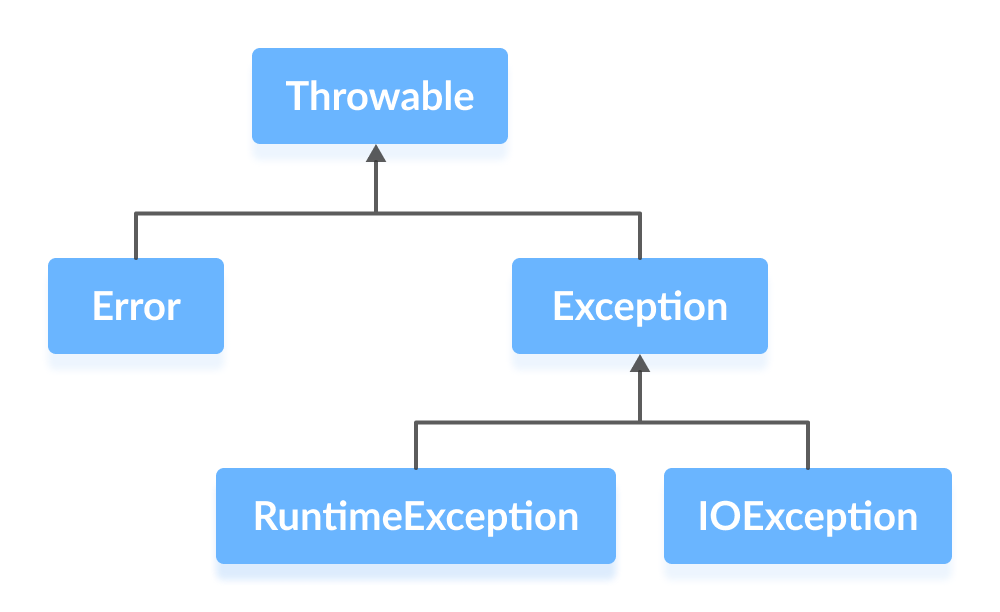 Java Exceptions17 abril 2025
Java Exceptions17 abril 2025 -
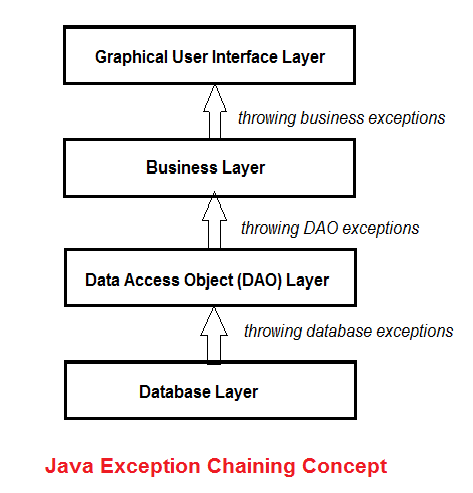 Understanding Java Exception Chaining with Code Examples17 abril 2025
Understanding Java Exception Chaining with Code Examples17 abril 2025 -
 Python Exceptions: The Ultimate Beginner's Guide (with Examples)17 abril 2025
Python Exceptions: The Ultimate Beginner's Guide (with Examples)17 abril 2025 -
 Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow17 abril 2025
Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow17 abril 2025 -
 Implement Custom Exceptions in Java: Why, When and How17 abril 2025
Implement Custom Exceptions in Java: Why, When and How17 abril 2025 -
 Abusing Exceptions for Code Execution, Part 217 abril 2025
Abusing Exceptions for Code Execution, Part 217 abril 2025 -
 What is the built in base class to handle all exceptions in Java - Stack Overflow17 abril 2025
What is the built in base class to handle all exceptions in Java - Stack Overflow17 abril 2025 -
 Exception Handling Best Practices - AnAr Solutions17 abril 2025
Exception Handling Best Practices - AnAr Solutions17 abril 2025 -
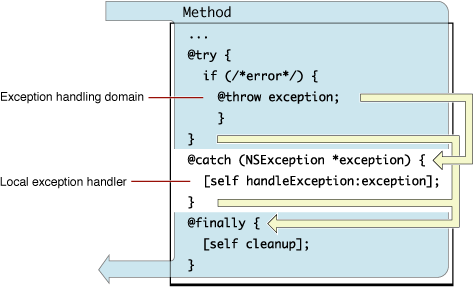 Handling Exceptions17 abril 2025
Handling Exceptions17 abril 2025 -
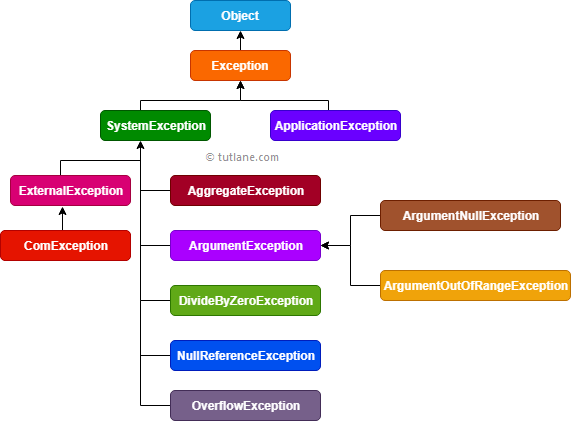 Visual Basic Exception - Tutlane17 abril 2025
Visual Basic Exception - Tutlane17 abril 2025
você pode gostar
-
 My publications - Inglês - Página 264-265 - Created with Publitas.com17 abril 2025
My publications - Inglês - Página 264-265 - Created with Publitas.com17 abril 2025 -
 Purble Place - Download17 abril 2025
Purble Place - Download17 abril 2025 -
 Assistir Tokyo Ghoul 2 Dublado Episodio 10 Online17 abril 2025
Assistir Tokyo Ghoul 2 Dublado Episodio 10 Online17 abril 2025 -
 Crocs infantil shrek Black Friday Casas Bahia17 abril 2025
Crocs infantil shrek Black Friday Casas Bahia17 abril 2025 -
A thumbnail for a N the JoJo game video I'm making.17 abril 2025
-
Hot Wheels Dragon Blast Launching Playset17 abril 2025
-
 Hands on OnePlus Concept One na CES 2020 – TecMundo17 abril 2025
Hands on OnePlus Concept One na CES 2020 – TecMundo17 abril 2025 -
 Sakura haruno Animes famosos, Desenhando roupas de anime, Personagens de anime17 abril 2025
Sakura haruno Animes famosos, Desenhando roupas de anime, Personagens de anime17 abril 2025 -
 November 2022 Sneak Peek17 abril 2025
November 2022 Sneak Peek17 abril 2025 -
 Quanto vale o patrimônio líquido do Dr. Nowzaradan? – - Nº 1 de estrelas oficiais, rede de negócios e pessoas, Wiki, história de sucesso, biografia e citações17 abril 2025
Quanto vale o patrimônio líquido do Dr. Nowzaradan? – - Nº 1 de estrelas oficiais, rede de negócios e pessoas, Wiki, história de sucesso, biografia e citações17 abril 2025