Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 15 abril 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

Defending CI/CD Environments - The NSA/CISA Way
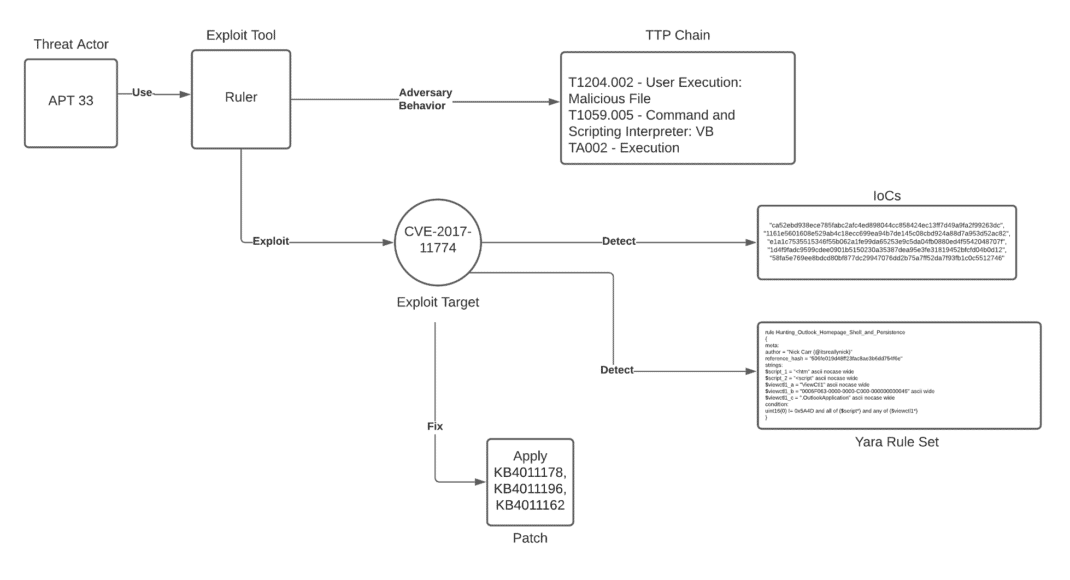
Unpacking the CVEs in the FireEye Breach - Start Here First
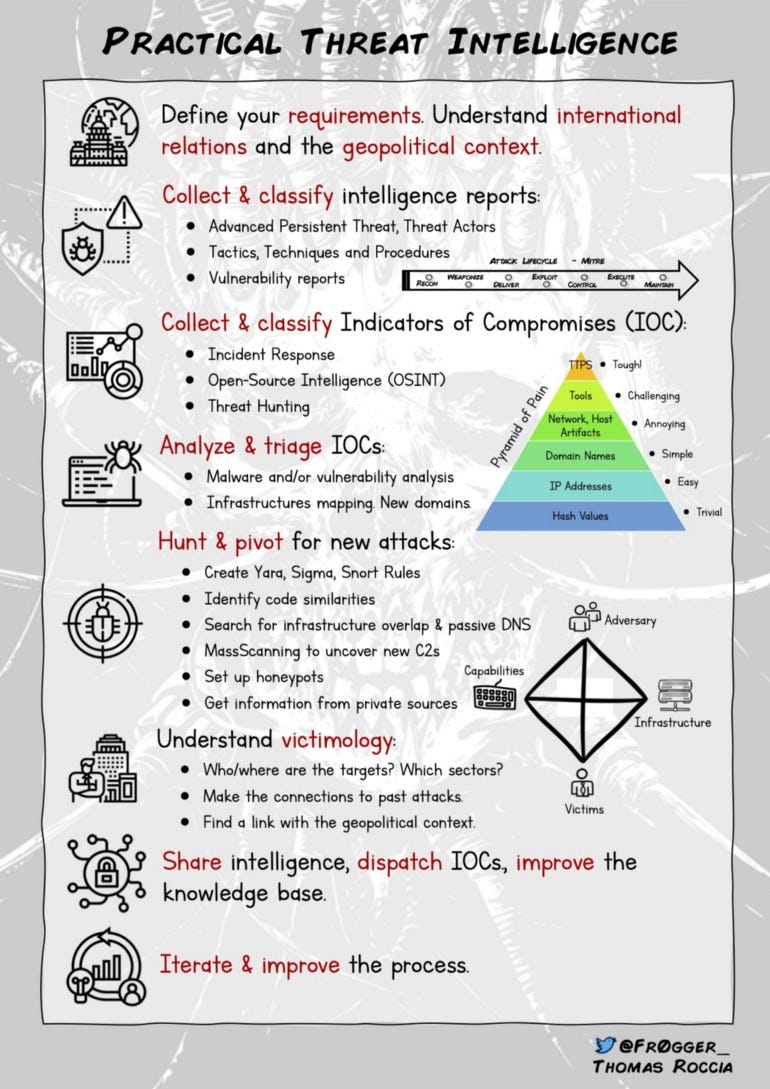
Security Infographics. I often do infographics to share…
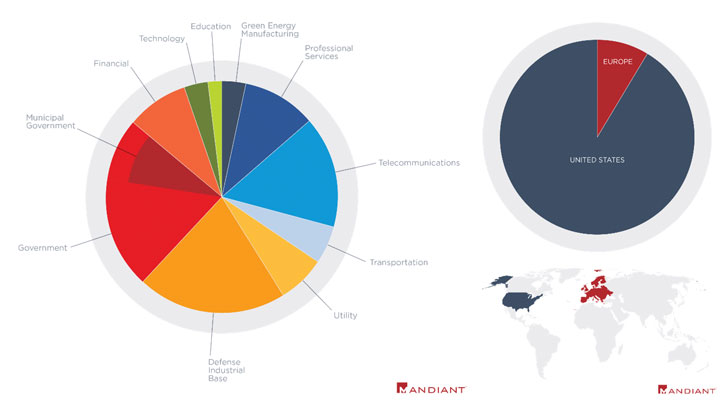
Chinese Cyber Espionage Hackers Continue to Target Pulse Secure

TTPs Within Cyber Threat Intelligence

Tactics, Techniques, and Procedures (TTPs)

FireEye offers proactive OT environment protection with latest
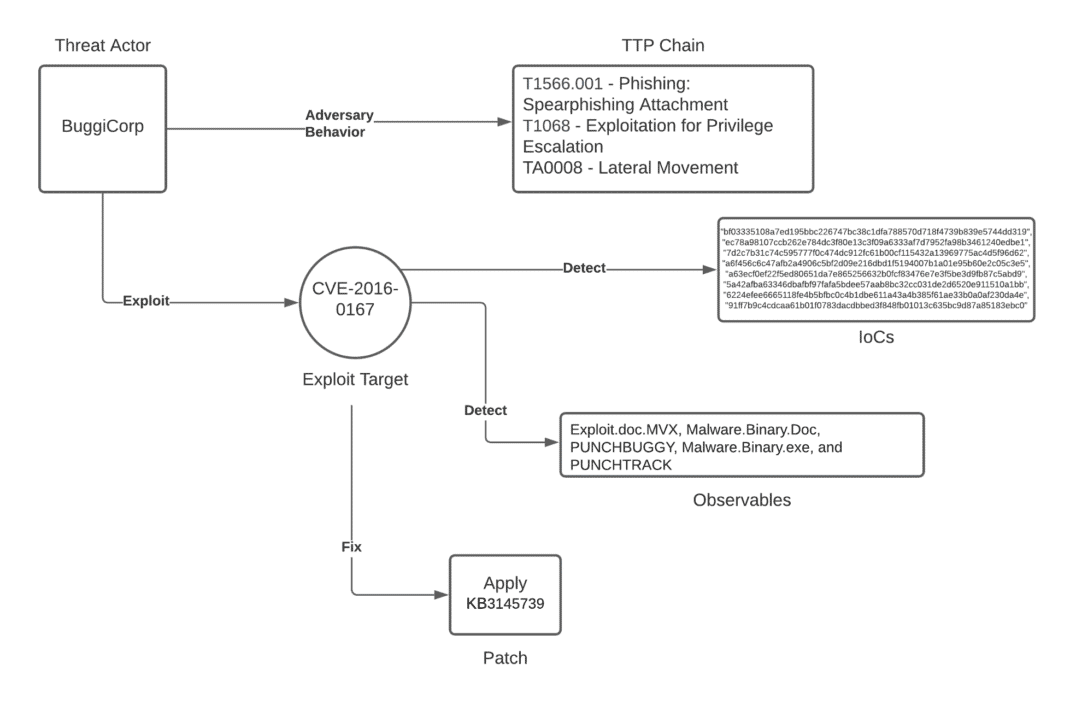
Unpacking the CVEs in the FireEye Breach - Start Here First
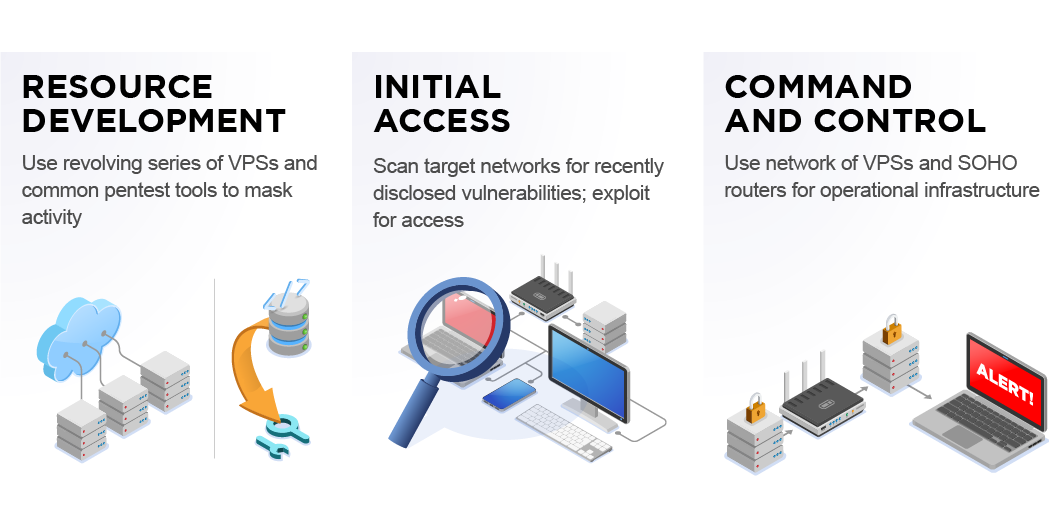
Chinese State-Sponsored Cyber Operations: Observed TTPs
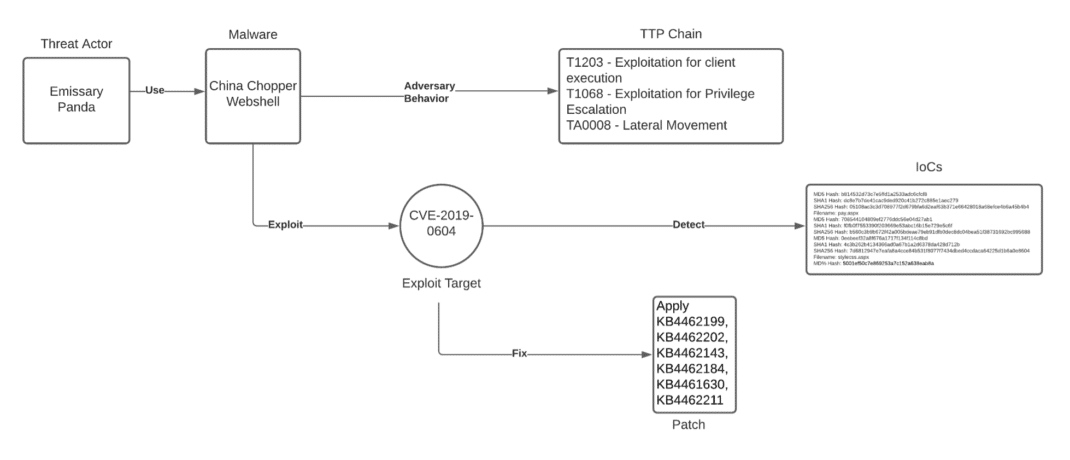
Unpacking the CVEs in the FireEye Breach - Start Here First

Threat Intelligence Briefing: Adversarial Motives, Intents and
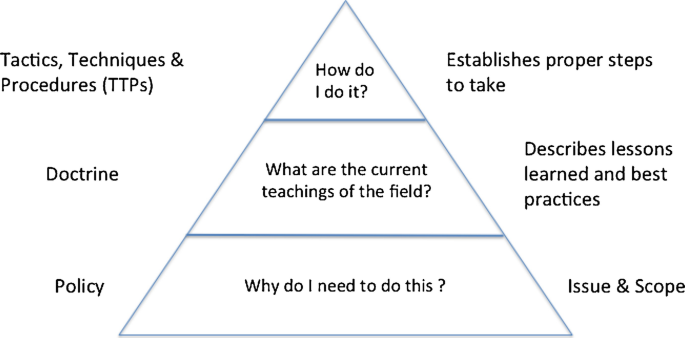
Cyber Policy, Doctrine, and Tactics, Techniques, and Procedures

FireEye Reveals How SolarWinds Hackers Bypassed the Defenses
Recomendado para você
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!15 abril 2025
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!15 abril 2025 -
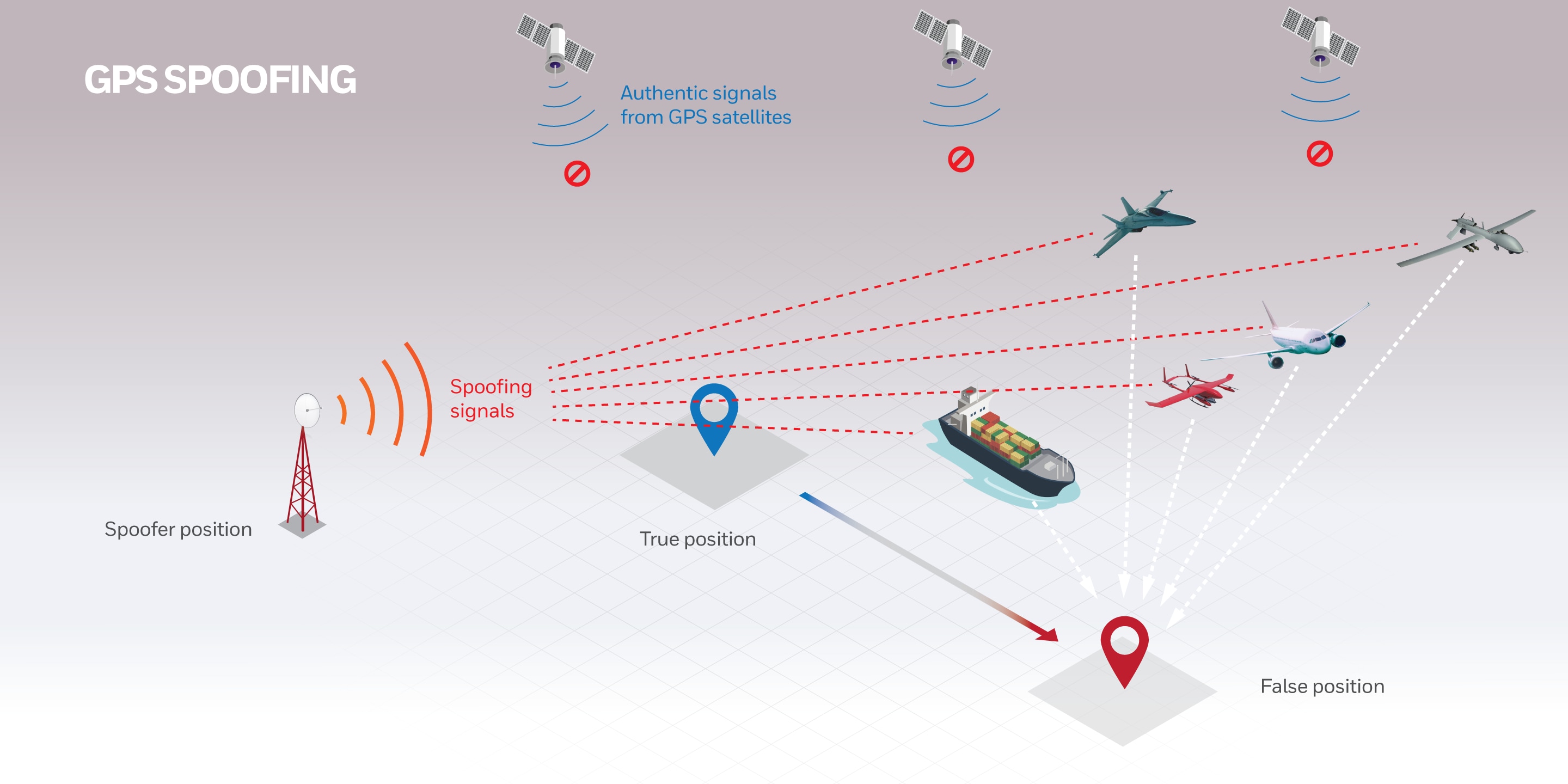 No GPS, No Problem: Honeywell Invents, Demonstrates Military-Grade15 abril 2025
No GPS, No Problem: Honeywell Invents, Demonstrates Military-Grade15 abril 2025 -
 YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub15 abril 2025
YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub15 abril 2025 -
 What is Spoofing? - FFCCU Blog15 abril 2025
What is Spoofing? - FFCCU Blog15 abril 2025 -
 CAIDA Catalog Search - A Collection of Scientific Research on the15 abril 2025
CAIDA Catalog Search - A Collection of Scientific Research on the15 abril 2025 -
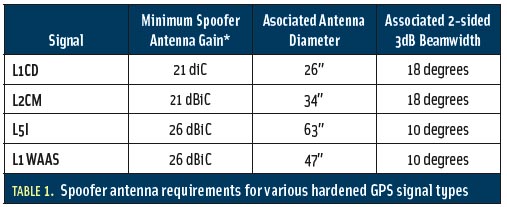 Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation15 abril 2025
Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation15 abril 2025 -
 James the Red Engine, Movie Spoof Films Wikia15 abril 2025
James the Red Engine, Movie Spoof Films Wikia15 abril 2025 -
 Nobody's Fool: Spoofing Detection in a High-Precision Receiver15 abril 2025
Nobody's Fool: Spoofing Detection in a High-Precision Receiver15 abril 2025 -
Location Guard15 abril 2025
-
 11 Types of Spoofing Attacks Every Security Professional Should15 abril 2025
11 Types of Spoofing Attacks Every Security Professional Should15 abril 2025
você pode gostar
-
Fórum Dublanet15 abril 2025
-
Jogo Disney Princess Enchanted Journey - Playstation 2 - Disney15 abril 2025
-
 Boneca Anna Frozen 2 Disney - 30 Cm - Vestido Encantado15 abril 2025
Boneca Anna Frozen 2 Disney - 30 Cm - Vestido Encantado15 abril 2025 -
 lost-ark-closed-beta-world-map15 abril 2025
lost-ark-closed-beta-world-map15 abril 2025 -
 Karabakh President Samvel Shahramanyan is already in Armenia, Artsakh MP Davit Galstyan says15 abril 2025
Karabakh President Samvel Shahramanyan is already in Armenia, Artsakh MP Davit Galstyan says15 abril 2025 -
High School matemática ciências - Recursos de ensino15 abril 2025
-
 Bridge of Khazad-dum (LTC)15 abril 2025
Bridge of Khazad-dum (LTC)15 abril 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/23024846/GameCapture_2021_11_18_10_55_31.png) Elite Four & Champion Cynthia – Pokémon Brilliant Diamond & Shining Pearl guide - Polygon15 abril 2025
Elite Four & Champion Cynthia – Pokémon Brilliant Diamond & Shining Pearl guide - Polygon15 abril 2025 -
 Download do APK de FreeCell para Android15 abril 2025
Download do APK de FreeCell para Android15 abril 2025 -
 Dragon Ball Super: Ep. 97 - Senhoras e senhores, o Torneio de Poder começou!15 abril 2025
Dragon Ball Super: Ep. 97 - Senhoras e senhores, o Torneio de Poder começou!15 abril 2025